This Week in Matrix 2022-06-03
2022-06-03 — This Week in Matrix — Thib🔗Matrix Live 🎙
🔗Dept of Spec 📜
TravisR reports
Hey all, it's been a holiday for much of the team this week, so from the plane of Maple trees I present to you the spec update.
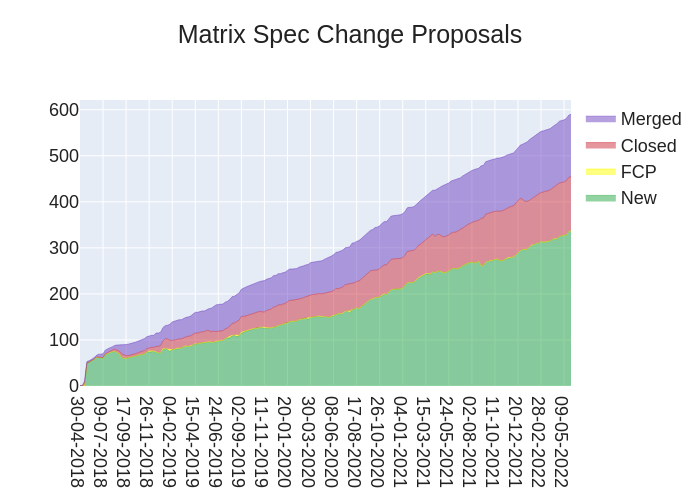
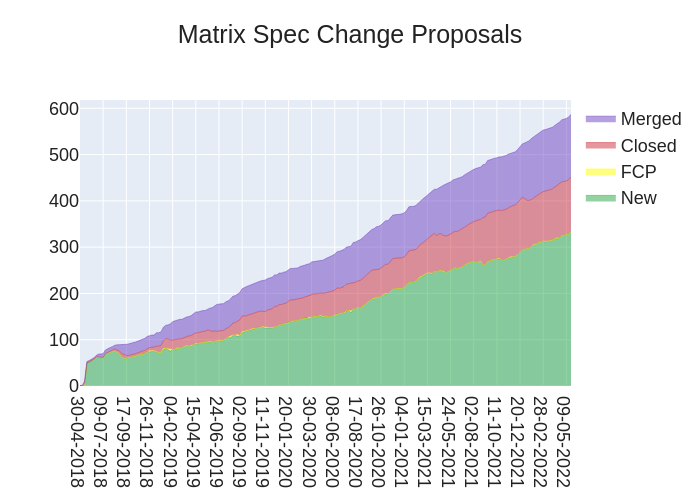
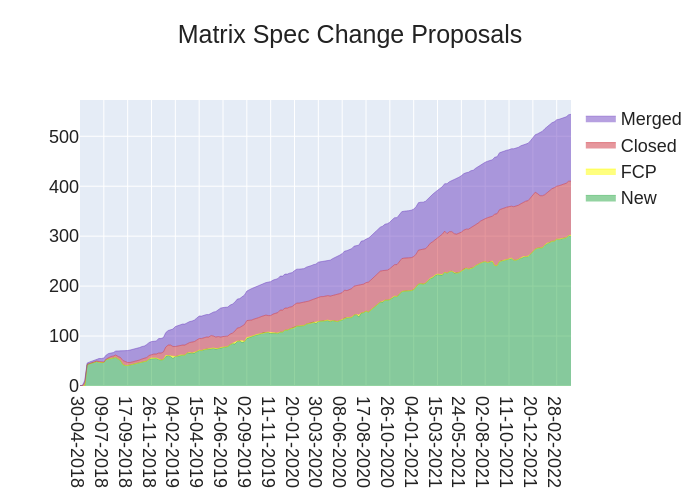
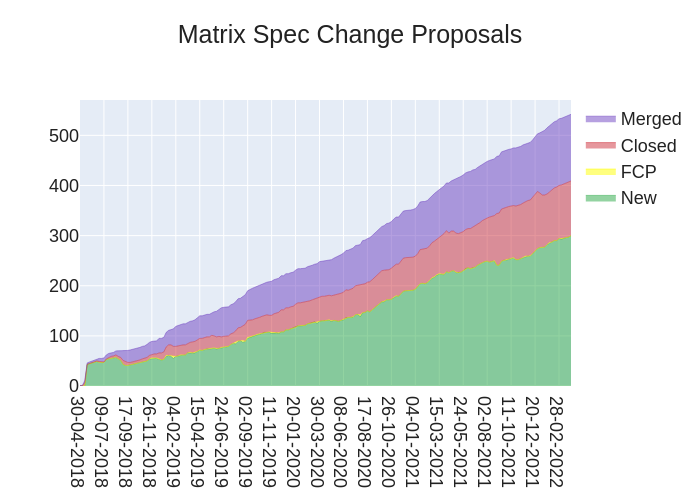
The heart of Matrix is the specification - and this is modified by Matrix Spec Change (MSC) proposals. Learn more about how the process works at https://spec.matrix.org/unstable/proposals
🔗MSC Status
Merged MSCs:
MSCs in Final Comment Period:
New MSCs:
🔗Spec Core Team
In terms of Spec Core Team MSC focus for this week, we've been working on getting Matrix 1.3 out the door and generally working towards a better process for handling releases alongside critical proposals for the protocol. The goal is to be able to ship these major features while reducing the risk of a release falling behind. Watch this space for more details as this should result in MSCs getting through the process a little bit quicker.
