This Week in Matrix 2022-01-07
2022-01-07 — This Week in Matrix — ThibLast update: 2022-01-07 19:18
🔗Matrix Live 🎙
What a pleasure it is to be back with the community for the new year! This week Erlend is detailing what Commune is, and I'm flabbergasted by how well thought-through the project is.
🔗Dept of we've been away for holidays
This week in Matrix should be called Three Weeks in Matrix, since there hasn't been TWIM updates during the holiday season. Nico has published a first and second communitwim while I was away. All the news reports since the last official TWIM still made it to the post you're currently reading!
🔗Dept of Spec 📜
TravisR says
Your regular spec person, anoa, is out today so you're stuck with me, not-anoa. This time I got the script to work though 😇
Here's your weekly spec update! The heart of Matrix is the specification - and this is modified by Matrix Spec Change (MSC) proposals. Learn more about how the process works at https://matrix.org/docs/spec/proposals.
🔗MSC Status
Note: This is for the last 3 weeks given TWIM holiday :)
Merged MSCs:
- MSC3550: Allow HTTP 403 as a response to profile lookups
- MSC3442: Move the prev_content key to unsigned
- MSC3419: Allow guests to send more event types
- MSC3283: Expose capabilities for profile actions
- MSC3231: Token authenticated registration
- MSC3173: Expose stripped state events to any potential joiner
- MSC3069: Allow guests to use /account/whoami
- MSC2778: Providing authentication method for appservice users
- MSC2758: Proposal for common identifier grammar
- MSC2732: Olm fallback keys
- MSC2312: Matrix URI scheme proposal
MSCs in Final Comment Period:
- No MSCs are in FCP.
New MSCs:
- MSC3618: Add proposal to simplify federation /send response
- MSC3613: Combinatorial join rules
- [WIP: Not ready for review/impl] MSC3604: Room Version 10
- MSC3593: Safety Controls through a generic Administration API
- MSC3592: Markup locations for PDF documents
- MSC3589: Room version 9 as the default room version
- WIP: MSC3588: Stories As Rooms
- MSC3582: Remove m.room.message.feedback
- MSC3575 Sliding Sync (aka Sync v3)
- MSC3574: Marking up resources
Closed MSCs: Sadly, not every MSC makes it to the end.
- MSC3585: Allow the base event to be omitted from /federation/v1/event_auth response
- MSC2516: Add a new message type for voice messages
🔗Spec Core Team
In terms of Spec Core Team MSC focus for
this weekthe last little bit, we've been working on getting MSCs merged into the formal spec itself in preparation for v1.2 this quarter. We expect the release to happen quite soon and to contain Spaces, room versions 8 and 9, and refresh tokens (no spec PR yet) in addition to all the other wonderful stuff which has landed.The merged MSCs can be seen over at https://spec.matrix.org/unstable/ where they're queued up for the next release. Look out for
Added in v1.2labels throughout the spec, denoting what is new and exciting.🔗Random MSC of the week
The random MSC this week is MSC2192: Inline widgets (I promise it was random, after a few re-rolls). Inline widgets are a concept that allows for rich functionality in the timeline without needing to necessarily specify an explicit event type. For example, video embeds, minigames, etc could all be represented by inline widgets instead of dedicated event types.
The MSC needs updating to handle MSC1767: Extensible Events (and friends), but once there it could be a very powerful bit of functionality, with free fallback thanks to Extensible Events.
