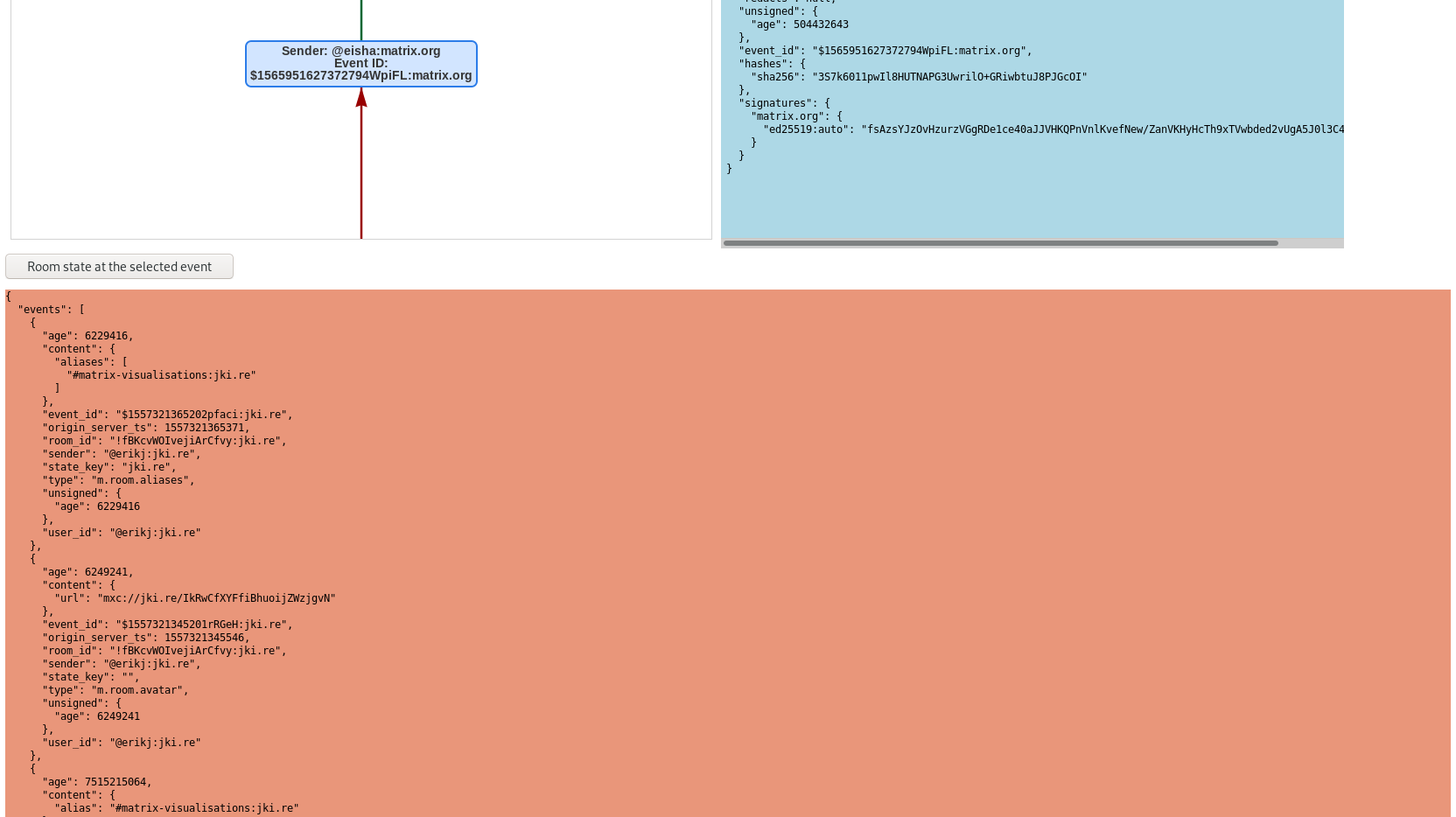
This Week in Matrix 2019-10-04
2019-10-04 — This Week in Matrix — Ben Parsons🔗Matrix Live 🎙
- Ubucon https://sintra2019.ubucon.org/
- PyCon Ireland https://python.ie/pycon-2019/
- OggCamp https://oggcamp.org/
- MozFest https://www.mozillafestival.org/en/
- and more, watch the vid
🔗Dept of Spec 📜
Two MSCs have reached final comment period this week:
Last week the spec core team said they'd start focusing on 3 MSCs per week. Those were MSC2290, MSC2176 and MSC1219. The first two have entered FCP, and MSC1219 will roll over into this week.