For Matrix 1.3, we're targeting Thursday, June 16th, 2022 as our release date, though this comes with a small asterisk: we're looking to land quite a lot of stuff so might have to adjust the date once more as needed. We do feel reasonably confident in the date though - watch for blog posts titled Matrix 1.3 in the coming weeks.
🔗Random MSC of the week
The script has chosen MSC2846 - Decentralizing media through CIDs as your random MSC this week. The MSC raises an interesting question about how to make media more akin to events in Matrix. If you're interested in this area, take a read of it and the related MSCs.
🔗Dept of GSoC 🎓️
🔗Encrypted Search for Matrix
burgers says
Hey there, I'm Aditya Rajput (aka BURG3R5), a sophomore at IIT Roorkee, India. This summer I'll be working on implementing encrypted Search in Matrix rooms. More details about this project can be found here. Once a week, I'll be blogging about my progress (plus some neat stuff I find during research) in this blog. Technical discussion and more frequent updates can be found in the public room #encrypted-search:matrix.org.
While writing my GSoC proposal, I'd already made some progress w.r.t. the actual code required for this project, and my preliminary implementation can be found here.
Looking forward to working in this ecosystem with you all!
🔗Kazv Project
nannanko announces
Hello everyone, my name is nannanko. From today, I will officially participate in GSoC to contribute code to the Kazv Project. I hope I can get along well with you all.
🔗3rd Party Authorised Room Membership
kuries says
Hey there! I'm Binesh Munukurthi, a Computer Science student from India. I'll be working on the 3rd Party Authorised Room Membership project for this year's GSoC.
This project aims to develop an application that has the ability to delegate membership of a room based on a user’s interaction with other third party services. For more details on what I'll be implementing, please refer to the link
I'll be posting my weekly updates here If you are interested in knowing more about the project's progress, feel free to join the public room #matrix-cerberus:cadair.com.
I look forward to spending a wonderful summer with you all! Thanks!
🔗NeoChat
flyingcakes announces
Hi! I'm Snehit Sah. I will be contributing to KDE's Matrix client, NeoChat, during GSoC. I will add Spaces support to the application. My progress can be followed at my blog. Hoping for a fun stay!
🔗Dept of Servers 🏢
🔗Synapse (website)
Synapse is a Matrix homeserver implementation developed by the matrix.org core team
Shay says
This week was a short one, but work continues on fast room joins, testing Synapse with workers on Complement, and increasing the efficiency of Synapse with regard to database i/o. In addition, we released v1.60.0 (https://github.com/matrix-org/synapse/releases), which includes
- work to reduce the possibility of database corruption
- a fix to a bug introduced in Synapse 1.60.0rc1 that would break some imports from
synapse.module_api
🔗Dendrite (website)
Second generation Matrix homeserver
Till reports
This week we released Dendrite 0.8.7! This is a highly recommended update since it fixes some fairly large bugs:
- Support added for room version 10
- A number of state handling bugs have been fixed, which previously resulted in missing state events, unexpected state deletions, reverted memberships and unexpectedly rejected/soft-failed events in some specific cases
- Fixed destination queue performance issues as a result of missing indexes, which speeds up outbound federation considerably
- A bug which could cause the
/registerendpoint to return HTTP 500 has been fixedAs always, please feel free to join us in the #dendrite:matrix.org room for more discussion!
