This Week in Matrix 2019-05-03
2019-05-03 — This Week in Matrix — Ben Parsons🔗New matrix.org Security Disclosure Policy and moderation pages
Check out the Matrix Official Security Disclosure Policy, which also features a "Hall of Fame": https://matrix.org/security-disclosure-policy/
We also have an official moderation guide now at https://matrix.org/docs/guides/moderation
🔗Servers
🔗Synapse
🔗Last week
Work progresses on reactions support, expect a more formal MSC rsn, but for check out https://github.com/matrix-org/matrix-doc/blob/matthew/msc1849/proposals/1849-aggregations.md for more details. Aside from that we now have an API to send server notices, support is coming for blacklisting IP ranges for federation traffic and finally we published a security disclosure policy and hall of fame https://matrix.org/security-disclosure-policy/. We’ve also been tracking down some device management bugs that prevent e2e message decryption as well as fixing some security bugs.
🔗Next week
More reactions work, device management bug hunting and server key validity support.
🔗Crypto
- Olm 3.1.2 bugfix release.
- Pantalaimon: Initial SAS support through panctl http://webmshare.com/play/QeBY1
- Pantalaimon: Support for sending out key requests.
🔗Clients
There are some BIG (capital and bold!) client releases this week, let's take a look
🔗Quaternion 0.0.9.4
Big release for Quaternion this week, following lots of work on libQMatrixClient. kitsune reports that:
Quaternion is now officially at version 0.0.9.4! Optional native scrollbar for the timeline, files uploading, initial support of matrix.to links (the foundation for future Matrix URIs), first complete translations, and much much more - the long list is here: https://github.com/QMatrixClient/Quaternion/releases/tag/0.0.9.4. Packagers are advised to take a look at the building and packaging section of the release notes: there are a few updates for you there.
🔗Spectral
Continuing the QT-client theme, Black Hat has released a new version of Spectral to FlatHub, join #spectral:matrix.org for more:
A new version of Spectral is released on Flathub this week! The last release is half a year ago, and there are a lot of changes since then, including a better UI, bug fixes and performance improvements.
Changelog:
Increase minimum Qt version to 5.12.
Redesigned UI.
Emoji and username auto completion in text input.
Respect server-side notification settings.
Emoji picker.
Fix font size in HiDPI.
Improved reply UI/UX and rich reply UI.
Sending/receiving typing notifications.
Switch to hoedown for parsing markdown.
Display notification count.
Responsive UI.
Fix #2(Room/People separator issue).
Infer device name from system information.
Image caching.
And of course various performance improvements. For my account Spectral takes ~35MB RAM initially, compared to 45~50MB before.
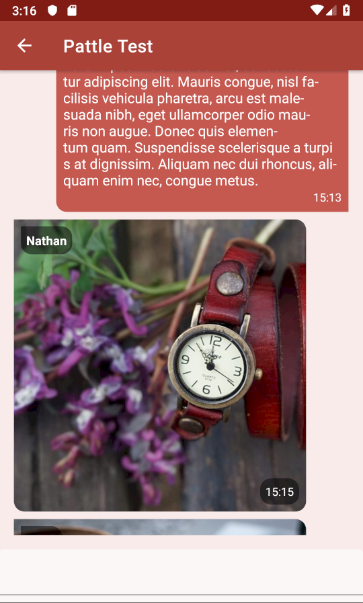
🔗Pattle new release

Wilko came to announce a new Pattle release, that's the Flutter client:
A new release of Pattle has been pushed to F-droid! Lots of different changes this release, including:
- Viewing images!
- Actual local echo (message is immediately placed in the timeline)
- Sent state indicators are now shown next to the message time (clock for still being sent and a checkmark for sent)
- Show member change events! (x has joined, left, invited, etc)
- Thumbnails are now used for chat avatars, which should improve performance a bit
- Other small fixes :)
Check out a video demo at here.
🔗continuum
yuforia reports that:
This week in continuum:
- Remove support for embedded webview and open external browsers when necessary instead. Many users actually prefer it this way. And dependency on a fairly large native module is gone.
- Improvements on the emoji input. Removed some style classes and tweaked some sizes to make the appearance more compact and flat. https://matrix.org/_matrix/media/v1/download/matrix.org/PvFFPAvoDhiHghsyeJnWVyAK
🔗Riot Web
Initial UI work on reactions and editing, nothing useable yet though.
🔗Riot iOS
- Release of 0.8.5 :
- Grouped notifications
- Interactive device verification (by emoji)
- WebRTC and Jitsi libs updates
- min iOS version is now 10 (Jitsi constraints)
- Initial UI work on reactions, nothing useable yet though.
🔗Riot Android
Benoit from the Riot team:
- CI has been configured on Buildkite for the Android matrix sdk, riot and riotx.
- The Android sdk can now be integrate as a grate dependency via Jitpack.
- Riot 0.9.1 has been released with sas feature included! Device verification is easier with riot web and riot Android users, soon with riot ios users. Will be on production channel on Monday.
- We have finally pushed the security fix on GH.
- Also working on the crypto modularization to integrate it on RiotX.
- We will concentrate our effort on RiotX now
🔗RiotX (Android)
- Working on reactions
🔗Bridges
🔗matrix-appservice-discord searching for a new maintainer
Sorunome reports that:
We (matrix-appservice-discord) are looking for a new maintainer!
What are we looking for in a maintainer?
You wouldn't have to be super active, however a few minutes per day would be greatly appreciated. You'd be responsible of reviewing PRs! Because of this not being afraid of Typescript and not being afraid of Discord is required - no need to be at pro-level!So we are basically looking for someone who can help us look over PRs and maybe do some themself. If you think you are interested, please message us in our matrix room!
🔗Bridging Facebook Messenger
I made a new Facebook Messenger bridge: https://github.com/tulir/mautrix-facebook / #facebook:maunium.net. Currently the main difference to matrix-puppet-facebook is multi-user support like my WhatsApp and Telegram bridges. The bridge is Python and the code structure is similar to mautrix-telegram, so I'll probably eventually create a generic bridge library out of the common parts.
🔗SDKs and Frameworks
🔗Ruby SDK
Ananace reports that:
Working on the Ruby SDK again, planning to try and get it to the point where I feel comfortable calling it a provisionary 1.0 release. I want to propose additions to various software using it after all, and that tends to look better if it's 1.0 - or close. 😃
🔗That's all I know
That's all for this week folks, come chat in #twim:matrix.org for more, or to share what you've been working on.
PS this interesting-looking project is not ready for public eyes on it yet, so please refrain from checking out the code and discussing with the author in #tangent:matrix.org