This Week in Matrix 2020-04-03
2020-04-03 — This Week in Matrix — Ben Parsons🔗Matrix Live 🎙
Featuring p2p, E2EE, FTUE, Open Tech Will Save Us and Mirage
🔗Dept of Status of Matrix 🌡
🔗Open Tech Will Save Us
Open Tech Will Save Us is a virtual meetup, taking the form of a monthly live video stream broadcasting on the second Wednesday of every month at 5pm UTC.
The first event will have speakers from Jitsi, IPFS and Matrix.
We'll cover the importance of preserving privacy and ways to keep your communications under control. Read more at https://matrix.org/open-tech-meetup/
🔗GSoC Student Applications closed
Google closed the door to applications on Tuesday, and we have an absolute bounty of proposals. More information will be shared when the announcements are made in a few weeks.
🔗Dept of Spec 📜
anoa said:
Here's your weekly spec update!
🔗MSC Status
Merged MSCs:
- No MSCs were merged this week
MSCs in Final Comment Period:
- No MSCs are currently in FCP
New MSCs:
Not much changing state this week as most people are focusing on implementation and existing MSCs.
🔗Spec Core Team
Next week the Spec Core Team is focusing on the same as last week: MSC2457 (password invalidation), MSC2454 (SSO UI Auth), and MSC2472 (Symmetric SSSS).
🔗Dept of Servers 🏢
🔗Dendrite / gomatrixserverlib
Neil Alexander offered:
Dendrite now has support for sending v2 invites, and partial support for receiving them
The typing server in Dendrite has now been renamed to a more general-purpose EDU server and support for sending/receiving typing notifications has been fixed
Room version v3 and v4 support in Dendrite is mostly finished, hopefully will be merged soon
A new version of the P2P demo was released yesterday with some fixes (more information and discussion in #p2p:matrix.org)
gomatrixserverlib now has new types and support for the new invite format, as used in the v2 endpoint
gomatrixserverlib has received some bugfixes, including with event ID generation and avoiding
nullin marshalled JSON forauth_eventsandprev_events
🔗Construct
Update from Jason:
End-to-end encryption support has landed in Construct. The server now supports cross-signing, secret storage, and key backups for clients. I'm pleased with how this all came together on schedule for the upcoming transition to e2ee by default for Matrix. If you haven't been paying attention in #construct:zemos.net last week full support for push-rules including efficient highlight-counting also landed. Next week Application Service support is scheduled.
Construct is quickly nearing complete coverage over the full breadth of the Matrix protocol, and the transition into release packaging is fast approaching. Construct is the C++ homeserver built for maximum performance with the lowest possible cost of ownership. If you're in need of a faster homeserver please show your support in #construct:zemos.net and tell all your friends to lend a hand today!
Thanks Tulir for relaying
🔗New Rust Homeserver
timo announced:
Hello! This week I worked on a Matrix homeserver written in Rust. Registering and logging in works already and I am currently adding support for sending events and inserting them into the event graph. I spent most of my time reading the Matrix specification to understand how this process works, because with federation (which I plan to add to my homeserver in the future) servers might disagree on which event was created first and there are strictly defined rules to resolve this. The Matrix homeserver uses the Ruma libraries as it's base and handles requests and responses using the Rocket crate. I use sled to store information as (key, value) pairs in a database. Most of these libraries are still experimental and I take this attitude myself by straying off from the reference implementations and changing algorithms in hopes of better performance. If you want to help, check out #rustmatrix:koesters.xyz.
🔗mautrix-asmux
Tulir offered:
mautrix-asmux wasn't made this week, but I haven't mentioned it on TWIM before. Basically, it acts as a proxy between appservices and the homeserver. The primary point is to make it possible to dynamically provision appservices.
The dynamically provisioned appservices connect to mautrix-asmux with individual access tokens, which asmux checks and then proxies the requests to Synapse with its own global access token. Synapse is only aware of one appservice, which will have a large user ID and alias namespace (e.g. everything starting with
_). In the other direction, mautrix-asmux maintains a room ID -> appservice mapping, which it uses to send incoming events to the correct appservice. As a side effect, mautrix-asmux implements MSC2190, which is needed for end-to-bridge encryption.
🔗📡 Sygnal 0.4.0
Half-Shot told us:
Hey, some non-bridge news from me. We've released Sygnal v0.4.0 which allows folks to use postgresql to store state rather than sqlite3.