Thus, the 3 MSCs the spec core team will be focusing on this week will be MSC2199, MSC1219 and an up and coming security-related MSC. Join us in #matrix-spec:matrix.org for related spec discussions :)
There is also a new MSC, MSC2312 describing the proposed Matrix URI scheme. This is a remake of a much older proposal. The general idea is to make a standard for Matrix URIs: matrix:.
🔗Dept of Servers 🏢
🔗Synapse 1.4.0 released
Neil offered:
Synapse This week we shipped our privacy release 1.4.0 which is a huge deal in improving user data privacy. Additionally we also included a significant perf improvement which will help anyone suffering from a build up in forward extremities.
Coming up, improved room directory perf, ironing out wrinkles in the room upgrade UX as well as a major reliability boost in the sqlite -> Postgres db porting script.
🔗Dendrite dev recommences
anoa said:
Dendrite's latest hiatus has come to a close after the privacy work had taken so much of my time. Thankfully although PR review is blocked on the dendrite team, the community have continued to submit PRs and even review each other's PRs (thanks cnly !).
Fixes this week have mostly focused around the CI. We finally got Dendrite's CI unborked (t'was borked in a half-way transition between CircleCI and Buildkite), but it's now working and faster than ever. We're also working to add the Sytest test failure results to the top of the CI window such that people can see which tests failed and the associated Dendrite logs.
Additionally we had some new and merged PRs this week! A federation fix from cnly, a change to allow Dendrite to better work in kubernetes setups by aditsachde, and a codebase fix from @manasseh:matrix.org, who's also working on another fix involving updating gomatrixserverlib to support more recent spec versions.
Some things people were asking about:
- Progress of dendrite is tracked in Dendrite's milestones. We're currently aiming for #1 (Client-Side) Bot Hosting.
- CI not running for community PRs - Buildkite hosts currently run multiple PRs from many different projects, so we can't trust arbitrary code to run on them quite yet. There's a project in progress to run the code in a sandboxed environment (think VM or container) to lift this restriction :)
🔗Dept of Bridges 🌉
🔗matrix-appservice-slack 1.0 released
Half-Shot offered:
Aaaaaaaaaaand shipped 🥳 https://github.com/matrix-org/matrix-appservice-slack (1.0 is out!)
Check out the announcement post, big congrats to Half-Shot for getting this out.
🔗Bridging animated stickers to mautrix-telegram
tulir said:
mautrix-telegram will soon be able to bridge animated stickers to matrix as images or videos, thanks to a pull request by Eramde.
🔗Dept of Clients 📱
🔗Riot Web 1.4.0
Big release for riot-web, check out their release: https://medium.com/@RiotChat/new-privacy-controls-for-riot-dc3661888563
🔗Riot Android and RiotX
From Benoit:
Riot-Android: 2 main things have landed on develop, to be released early next week:
- Catching up on riot-web new Privacy Controls (choose identity server, stun server, securely compare contacts)
- [fdroid only] A new background sync mode for notifications. You can now choose between 'optimized for battery' and 'optimize for realtime'
- build available on buildkite
RiotX:
- Read Markers have landed on develop (jump to last read) Focus on stabilization and bug fixes
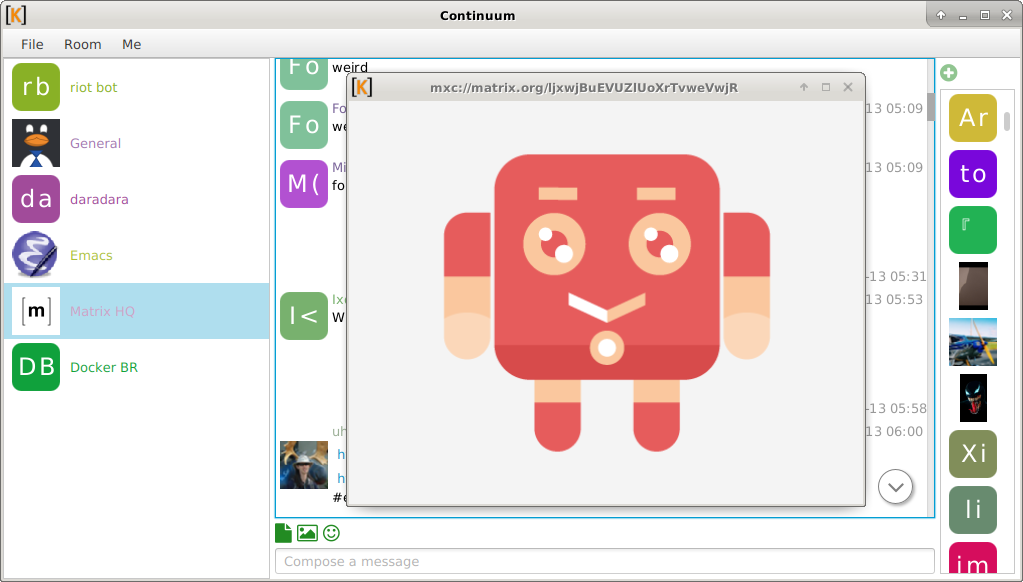
🔗Continuum
yuforia offered:
Continuum, desktop client written in Kotlin, version 0.9.26:
- Width of columns can be adjusted by dragging, this is a screenshot showing the mouse cursor placed between the first two columns.