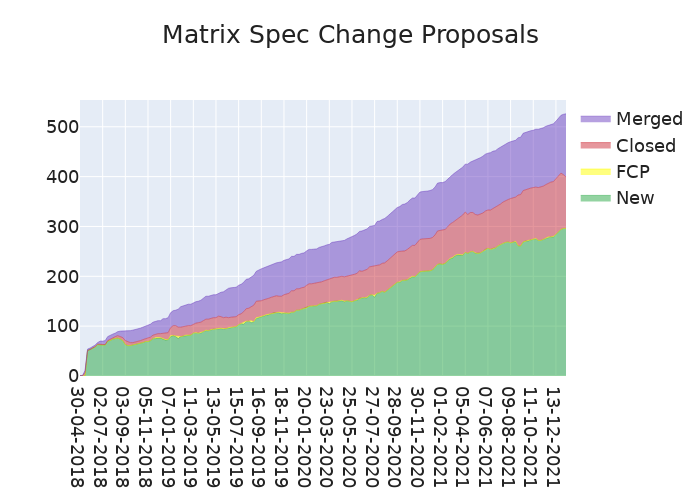
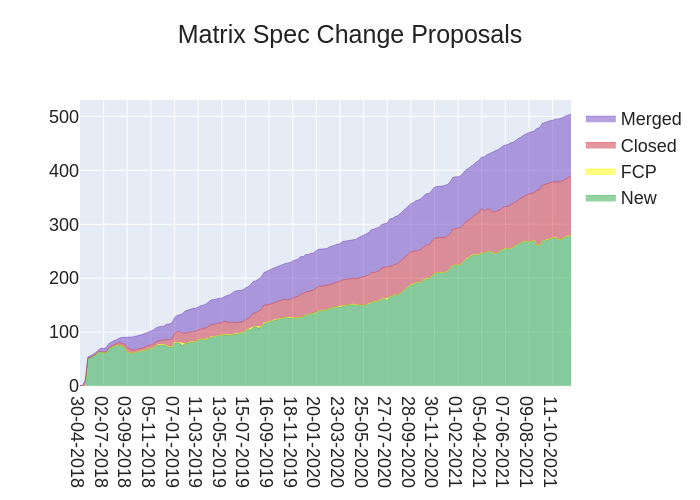
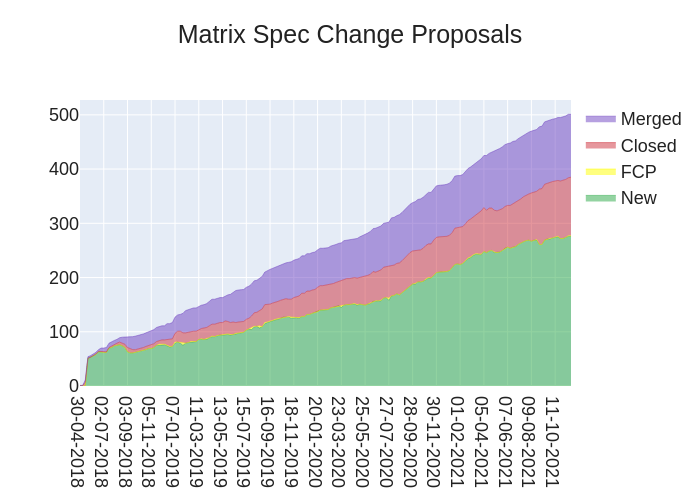
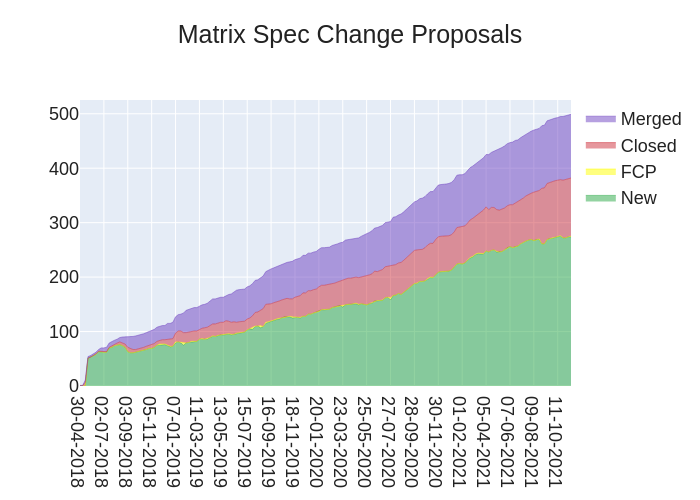
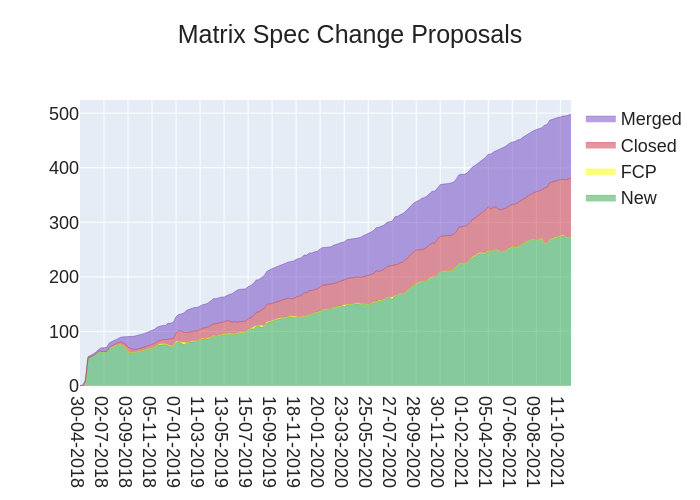
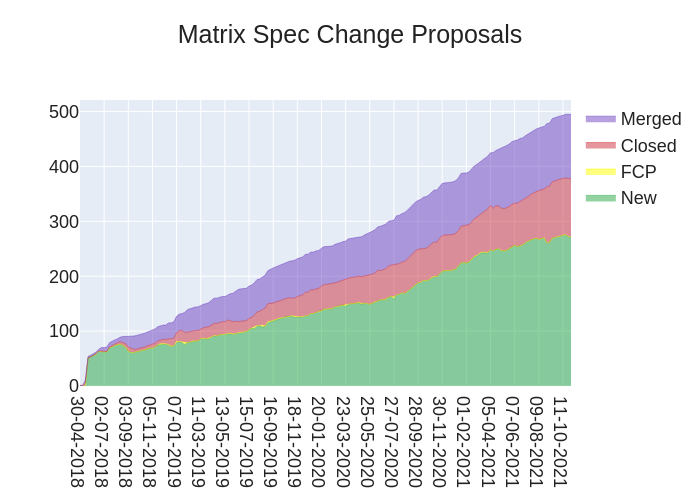
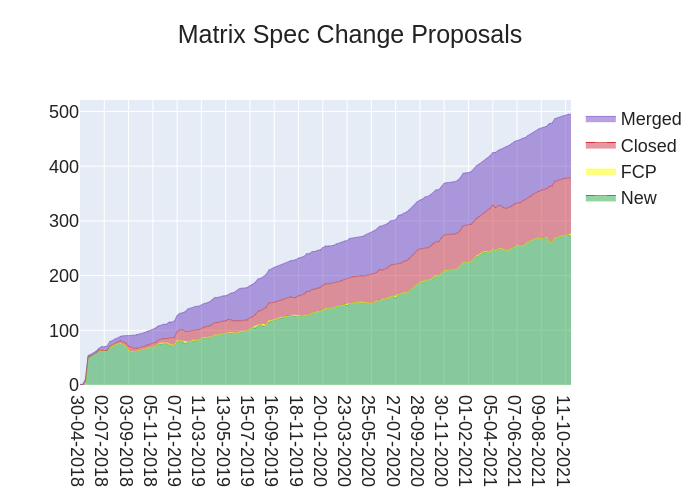
🔗The graph
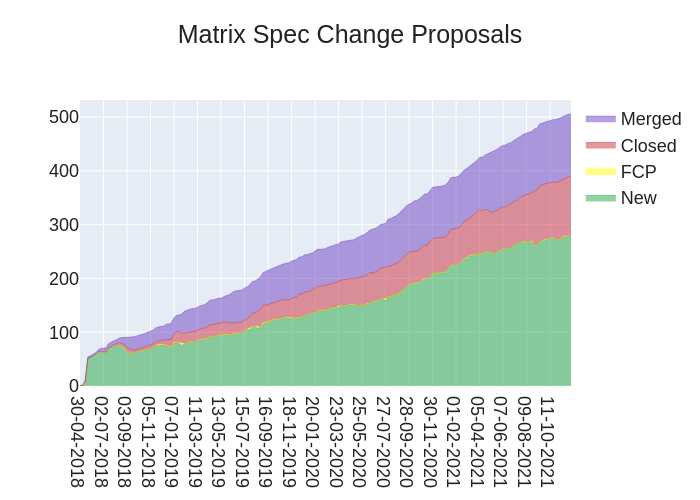
Here's a stacked graph of MSC progress:
Kegan announces
Sliding sync (aka sync v3) is described in MSC3575 - it's still very early days for the proposal which means a lot can change: and YOU can be a part of that. Please take a look at the MSC and provide any and all feedback, be it on the names of keys, format of JSON objects, or the kinds of operations that can be performed. I'm particularly interested in feedback from client developers who have complex room list sort orders or room list filtering requirements and bot/bridge developers who typically don't have a visible room list UI. Any and all feedback at this stage is welcome, visit #sliding-sync:matrix.org to join the discussion.