...and then...
another release, https://github.com/matrix-org/sygnal/releases/tag/v0.4.1
🔗Synapse
Neil told us:
We continue on our performance drive. We’ll get Redis into production early next week replacing our home grown TCP based replication system. We also landed some SSO fixes for user interactive auth. Additionally we shipped a bug fix release in 1.12.3.
🔗Synapse Deployment 📥
🔗Kubernetes
Ananace offered:
Just bumped the K8s-optimized Synapse image to 1.12.1
🔗Docker-matrix
Mathijs told us:
The docker image for synapse v1.12.1rc1 is now on mvgorcum/docker-matrix:v1.12.1rc1
🔗Dept of Bridges 🌉
🔗mautrix-telegram
Tulir said:
mautrix-telegram now has experimental support for end-to-bridge encryption. It's intended for cases where you don't want the homeserver to have access to messages, e.g. user-hostable appservices. It's currently on the
e2bebranch and should be merged to master soon. You can find setup instructions on the wiki: https://github.com/tulir/mautrix-telegram/wiki/End‐to‐bridge-encryptionThe same feature will make its way to mautrix-facebook and mautrix-hangouts in the near future. After that, I'm going to start working on porting matrix-nio's crypto code to Go to bring end-to-bridge encryption to mautrix-whatsapp and possibly also general e2ee support for gomuks.
🔗New tooling for plumbing IRC rooms
Cos announced:
I got annoyed by how difficult plumbing IRC rooms is and wrote a simple Python script to do it more easily from command line. Also cleaning old rooms and chats in Riot is quite tedious so I added support for easily leaving rooms to the script. I decided to creatively call it matrixtools and created a github repo for it for others to enjoy. It's still in infancy but more features are already planned such as more IRC management stuff and creating tombstone events to point rooms to other rooms. The tool uses Python and matrix-nio library. Contributions welcome! https://github.com/vranki/matrixtools
🔗mx-puppet-bridge
mx-puppet-bridge is a general bridging library that supports (double)bridging and relays. The goal is to make it as easy as possible for others to bridge new third-party protocols to matrix. Support room Donate
sorunome said:
The bridge bot now sends read indicators for messages successfully delivered to the remote network - only supported on protocol implementations with event synchronising. 🦊
🔗mx-puppet-slack
Advanced relay support! Similar to the discord bridge, you can now make an advanced relay, where, if in relay mode, the messages from matrix users appear correctly with username+avatar on the slack side. This works for both classic slack apps and new slack apps, via the events API.
For that the underlying slack client connection had to be significantly re-written, which became its own repository.
🔗mx-puppet-skype
The skype puppet received a couple of bugfixes, so that it shouldn't need to be manually restarted every day anymore.
🔗mx-puppet-voipms
mx-puppet-voipms is a puppeting bridge for the SMS functionality provided by voip.ms. It is based on mx-puppet-bridge.
zoe reported:
Initial release of mx-puppet-voipms, a puppeting bridge for the voip.ms SMS api built on top of the amazing mx-puppet-bridge framework.
🔗🤙 node-jitsi
Half-Shot told us:
Hey folks! I've not posted a proper bridge update in a while, so let's go into another project that isn't a bridge. I've started working on a new project called node-jitsi, which will allow people to connect their services to Jitsi Meet conferences. It's designed to allow bridges to start bridging across actual calls into Matrix via Jitsi, but could really be used by any project which is Node.JS based and wants Jitsi call functionality. The goal is to keep the interface clean and simple, and do all of the heavy lifting (WebRTC negotiations, XMPP handling) itself.
Currently the project has just started, although progress should hopefully be swift! Come check us out in #node-jitsi:half-shot.uk and get chatting
🔗Dept of Clients 📱
🔗RiotX
valere reported:
Main focus in on getting cross-signing out (bootstrap will soon be merged)
But we also started efforts on database migration from Realm to SQLDelight!