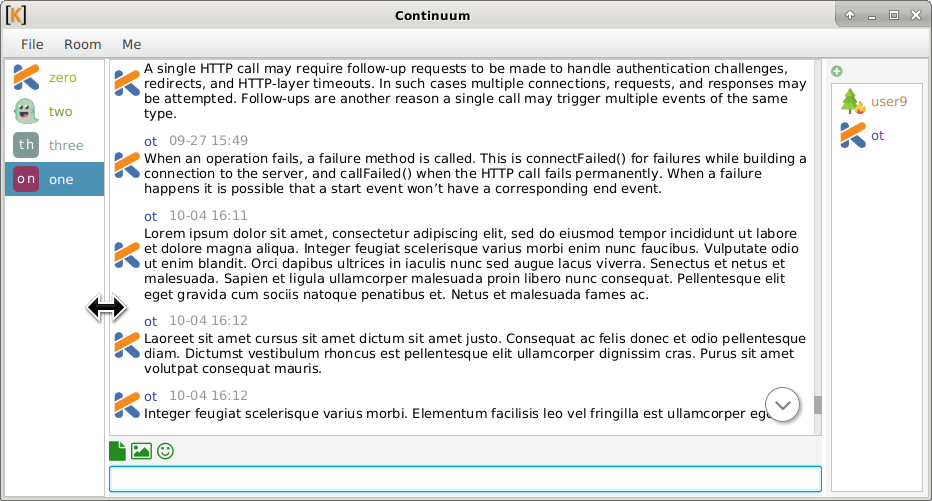
- Fix occasional out-of-bounds array access errors while calculating bounds during layout passes.
🔗FluffyWeb: Matrix client with Flutter for Web
@krille:ubports.chat offered:
As a proof of concept, I have created a little Matrix client with Flutter for Web, named FluffyWeb. This client has only basic features but it shows the possibilities of Flutter for Web and it seems to work fine so far. The client has a responsive design and should work on mobile fine too. Check it out at: https://christianpauly.gitlab.io/fluffyweb/ (Not working in Internet Explorer - I recommend the AOL Messenger in this case)
🔗Dept of SDKs and Frameworks 🧰
🔗Ruby SDK 1.4.0
Ananace said:
Just released version 1.4.0 of the Ruby SDK, the main change in this release is the addition of a naïve set of methods to replace the logger implementation. This should allow the gem to slot more easily into projects where existing logging configuration is already in place.
🔗Dept of Ops 🛠
🔗1.4.0.Mania
With the release of Synapse 1.4.0, there was a rush to get packages and containers updated, the community are always fast, but we should acknowledge Anance for having his k8s images updated within a few minutes!
🔗matrix-docker-ansible-deploy
Slavi announced:
matrix-docker-ansible-deploy has also been updated to support Synapse v1.4.0 and riot-web v1.4.0.
As always, referring to the project's changelog before upgrading is a good idea.
KUDOS to this this project! I love that I can git pull, ansible-playbook -i inventory/hosts setup.yml --tags=setup-all without really checking and my toy homeserver is automagically updated.
🔗Kubernetes
Ananace offered:
Just pushed the Kubernetes-optimized images for Synapse version 1.4.0
🔗mathijs's docker images
@mathijs:matrix.vgorcum.com reported:
I set up my own docker-hub account to push images of RC's of synapse at mvgorcum/docker-matrix that aren't built for the avhost/docker-matrix repo
🔗Dept of Bots 🤖
🔗msc name linker bot
anoa said:
I made a bot that gives the link for msc names. Code is here: https://github.com/anoadragon453/msc-chatbot
🔗Dept of Welcomes 👐
Welcome to the JRuby team who announced they will be moving their official chat to Matrix.