🔗Dept of Clients 📱
🔗Quadrix
JFA announces
Quadrix is a single-codebase, multi-platform project, using the meanwhile deprecated ReactXP framework (Microsoft's answer to Flutter), which compiles to iOS, Android, and web/Electron. The Quadrix apps are available in the main app stores for mobiles and desktops (including Snapcraft and Flathub). Repo is at https://github.com/alariej/quadrix. Would be great to have a few people test the apps and leave feedback in the repo or in the (still empty) #quadrix:matrix.org room!
Important: Quadrix doesn't support E2EE yet, but it's on the TODO.
🔗Element iOS (website)
Secure and independent communication for iOS, connected via Matrix. Come talk with us in #element-ios:matrix.org!
Ștefan says
- Our prototypes for a new app layout are going well. Just a few people have early access in order to give us feedback to ensure we’re building a new layout that works for everyone. Watch this space!
- We’ve been working on improving our onboarding flow so that users signing up for Matrix and Element find it much easier. This work is making great progress.
- Live location sharing is also making great progress and is quickly approaching the beta phase
- On the ElementX front we’ve been busy adopting async/await, introducing state machines, a new design kit component and hooking up crash reporting and sentry.io
🔗Element Android (website)
Secure and independent communication for Android, connected via Matrix. Come talk with us in #element-android:matrix.org!
Manu reports
- We are a bit late on the release candidate. We want to fix a performance regression when switching spaces. It will be available early next week.