🔗Develop Change log:
Features ✨:
Cross-Signing | Support SSSS secret sharing (#944)
Cross-Signing | Verify new session from existing session (#1134)
Improvements 🙌:
Verification DM / Handle concurrent .start after .ready (#794)
Cross-Signing | Update Shield Logic for DM (#963)
Cross-Signing | Complete security new session design update (#1135)
Bugfix 🐛:
Missing avatar/displayname after verification request message (#841)
Crypto | RiotX sometimes rotate the current device keys (#1170)
RiotX can't restore cross signing keys saved by web in SSSS (#1174)
🔗Nio for iOS
kilian said:
Nio for iOS has been getting some attention this week. Message display is now much better (visually grouped by sender) and I added some preliminary support for contextual event actions. For the time being emoji reactions and redactions have been implemented. (The context menu does trigger the best result of the visual flipping workaround in SwiftUI though 😅)
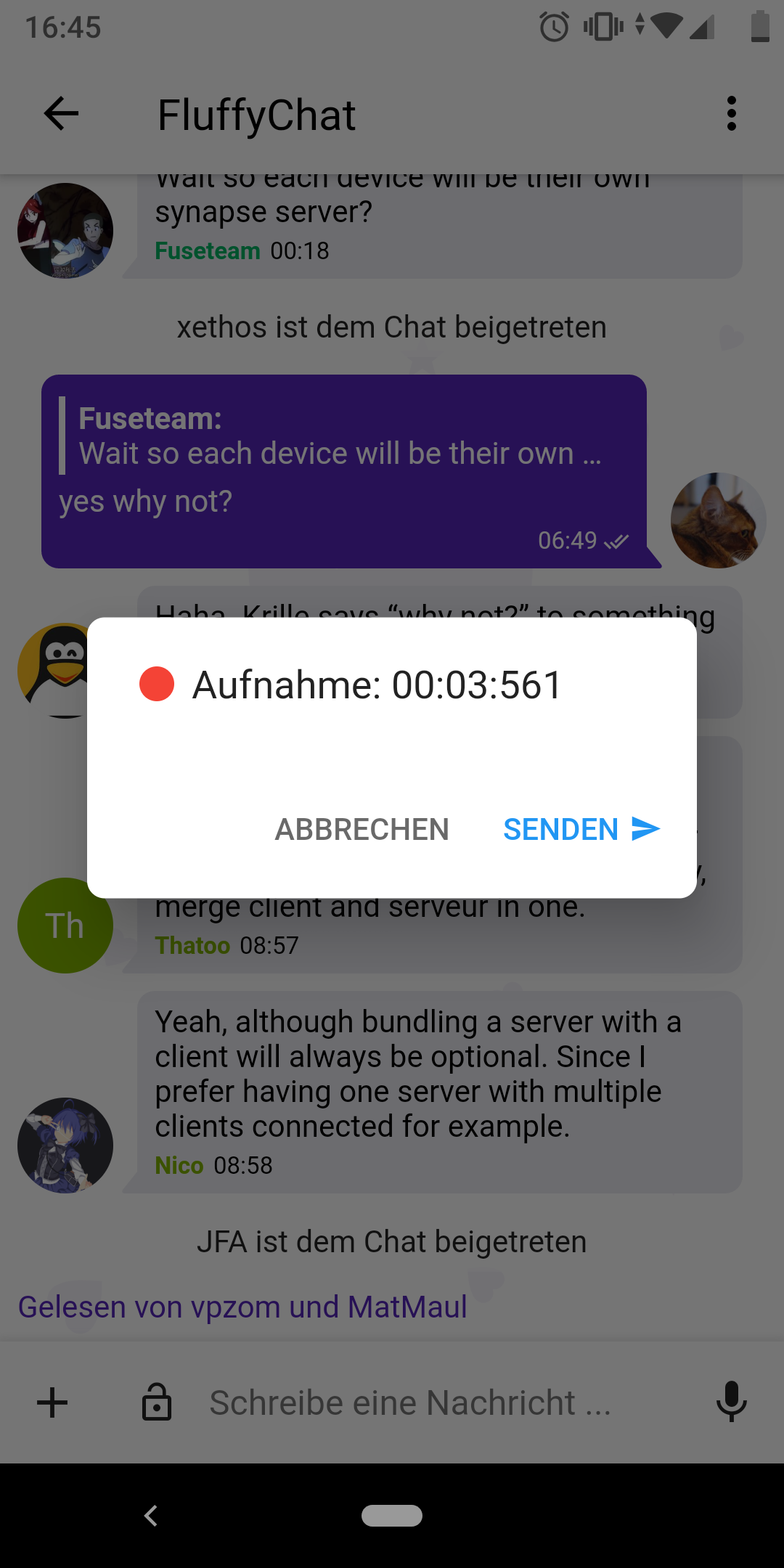
🔗What's new on the fluffy side?