🔗Dept of Servers 🏢
🔗Synapse (website)
Synapse is the reference homeserver for Matrix
callahad announces
We're back! New year, new release candidate: we published Synapse 1.50.0rc1 today, marking the end of life for our Python 3.6 and PostgreSQL 9.6 support. We've also extracted some shared utilities into their own package, matrix-common, which is used by Synapse, Sygnal, and Sydent.
We'll talk more about what's in 1.50 next week when it formally releases.
The Synapse team is expecting to spend most of January on behind-the-scenes work as we gear up to virtually host FOSDEM again! Members of the team will be presenting two talks this year: Shay on Events for the Uninitiated, and Brendan on Beyond the Matrix: Extend the capabilities of your Synapse homeserver. Check out the full devroom schedule here.
🔗matrix-media-repo (website)
Matrix media repository with multi-domain in mind.
TravisR says
v1.2.9v1.2.10 got released as a maintenance update. With early support for Matrix 1.1, S3 storage classes, and blurhash fixes it's worth the upgrade though there are other goodies - check out the changelog, and report bugs to the issue tracker 🙂
🔗Homeserver Deployment 📥️
🔗Helm Chart (website)
Matrix Kubernetes applications packaged into helm charts
Ananace reports
And as a end-of-year update, my Helm Charts have gotten updated yet again. With element-web ending up on 1.9.8, matrix-synapse on 1.49.2 (and .1 before that), and matrix-media-repo on 1.2.10
🔗Dendrite Helm Chart (website)
Helm Chart to deploy Dendrite on Kubernetes
jonnobrow reports
The first iteration of a Dendrite Helm Chart has been released under the k8s-at-home charts repository. It currently supports a full monolithic deployment and requires minimal configuration to get up and running (just need to generate a matrix key and mount it as per the instructions).
If polylith is your thing then I recommend the chart by S7evinK for now, although it is likely these charts will merge in the future.
The chart and documentation are available here: https://github.com/k8s-at-home/charts/tree/master/charts/incubator/dendrite
🔗Dept of Bridges 🌉
🔗Matrix Webhook Receiver (website)
An add-on for the matrix-appservice-webhooks bridge. Webhooks are essentially web interfaces for applications to "push" data to. The bridge can receive messages in a certain format, which is nice if the notifying app can be configured. Often it cannot.
kim says
matrix-webhook-receiver has hit 1.1.0! Give feedback or talk to us about it over in #matrix-webhook-receiver:matrix.org! 🙂
🔗Features
- Advanced Templating! It is now possible to set
formatandmsgtypebased on arbitrary values from the webhook JSON via Jinja2. Shoutout to qg for suggesting this and giving their feedback!- compatibility with matrix-appservice-webhooks forks that read
avatarUrlinstead ofavatar_url- allow mxc:// URL avatars
- improvements to the GUI, including automatically resizing text areas and msc:// avatar URL preview
- improvements to templates/examples including making use of above features
- more documentation, including Tips & Tricks and Related Projects
🔗Notable Fixes
- ability to properly set no avatar
- work around upstream's newline issue when not using a template
Full Changelog: https://github.com/HarHarLinks/matrix-webhook-receiver/compare/1.0.0...1.1.0
🔗matrix-hookshot (website)
A multi purpose multi platform bridge, formerly known as matrix-github
Half-Shot says
Howdy folks, it is the time of the year where everyone scarpers! Anyway, perfect time to announce that matrix-hookshot has gotten it's first major release!. 1.0.0 is here!
For those not in the know, the hookshot bridge is used to bridge GitHub, GitLab, JIRA and Generic Webhooks into Matrix rooms. It doesn't just bridge into existing rooms, but can also spawn dynamic rooms based on aliases, send you your notifications in a DM and do lots of other wonderful things!
The notable changes from the 0.1.0 release are:
- The bridge has now been renamed from matrix-github to matrix-hookshot.
