This Week in Matrix 2018-10-26
2018-10-27 — This Week in Matrix — Ben ParsonsWe have a LOT of updates this week, so let's dive straight in!
🔗matrix-docker-ansible-deploy
We've covered the growth of this project several times in TWIM, but I wanted to give a little more attention to the work Slavi has been doing with matrix-docker-ansible-deploy. Synapse is a large Python project with many configurable options, and many optional components, so installing it has sometimes been a challenge. I have seen many reports that using Ansible and Docker, and in particular using these playbooks from Slavi, is a more sane way to install Synapse. The tools get a lot of attention and updates. This week, Slavi reports:
matrix-docker-ansible-deploy now has a self-check command that can help diagnose various configuration problems with the setup (DNS records being misconfigured, firewall ports not being open, etc).
For support and more info, come join the associated room: #matrix-docker-ansible-deploy:devture.com
Late breaking news from Slavi:
One more matrix-docker-ansible-deploy update: the playbook can now set up Whatsapp-bridging via mautrix-whatsapp. Thanks to @izissise!
🔗Dimension
Dimension is an integration manager for Matrix. It's written and maintained by TravisR, and allows you to an a pre-defined selection of widgets, bots and bridges to improve your self-hosted Matrix experience. Check out: https://dimension.t2bot.io/. This week, TravisR reports:
Dimension has received quite a lot of updates over the last week. Here's what's hot off the press:
As per usual, if you find any bugs or have ideas for things to add to Dimension feel free to come by #dimension:t2bot.io
- 4 new bridges can be self-hosted and managed in Dimension: Telegram, Webhooks, Slack, and Gitter.
- 3 new widgets are available: Grafana, TradingView, and Spotify.
- Add your own custom bots for people to add to their rooms.
- A dark theme has been added and is automatically applied if you use the dark theme in Riot.
- The overall UI has been updated to be slightly more modern and less bright orange.
- Various bug fixes and improvements (is it even possible to have a changelog without this?)
🔗mautrix-telegram
tulir has been working on mautrix-telegram, and has made some massive performance improvements:
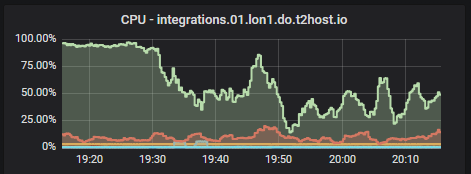
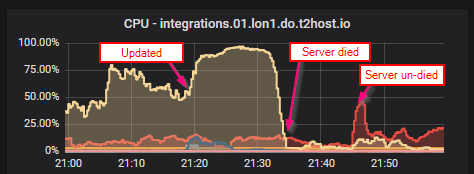
mautrix-telegram now uses the non-ORM part of SQLAlchemy for database tables that are used often. That change made the CPU usage on the t2bot.io instance drop from ~100% to ~7%
We have graphs to illustrate the improvements:
TravisR, who hosts the bridge on t2bot.io, reports that the bridge is now effectively instantaneous!
The bottleneck has returned to being synapse instead of the bridge
🔗Discord Bridge 0.3.0-rc1
A tonne of work has happened on the Discord Bridge, and it has all been brought together in 0.3.0-rc1.
From the release notes, this is just a subset of the features:
- #251 Support for Postgresql and a newer SQLite3 backend!
- #182 Replace npmlog with winston, for logging to files and better logging overall.
- #221 Add support for
m.sticker. - #210 Discord-side moderation of matrix users.
- #259 Show Matrix replies as Discord embeds.
- #164 Bot will now mention name, topic and membership changes on Discord.
- #175 Add special discord keys onto m.room.member for ghosts
Shoutout to our new member of the team, @Sorunome who did a lot of the review work behind the scenes for this release. Also, thank you to everyone who submitted a PR or an issue!
🔗Slack Bridge 0.2.0 released!
We covered progress on the Slack Bridge previously, but Half-Shot has now declared it ready for 0.2.0 final! The bridge is reportedly running and very stable - go try it out now!
https://github.com/matrix-org/matrix-appservice-slack/releases/tag/0.2.0
🔗Spectral
We just missed out on this update from Spectral last week. Black Hat says:
Spectral now provides an AppImage along with Flatpak build. Also, thanks to the notification codes from nheko, Spectral can show icons in notifications, and now enters corresponding room when clicking on the notification. It also gains several UI/UX improvements.
P.s. I have resubmitted Spectral to Flathub.
🔗FAQBot
Coffee featuring two weeks in a row in TWIM:
FAQBot has been set free at last! Find its code at https://gitlab.com/Matrixcoffee/FAQBot, and its room at #faqbot:matrix.org.
FAQBot sits in various public rooms and answers common Matrix questions. Very useful for demonstrating the product to newcomers!
Also, if anyone wants to help write answers for FAQBot, https://gitlab.com/Matrixcoffee/matrix-knowledge-base is the place.
Strongly encourage people to go take a look at the knowledge base and see what can be improved.
🔗New communities
swedneck has created a new gaming community on Matrix:
we just bridged the linux-gaming community from discord to matrix, with a matrix community and individually bridged rooms/channels and all main room is #general_linuxgaming:matrix.org community is +linux-gaming:matrix.org
i've set up an instance of matrix-appservice-discord, which is bridging some select rooms from the linux-gaming discord server to +linux-gaming:matrix.org
The Linux Gaming community has gotten a proper matrix community (+linux-gaming:matrix.org) with a fair few rooms in it, all of which are bridged to a discord channel via my matrix-appservice-discord instance.