krille told us:
FluffyChat 0.11.0 is now available in the F-Droid repo:
https://mtrnord.gitlab.io/fluffychat-flutter-fdroid/fdroid/repo/
🔗New features
Voice messages
New message bubble design
Share content with FluffyChat
🔗Changes:
- Use SnackBars instead of Toasts
🔗Fixes:
Minor fixes in the SDK
Loading dialog when sending files is displayed too long
Fixed device settings list
Fix a lazy loading bug
Improve app icon
The current version in the PlayStore is outdated. I need to write a privacy policy first and this can take some time. A TestFlight version for iOS is planned too but not yet ready. Here is a screenshot of the new voice messages feature:
🔗Quotient project
kitsune reported:
The Quotient project has made two "sustaining" releases this week, and then three^Wfour more to fix foolish mistakes - right on the Fools' Day! Long story short - if you're on Quaternion 0.0.9.4* (with any trailing letter) and, respectively, libQMatrixClient 0.5.x, make sure to upgrade to Quaternion 0.0.9.4e and libQMatrixClient 0.5.3.2 because, as of this writing, these are the latest and fixedest in the breed. Aside from many backend bugfixes (mostly described in release notes from 0.5.3), this refreshed pair can handle SSO and no more interferes with Pantalaimon in encrypted rooms. Further plans include scrapping the whole Quotient thing and switch to Python because it's so much easier. Just kidding :) the plans didn't change, Quotient 0.6 is the next milestone, and the backend for the next Quaternion release. And you won't need to wait another year for them, I promise.
🔗Mirage
miruka reported:
Mirage 0.4.3 was released today, AppImage and Flatpak included.
Some of the most notable changes:
Redactions support: individual or selected messages can now be removed from the context menu or using keyboard shortcuts
New shortcuts for inviting to, leaving or forgetting a room
Support for environment variables to specify config and user data folders
Fixed the crash after login for KDE users
🔗Riot Web
Ryan announced:
Riot Web 1.5.14 and 1.5.15 were released this week with a simpler Jitsi integration, new keyboard shortcuts (along with shortcut help via
Cmd / Ctrl+/), and layout performance fixes. 1.5.14 has a security issue with the Jitsi widget wrapper, so please remove any copies of 1.5.14 if you installed it. Lots of cross-signing polish work continues as we get closer to release.
🔗Riot-iOS
Manu announced:
We made a hot fix release (0.10.5) this week. Cross-signing work is still progressing well. We will run much more tests next week with other Riots to finish the feature.
Ismail, who joined the team mid-week 🥳🎉, has started to do some maintenance work required by iOS 13 SDK.
🔗Dept of SDKs and Frameworks 🧰
🔗ruma
jplatte announced:
Through a steady increase in demand thanks to GSoC, matrix-rust-sdk and timokoesters' homeserver, our foundational crates are receiving more attention than ever before, resulting in the following releases last week:
- This release contains a change that allows endpoint definitions to have an associated error type
This release once again gets us closer to r0.6.0 compatibility
We now use the standard libraries
Durationtype for a few things including the/syncrequest'stimeoutparameterWe now have an
Errortype that error responses from the homeserver will be deserialized into
🔗New PHP library
a_v_p announced:
Hello! I'm working on a PHP library (GPL v3.0+) that allows to communicate with a Matrix instance. Currently the library allows to create users, rooms, login to the Matrix server and send messages, although more work needs to be done: https://github.com/artyom-poptsov/matrix-php
I created the library due to my own needs, but probably it will be of some interest for others.
Apparently the author has a need for Matrix-Moodle integration, sounds interesting! An update! Late breaking:
I've updated Matrix-PHP, now there's documentation in
README.mdon how to use the library. If anyone wants to use it/contribute, this should make the things easier.There's no release yet though. But for now, the library is capable of:
- creating users with on the servers where registration is disabled;
- changing users passwords (by users themselves or by admins);
- logging in to the server using
m.login.passwordmethod;- sending text messages to rooms;
- checking if a username is available for registration on a server (only for admins.)