- Now supports JIRA and Generic Webhooks in addition to GitHub and GitLab.
- Includes new commands and metrics reporting.
- Includes complete documentation.
You can get involved and start playing with it by checking out the release here
And that will be my last TWIM entry of the year. Have a good one and stay safe all 🐶
That was in 2021! Half-Shot is back in 2022 with more news
Hey folks! It was only last year we released the 1.0 release of hookshot, after many years of work to get it that far. I'm happy to announce that this week we've got another release. There are a number of buxfixes and improved documentation pieces landing (special shoutout to HarHarLinks for ensuring the docs are competent). The highlights are as follows:
- Added support for Figma webhooks. this also means the archival of my old project matrix-figma
- Support GitLab wiki page change events.
- Added a new script
validate-configwhich allows you to check your config file for simple errors. Handy for people writing ansible roles!- Add support for a html key on generic webhooks to set the HTML content of a Matrix message.
The project can be found over at https://github.com/Half-Shot/matrix-hookshot/, with pretty pretty docs at https://half-shot.github.io/matrix-hookshot. We're also in #hookshot:half-shot.uk if you prefer using Matrix to learn about these things!
🔗Heisenbridge (website)
Heisenbridge is a bouncer-style Matrix IRC bridge.
hifi announces
Heisenbridge roundup!
Release
v1.8.0v1.8.1v1.8.2v1.9.0 🥳
- Spaces support 🌃
- Sort NAMES reply nicks 🔤
UNPLUMBnetwork command to force unplumbing without being in the room- Proper SASL external with CertFP with mechanism override option (see notes)
- Disconnect and cleanup from networks that have no rooms open ♻️
- Reply (and reject) DM requests to ghosts with
QUERYcommand ↪️- Try to keep IRC users in the room at all costs if they are on the IRC channel
- Fix assumption of all IRC replies to have arguments
- Prevent accidental namespace changes to cause mayhem
- Finally convert from homegrown Matrix API stuff to Mautrix
- Bump Mautrix requirement to 0.12=>0.14
- Conduit support was broken in 1.8.x but fixed again in 1.9.0, sorry
Finally there's network level spaces support with a new
SPACEcommand. This creates a new bridge controlled space for the network and automatically manages rooms in and out. There's an issue/feature with Element that all rooms that have been converted to DMs with/converttodmwill appear in all bridge spaces. The workaround is to convert them back to regular rooms.CertFP SASL has been updated to do SASL external flow by default. If you are upgrading and have used CertFP with OFTC you need to run
SASL --mechanism=nonefor it to connect again.Abandoned networks where the user has left all rooms including the network room will now automatically disconnect and cleanup. This is more in line what people would expect and prevents idle connections from hanging around.
Get your third vaccination from GitHub, PyPI or matrix-docker-ansible-deploy!
Thanks!
🔗Dept of Clients 📱
🔗Nheko (website)
Desktop client for Matrix using Qt and C++17.
Nico announces
We just released 0.9.1!
This is a small bug fix release. If you reported an issue, there is a 15% chance it is fixed now! This release also supports pinned messages, although those will only show up after someone changed the pinned messages in a room currently (we didn't want to force a full resync just for such a small feature). The spaces list is also now nested, Nheko offers you quick access to your recently used reactions and Nheko will show you your direct chats in the sidebar. Apart from that there are quite a few bugfixes and smaller improvements, you can find the full changelog and downloads here: https://github.com/Nheko-Reborn/nheko/releases/tag/v0.9.1
Thank you everyone, who helped shape this release!
Nico reports
Nheko now is a lot more efficient. We now use one Threadpool instead of 3, got rid of more than 60% of the allocations when scrolling through messages, layout half as much content when scrolling, blurhashes decode in 10% of the time and jdenticons allocate ~10% as much temporary buffers. We also deleted around 1000 lines of unused code. Tooltips also shouldn't steal the mouse focus when scrolling anymore, which could lead to sudden stalls when scrolling.
Additionally edits now replace existing notifications, tastytea added a manpage and fixed blurry or incorrectly sized custom emoji, you can now send custom emotes via the inline completer using ~ and completers now show a scrollable list with more Elements than before. Advanced users can also now opt into an insecure client side secrets storage via a hidden setting.