#prismo:matrix.org and #anfora:matrix.org have also been bridged to discord.
🔗Matrix for Ansible notifications
If you are using ansible, jcgruenhage has a useful addition that will allow you to get notifications from matrix:
After over a month of waiting, the matrix notification module has been merged on to ansible devel which will be released as ansible 2.8 early next year. Src: https://github.com/ansible/ansible/pull/45823
🔗mxisd v1.2.0-beta.3
Max:
mxisd v1.2.0-beta.3 is out with the start of a brand new Identity store based on arbitrary executable, to connect to anything and everything. Authentication is implemented at the moment (see doc). Feedback is very welcome to improve as much as possible for v1.2.0
🔗MSC1695 Message Edits
Discussion of message editing, in particular for how message edits from Bridges are handled has progressed. Nothing is final yet so check out https://github.com/matrix-org/matrix-doc/pull/1695 for the latest.
🔗Quaternion translations: German and Polish now available
Last week we had an update from kitsune to say that there was a new Lokalise project to allow Quaternion translations. This week, we learn that the first translations are now available:
First couple of translations - German and Polish - have made it to the released Quaternion 0.0.9.3 - thanks to krombel and krkk for their contributions! Swedish and Russian translations are in the works.
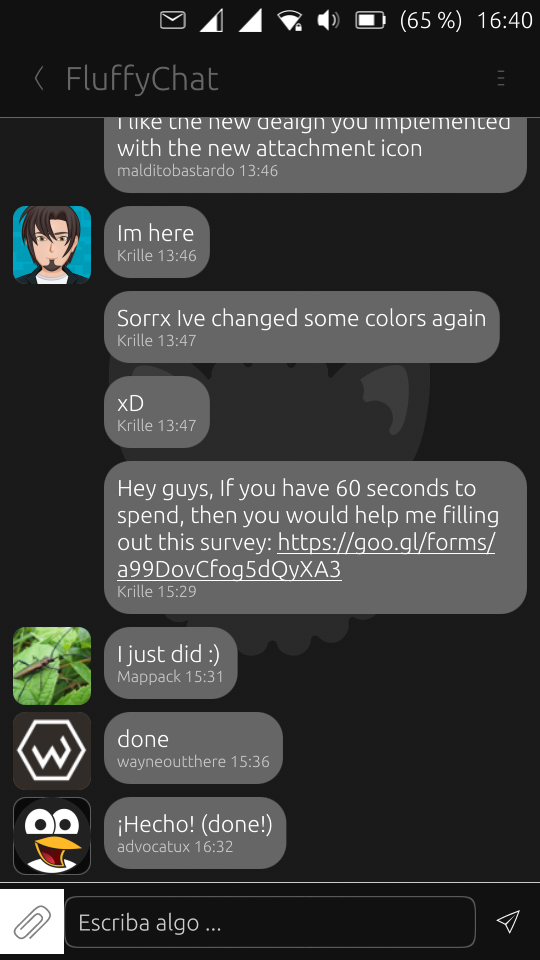
🔗Fluffychat
We anticipated it last week, but here it is:
The first stable release of the #matrix messenger #fluffychat is out now. ? Get it from: https://www.fluffy.chat
Thanks to all who have helped me. Thanks to regionetz for hosting the ubports.chat homeserver, thanks to @matrix for the awesome work, thanks to @Ubports for this awesome platform and to fabiyamada, advocatux, wayneoutthere, lionelb, Diogo, mithgarthsormr, mark, and all the awesome people from the community!!
With your help, Ubuntu Touch is still alive and has got a new stable messenger!
🔗Informo: new bot for spec changes
Informo is an ambitious project hoping to be a "decentralised news network, making information accessible". The project lives at https://github.com/Informo, but for now you can join #discuss:weu.informo.network to get their latest news.
This week, vabd reports:
We made a Matrix bot that shouts about updates to change submissions to Informo's specifications. It basically processes all changes made to the list of labels for each issue and PR of a GitHub repository's, and generates a notice message that it sends to the configured room(s). We made it because we wanted the people that are interested in Informo to know in real time about any change made to the state of proposals, along with the calls for public reviews. We just set it up in #discuss:weu.informo.network, and published its source code along with a built binary here: https://github.com/Informo/specs-bot
It might also be worth noticing that, although we designed it to shout about updates to Informo's specifications proposals, we also made it compatible with other projects, e.g. the Matrix specs
🔗Push-to-talk functionality with Jitsi on Riot
anoa has been making improvements to Video Calling on Riot:
I've been working on global push-to-talk functionality with Jitsi on Riot. I've got toggle on/off functionality working, but still trying for walkie-talkie mode. To do so, I need to get this library working with Riot: https://github.com/WilixLead/iohook
If anyone has experience with native Node modules and/or Electron, please hit me up! @andrewm:amorgan.xyz
🔗Greetings from Mozfest
Mozfest is a tech-focused event happening this weekend in London. Neil and I have been along tonight and we've been chatting to a lot of people about Matrix, decentralisation and all those things we love! Check out our very short and sweet video below!
This is the start of Season Three of Matrix Live. Matrix Live seasons are variable in length, based on the data available so far. From this season, Matrix Live with change the format slightly, based on feedback. The videos will try to be a bit more interesting, varied, and deep. With this video being the start of a new season, it was meant to be more substantive with us talking to Mozfest-ites, but I lost track of time, so this shorter but still energetic video will hopefully convey the idea.