🔗Dept of Ops 🛠
🔗matrix-docker-ansible-deploy
Slavi said:
A few interesting matrix-docker-ansible-deploy updates this week:
Thanks to Christian Lupus's efforts, the playbook now supports installing to an Archlinux server.
Thanks to Marcel Partap's efforts, the mxisd identity server, which has been deprecated for a long time, has finally been replaced by ma1sd.
🔗dacruz21/matrix-chart
Typo Kign reported:
I've just released v1.0 of my Matrix helm chart, to help deploy a complete homeserver stack in Kubernetes. Partially inspired by spantaleev's wonderful ansible playbook, dacruz21/matrix-chart aims to be an all-in-one installation of Synapse, Riot, bridges, and other services. It includes a number of Kubernetes security and scalability features, and is ideal for anyone running a large homeserver, or a homeserver in a corporate environment where security is paramount.
More details at https://github.com/dacruz21/matrix-chart, and visit #matrix-chart:typokign.com for any questions or support.
🔗Dept of Bots 🤖
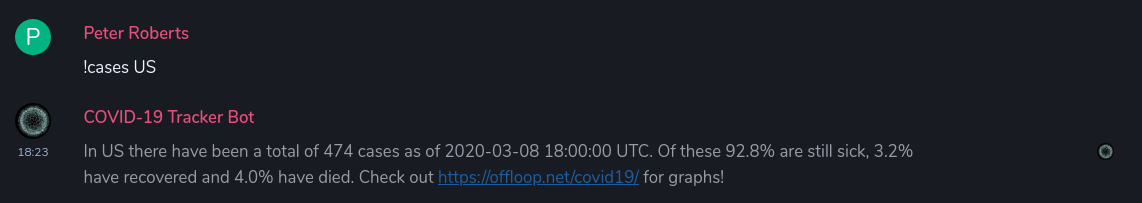
🔗CovBot
Peter Roberts said:
Lives in the cloud now so should be more reliable.
Fairly sure Peter is referring to his tracking bot being on new hosting. He could mean that he has ascended to the clouds, and is therefore more reliable, but perhaps he wouldn't have posted to TWIM in that case.
🔗dice bot
Tulir told us:
The maubot dice plugin got a new release. The primary change was a config option to show results of individual rolls.
🔗OBS bot v0.5
msirringhaus announced:
In addition to some performance fixes, the chat bot integration in Rust for openSUSEs Open Build Service can now listen also to openQA events.
openQA is an operating system level integration testing framework that makes it possible to test the installation process, GUIs and TUIs by simulating user interaction on different hardware or virtualization technologies. OBS is used for development of the openSUSE distribution and can build packages from the same sources for Fedora, Debian, Ubuntu, SUSE Linux Enterprise and other distributions.
Sources can be found here, RPMs exist as well.
🔗Dept of Hackathons 🍕
🔗Mozilla is hosting a Fix-the-Internet Lab
Aaron told us:
Mozilla is hosting a Fix-the-Internet Lab from April 15th - June 15th that specifically calls out decentralization and messaging.
Mozilla’s Fix-The-Internet MVP Lab is an 8 week-long incubator-style program this Spring to mobilize & fund around products and technologies that enable everyone to connect and build a better society.
Sounds like it could be a good fit for a Matrix community project. Each participant would get a $2500 stipend and access to mentorship. There are also significant prizes.
Applications are due Monday April 6 at 11:59PM ET.
https://blog.mozilla.org/blog/2020/03/30/were-fixing-the-internet-join-us/
🔗Swedish government launching a three-day remote hackathon
Ananace reported:
Maybe more tangentically relevant, but the Swedish government is launching a three-day remote hackathon starting tomorrow (3rd-6th of April) focusing on saving lives, communities, and businesses. A Matrix solution may very well be interesting to develop for this, perhaps something taking another look at the CoAP/CBOR work.
🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server. Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | envs.net | 357 |
| 2 | gottliebtfreitag.de | 429 |
| 3 | maunium.net | 456.5 |
| 4 | kif.rocks | 520 |
| 5 | imninja.net | 632.5 |
| 6 | encom.eu.org | 657 |
| 7 | fairydust.space | 676 |
| 8 | xethos.net | 804 |
| 9 | chat.matrix4me.de | 913 |
| 10 | synod.im | 1096 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!