Nico says
We're baaaaack! Anyway, last week Drake just translated all of Nheko into Spanish, you can now zoom in and pan in the image viewer, emojis shouldn't split up into their segments anymore and Nheko should always be sending the qualified version of it (according the to the unicode test files, not by just appending FE0F). Blurhashes should be even faster still and we now have support for running the call event loop on macOS and Windows (although call support is still disabled there for now).
We are also now working to restructure our README. It has a lot of outdated stuff in it and you really want to see screenshots pretty early in the README! You can sneak a peak here: https://nheko.im/nheko-reborn/nheko/-/tree/README_updates
🔗Element (website)
Everything related to Element but not strictly bound to a client
Danielle reports
Welcome to a new year at Element!
Threads
- This week the Threads team has focussed their efforts on improving some of the smaller details and pesky bugs we’ve found in our first rounds of testing.
- If you’d like to help us test Threads we’ll be asking for help in the Community Testing room over the next few weeks. Join#element-community-testing:matrix.org to stay in the loop.
Polls
- Polls is available in Labs on all clients! While we know there are some minor improvements to be made, we’re proud of where we are and would love for you to start using it!
Community Testing
- Our next session will be on Wednesday, 12th January at 16:00 UTC (17:00 CET). We will be testing the new release candidates on all three platforms! Join us at#element-community-testing:matrix.org
🔗Element Web/Desktop (website)
Secure and independent communication, connected via Matrix. Come talk with us in #element-web:matrix.org!
Danielle reports
- Work continues on the integration of PostHog analytics. With your explicit permissions we’ll receive anonymous usage data that will allow us to understand the areas of Element that are helpful (or not). This info will help fuel things like our Information Architecture project.
- In labs (you can enable labs in settings on develop.element.io or on Nightly)
- Information Architecture improvements are still being worked on - try it out by enabling things like the new Spotlight search and Breadcrumbs.
- Message Bubbles are improving; We’ve been hard at work preparing them for a release in the coming weeks.
🔗Element iOS (website)
Secure and independent communication for iOS, connected via Matrix. Come talk with us in #element-ios:matrix.org!
Danielle announces
- During the Christmas break we increase the speed of the app launch by 7x! Once stabilised this update will land with you.
- Analytics changes have been merged into the RC and opt-in will be available soon.
- In development:
- More Spaces improvements are underway; You’ll soon be able to add rooms to Spaces, update room settings, and have room interactions on the ‘long-press’.
- Improved onboarding! We’re hoping to make the first few steps in Element easy by simplifying some of the first tasks users take in the app, including signing up.
- We’ve started building Message Bubbles on iOS. This will help to distinguish the messages you send from the messages you receive.
🔗Element Android (website)
Secure and independent communication for Android, connected via Matrix. Come talk with us in #element-android:matrix.org!
Danielle says
- For Android we now have a PR review board to increase visibility into the state of PRs submitted by external contributors!
- The new Opt-in screen for PostHog analytics tracking will be released soon.
- Work on Message Bubbles has started and we can’t wait to share it with you!
- If you have any feedback or questions about Messages Bubbles, please let us know now.
- We’re also working on improving the sign up and sign in experience with some micro-improvements landing in the product soon.
- We’re sorry for the delay of Element on F-Droid store, it will be available next week.