- We have merged the UnifiedPush PR from P1gP1g. We are doing some adjustments but users will be able to choose their push distributor soon.
- The prototypes that are with a small group of early access tester are going down a storm - we’re getting lots of great feedback that will help to build a new app layout that works for all.
- Our improvements to the first time user experience are nearly ready for testing and shipping! We’re hoping to make our onboarding experience a lot simpler for folks that are creating an account.
🔗Cinny (website)
Cinny is a Matrix client focused on simplicity, elegance and security
Lozenge reports
Cinny v2.0.4
🔗What's changed
- Fix emoji autocomplete in some cases
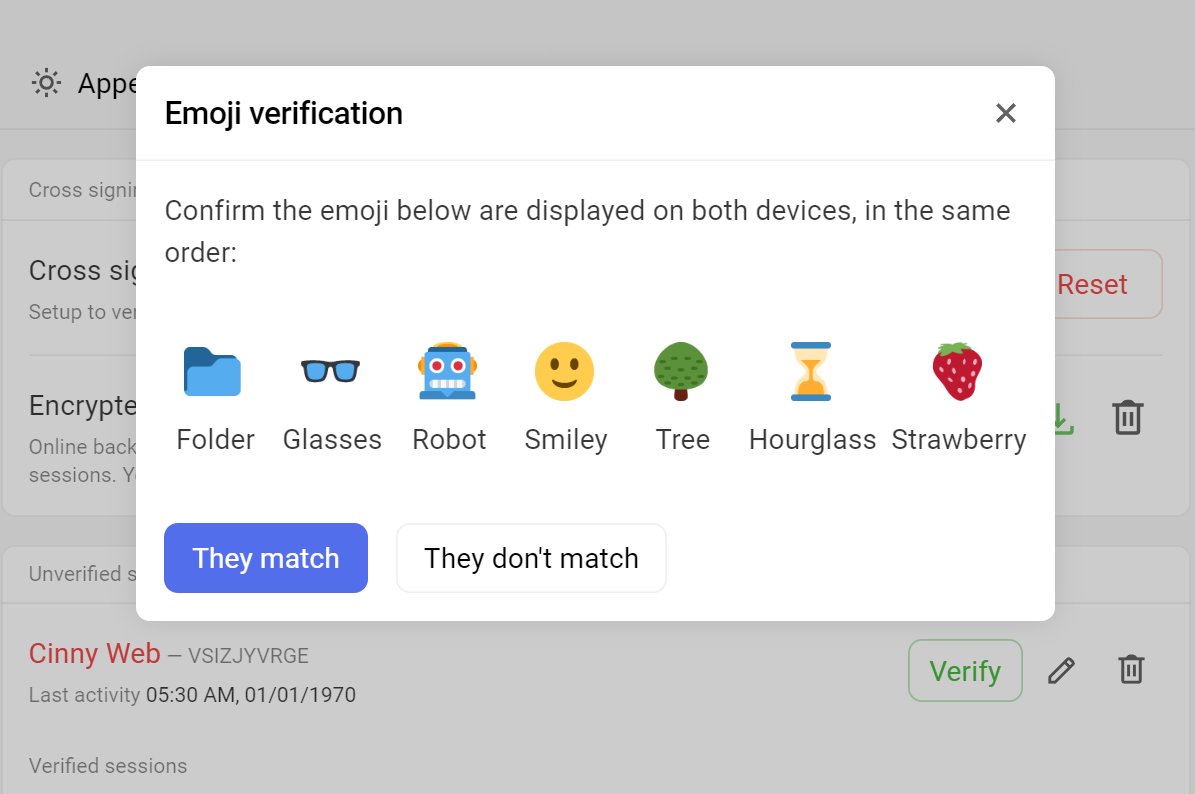
- Hide verify button if Cross-Signing is not enabled
- Add support for building docker image for linux/arm64
- Fix drag-n-drop not working in desktop app
- Add dev-tools to production builds of desktop app
- Fix copy-paste not working on macOS in desktop app
- Flatpak package for the desktop app
Find more about Cinny at https://cinny.in/ · Join our channel at: #cinny:matrix.org · Github: https://github.com/ajbura/cinny · Twitter: https://twitter.com/@cinnyapp
🔗Dept of Non Chat Clients 🎛️
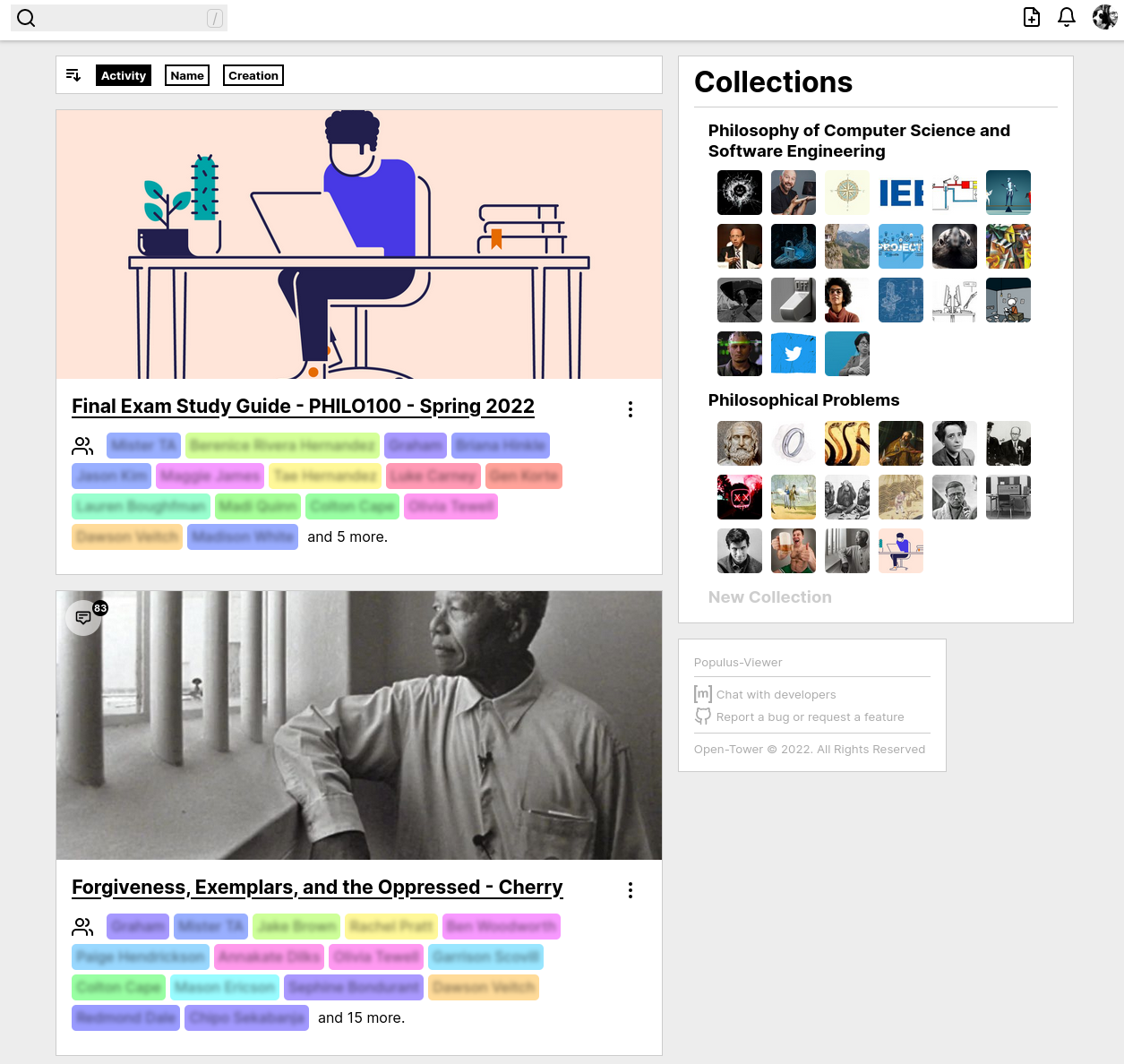
🔗Populus Viewer (website)
A Social Annotation Tool Powered by Matrix
gleachkr says
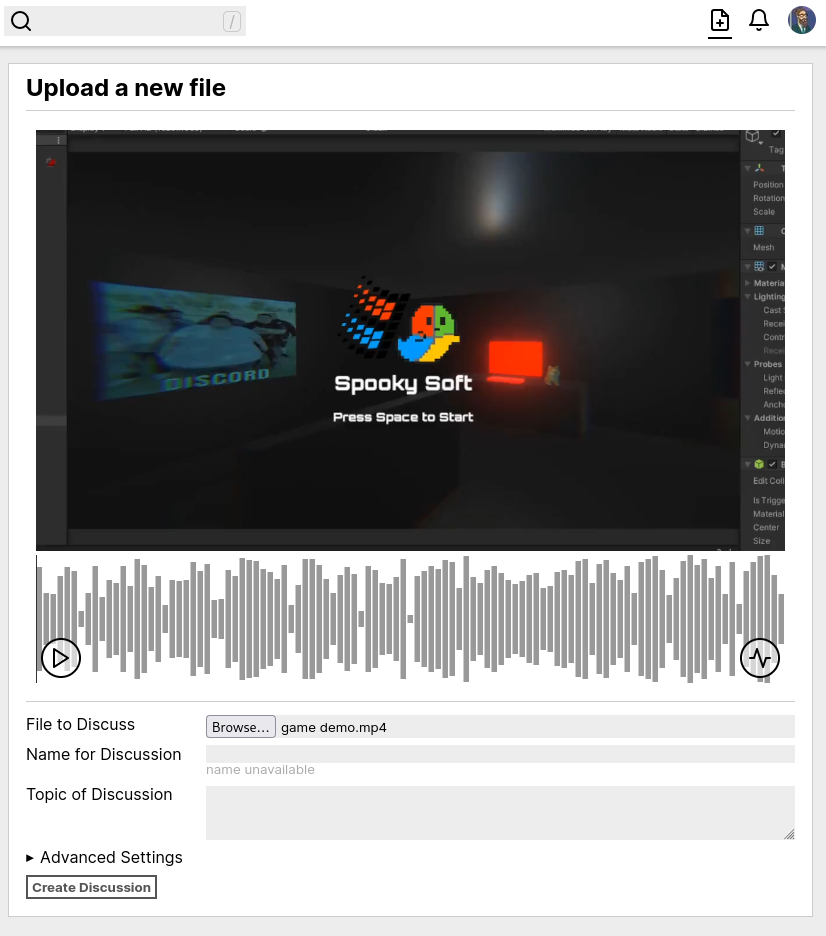
The last two weeks have been focused mainly on nuts-and bolts improvements to user experience, rather than any big new pieces of functionality. We've:
- Added upload previews for PDFs and audiovisual media, so you can confirm you're uploading the right thing before creating a discussion.
- Added a method to precompute PCM data for more accurate waveforms in audiovisual-media-based discussions.
- Allowed for join rules and annotation visibility to be modified separately in settings
- Added support for URLs linking directly to particular events
As always, if you're interested in social annotation on matrix, come join us at #opentower:matrix.org!
🔗Dept of VoIP 🤙
🔗Element Call (website)
Native Decentralised End-to-end Encrypted Group Calls in Matrix, as a standalone web app
Matthew reports
We've had breakthroughs this week on implementing a native Matrix SFU (selective forwarding unit) which speaks MSC3401, thanks to Sean DuBois - all round WebRTC superstar, project lead for the Pion WebRTC implementation for Go, and author of WebRTC for the curious.
Sean generously contributed an initial proof of concept to show how you'd build an MSC3401 SFU using Pion at https://github.com/matrix-org/sfu-to-sfu - which (I think?) is the first time that the first implementation of a major core MSC has been contributed from outside the core team. Huge thanks to Sean to setting the ball going on this - the current PoC demonstrates not just SFU capability but also the decentralised cascading architecture which makes MSC3401 unique. The initial PoC speaks a 'test jig' version of MSC3401 hooked up to a simple web client for experimentation, but Matthew's now experimenting with adding genuine Matrix support to it via mautrix-go, and hooking up Element Call to speak to it.