🔗Dept of Ping 🏓
Let's reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server. Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | matrix.tetraodon.nl | 317 |
| 2 | linuxgl.ch | 405 |
| 3 | fachschaften.org | 473 |
| 4 | glowers.club | 489.5 |
| 5 | flobob.ovh | 501.5 |
| 6 | im.leptonics.com | 501.5 |
| 7 | matrix.vgorcum.com | 513.5 |
| 8 | pztrn.name | 515 |
| 9 | matrix.markusbenning.de | 524 |
| 10 | kolosowscy.pl | 543 |
🔗Final thoughts 💭
Mastodon released v3.0.0 - check it out.
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!

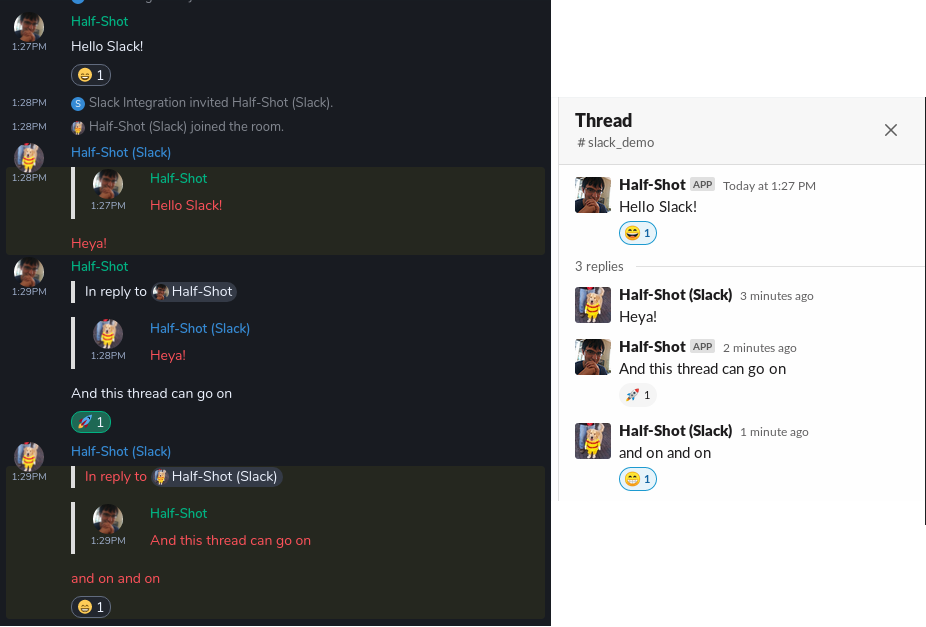 Threading & Reactions!
Threading & Reactions!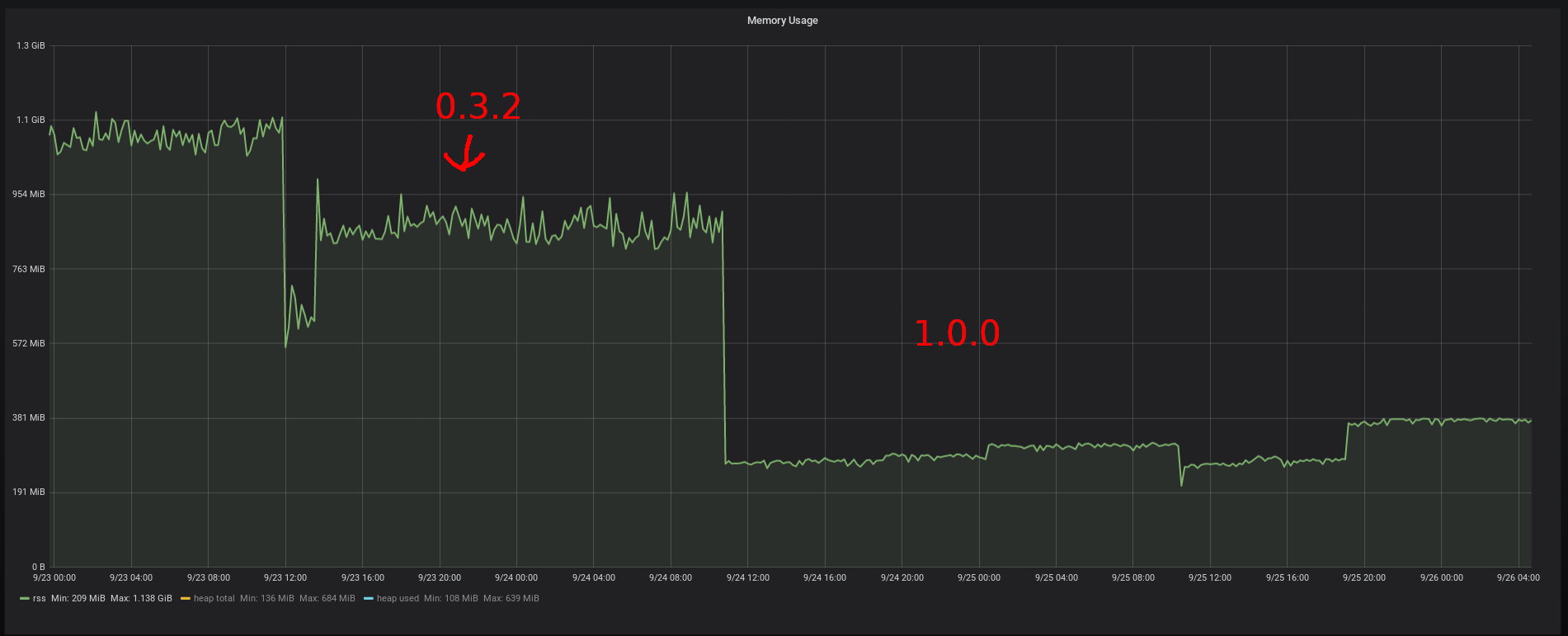 Memory usage of the bridge comparison
Memory usage of the bridge comparison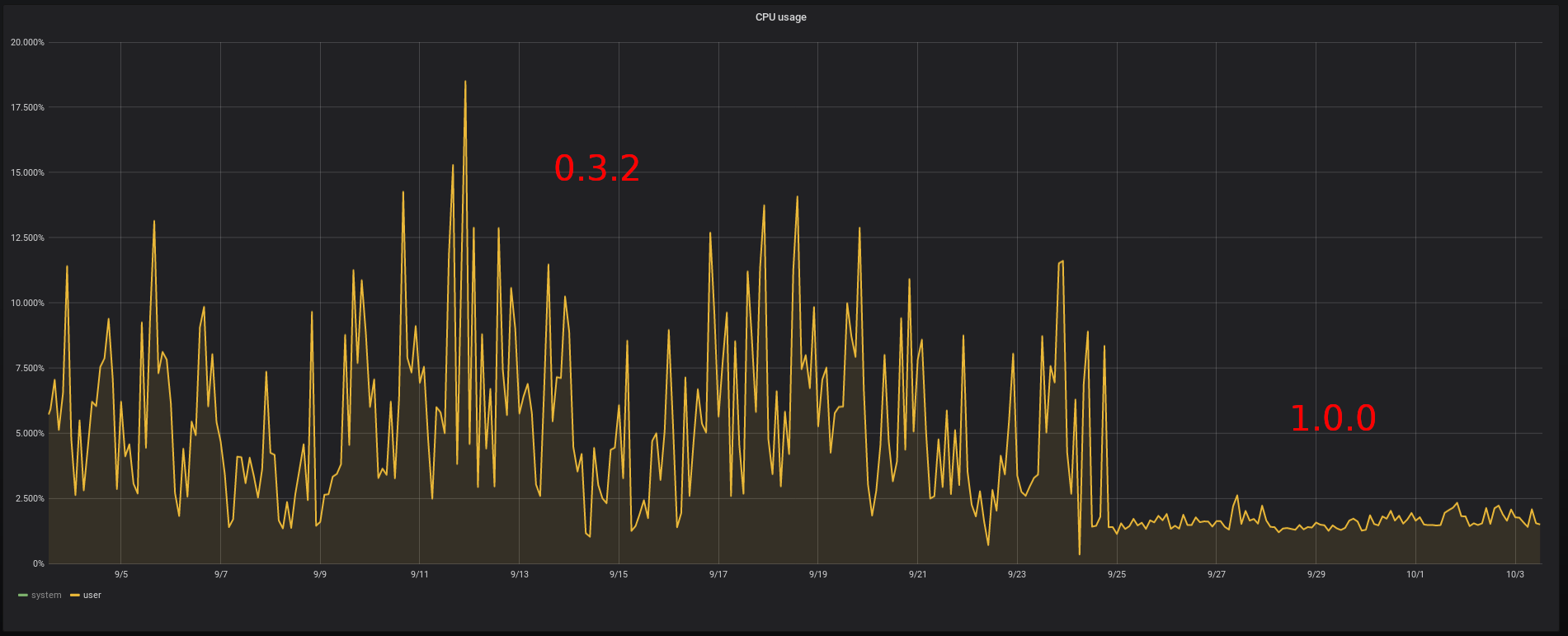 CPU usage of the bridge comparison
CPU usage of the bridge comparison