🔗Dept of Non Chat Clients 🎛️
🔗Populus Viewer (website)
A Social Annotation Tool Powered by Matrix
gleachkr says
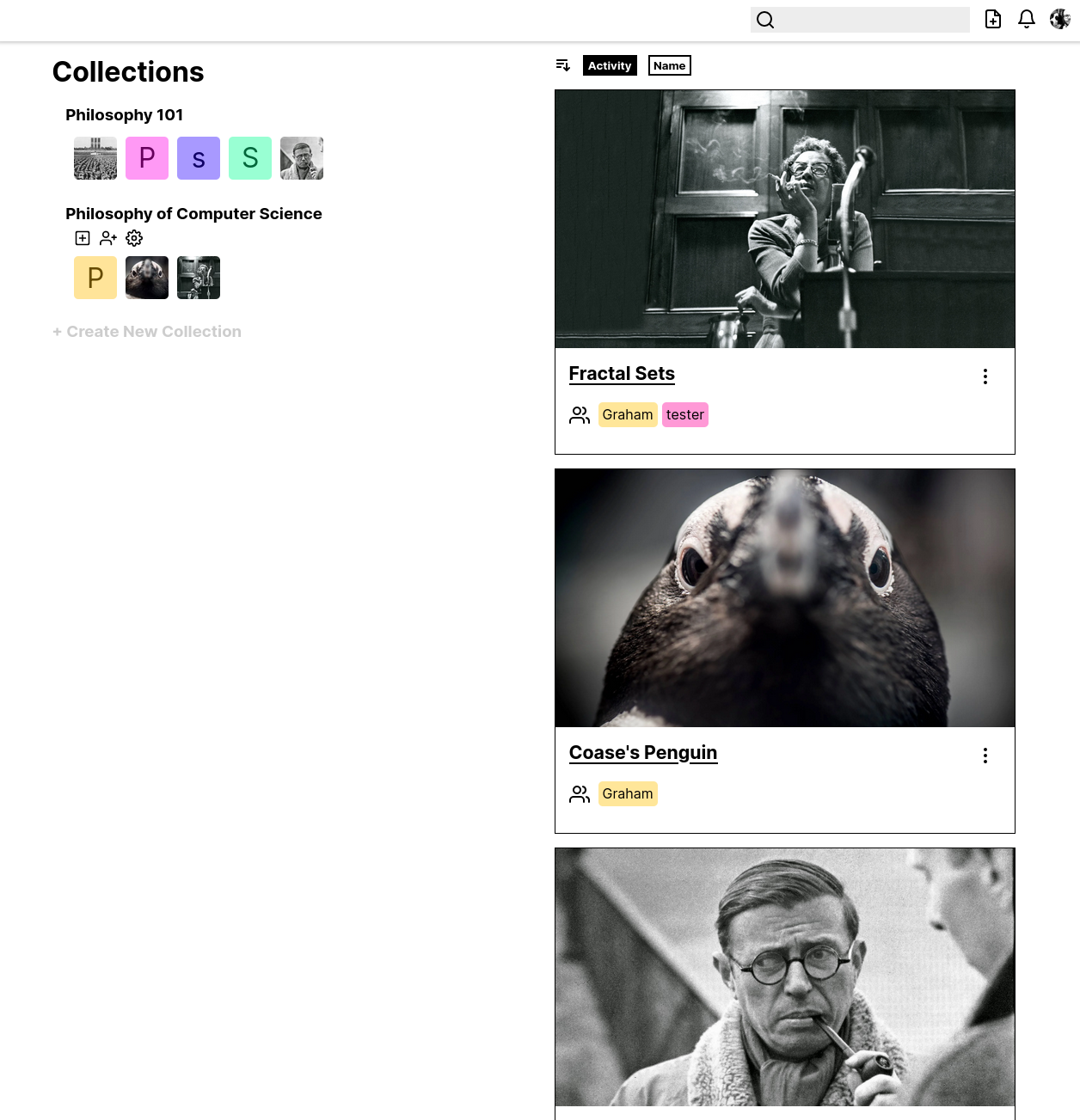
A lot has happened with populus-viewer!
- We now implement MSC2574! This MSC proposes a standard format for marking up resources (PDFs, other document formats, audiovisual media, websites, geospatial data...) using Matrix.
- Room avatars are now displayed in the welcome view for PDF rooms
- There's now a UI for using spaces to manage and share PDF collections
- Reactions now work like element-web: click to mirror an existing reaction or redact your previous reaction
Next, I'm aiming to implement MSC3592, which proposes a standard format for basic markup on PDFs. Stay tuned! And if you're interested in learning more, come visit #opentower:matrix.org.
🔗Matrix Wrench (website)
Matrix Wrench is a web client to tweak Matrix rooms.
ChristianP announces
Matrix Wrench is a web client to tweak Matrix rooms. After formerly calling it Matrix Navigator or Matrix Screwdriver, I finally settled on the name Matrix Wrench.
¯\_(ツ)_/¯Version v0.2.0 comes with a Network Log which displayscurlequivalents for all network requests. It also allows to easily add and remove room aliases. https://gitlab.com/jaller94/matrix-wrench/
🔗matrix-streamchat (website)
Matrix powered stream overlay for OBS, to integrate live chat in your favorite (selfhosted) streaming setups.