Adding SFU support to Element Call will mean that we can support more than ~7 simultaneous calls - and with MSC3401-style decentralised cascading, we should be able to support hundreds or even thousands. There's lots of work remaining here, but the ball is now rolling. For more info about SFUs and MSC3401, check out Matthew's CommCon 2021 talk (which was what prompted Sean's implementation work here!)
Separately, we've been running Element Call on staging with E2EE enabled for the last few weeks, and should be releasing the first major Element Call update next week. And once SFUs land, then Element Call can exit beta - watch out Zoom!
🔗Dept of SDKs and Frameworks 🧰
🔗libolm (website)
uhoreg announces
libolm 3.2.12 has been released. The main update in this release is that the
olm_sas_calculate_mac_fixed_base64is now exposed in all the official bindings, so that MSC3783 can be implemented. Aside from that, there have been some minor fixes and improvements. See the changelog for more information.
🔗matrix-rust-sdk (website)
Matrix Client-Server SDK for Rust
ben says
While most of the work in the background continues (Sliding-Sync PoC, Wasm+NodeJS support, UniFFI macros), the first few parts surface through the cracks and show themselves in new PRs: basic wasm web-js and nodejs support has landed with more APIs, tests and documentation on the way; the Sliding Sync PoC has been upgraded to the latest JSON layout and now provides a first set of reactive API via FFI, too. Furthermore this week has seen a bunch of cleanups, simplifications and clarifications around the OlmMachine and crypto types, and we're fixing a bug in the state store, where not all data has been properly encrypted in the past.
👉️ Wanna hack on matrix rust? Go check out our
help wantedtagged issues and join our matrix channel at #matrix-rust-sdk:matrix.org.
🔗Matrix Dart SDK (website)
Matrix SDK written in pure Dart and maintained by Famedly
Henri Carnot announces
Dart Matrix SDK : Version 0.9.9
This week, the team released version 0.9.9. In this new version, we added a search function to allow searching for an event in database and on server through several requests to the
/messagesendpoint.There was also some work on updating the image size when generating thumbnail, which allow saving a bit of calculation when sending events. If using a custom resizer make sure to update the resize response as here.
We also did some refactor with the event sender getter. The getter result is now a future to allow requesting the member event to the server if we cannot find it in memory, to help fix the issue when the user was not found in memory.
Finally, a quick helper function (
client.waitForSync) was added. It allows you to wait for a room to appear in (left, join, invited) section of the sync response.See you next time ;)
🔗Dept of Bots 🤖
🔗Matrix Community Manager (website)
The highly configurable message aggregation and filtering bot for matrix!
Sleuth announces
Only a small update this week. One new feature and some much needed Ansible improvements.
Pipes move messages from one room to an other. Useful if you are in important rooms but only want to monitor a single room. The Ansible role can now manage more aspects of MCM. Mainly in the post setup phase. The major one being if you run into encryption errors for any reason you can run the playbook with the fix tag and it will generate you a new device ID and encryption store.
- Pipes move all messages from one room to an other.
- Adding a filter now uses the room the command was sent from by default if the roomid is not specified.
- Ansible role now has tags for start, stop, configs, fix and all.
- Ansible role backs up the configuration.toml file to prevent the possibility of data loss.
Gitlab releases Come chat on Matrix
🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server.
🔗#ping:maunium.net
Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | the-apothecary.club | 450 |
| 2 | envs.net | 462 |
| 3 | polarbear.army | 473 |
| 4 | alemann.dev | 504 |
| 5 | aria-net.org | 530.5 |
| 6 | conduit.rs | 618 |
| 7 | tilduke.org | 643.5 |
| 8 | almum.de | 662 |
| 9 | keks.club | 731 |
| 10 | quyo.de | 879 |
🔗#ping-no-synapse:maunium.net
Join #ping-no-synapse:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | conduit.rs | 294.5 |
| 2 | dendrite.matrix.org | 305 |
| 3 | dendrite.neilalexander.dev | 387 |
| 4 | conduit.grich.sk | 433 |
| 5 | foxo.me | 465 |
| 6 | rustybever.be | 512 |
| 7 | cry.is | 521 |
| 8 | kszczot.pl | 527 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!