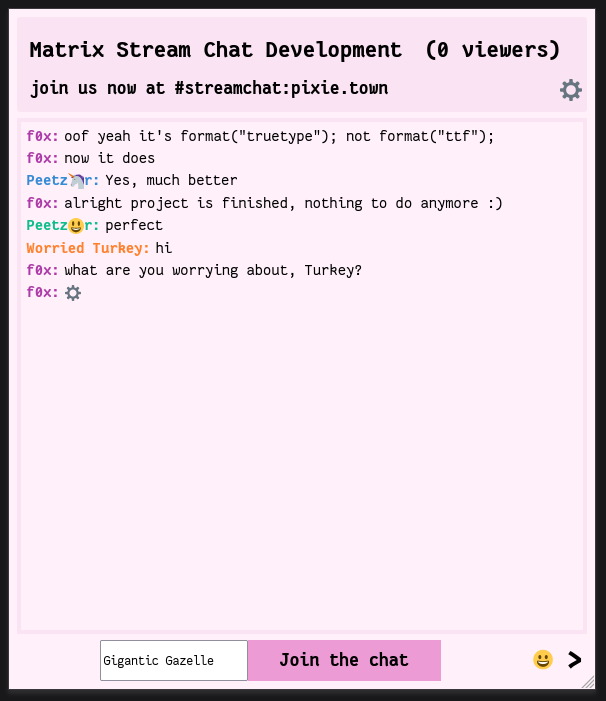
f0x says
there's a pink theme and irc styling for matrix-streamchat now
🔗Cactus Comments (website)
Cactus Comments is a federated comment system for the web, based on the Matrix protocol.
Asbjørn reports
Cactus Comments is a comment system for the open web, built on Matrix.
We released version v0.11.0 of the client!
The client has been relicensed to LGPL. This means that you can now use Cactus Comments in non-GPL compatible projects. But mainly, this release brings a bunch of CSS improvements: introducing automatic dark mode, and making it easier to change colors with CSS variables.
Here's the changelog:
- Relicense from GPLv3 to LGPLv3.
- Rewrite large parts of the stylesheet to use flexbox.
- Introduce CSS variables to the stylesheet.
.darkand.lightCSS classes with default values for dark/light mode.- Bugfix: "View More" button no longer blinks when auto-refreshing short comment sections.
v0.11.0 changelog and IPFS links here.
/ipns/latest.cactus.chat is updated to point to the latest release, so sites linking there should already be using the new version.
Try out a live demo: cactus.chat/demo
Join our Matrix room: #cactus:cactus.chat
🔗Dept of SDKs and Frameworks 🧰
🔗simplematrixbotlib (website)
simplematrixbotlib is an easy to use bot library for the Matrix ecosystem written in Python and based on matrix-nio.
krazykirby99999 reports
Happy New Year!
Since the last post of TWIM, versions 2.5.1 and 2.6.0 of simplematrixbotlib were released.
🔗Version 2.5.1 Released!
🔗New Fixes:
- Fixed #101 'Api' object has no attribute 'async_client'
🔗Version 2.6.0 Released!
🔗New Features:
- A listener for handling m.reaction events has been added. Bot developers can now use
Listener.on_reaction_eventto smoothly handle reactions.Example usage is shown below:
""" Example Usage: random_user !echo something random_user2 *reacts with 👍️ echo_reaction_bot Reaction: 👍️ """ import simplematrixbotlib as botlib creds = botlib.Creds("https://example.com", "echo_reaction_bot", "password") bot = botlib.Bot(creds) @bot.listener.on_reaction_event async def echo_reaction(room, event, reaction): resp_message = f"Reaction: {reaction}" await bot.api.send_text_message(room.room_id, resp_message) bot.run()Request additional features here.
Source: https://github.com/KrazyKirby99999/simple-matrix-bot-lib
Package: https://pypi.org/project/simplematrixbotlib/
Documentation: https://simple-matrix-bot-lib.readthedocs.io/en/latest/
Matrix Room: https://matrix.to/#/#simplematrixbotlib:matrix.org
🔗matrix-bot-sdk (website)
A TypeScript/JavaScript SDK for Matrix bots
TravisR announces
matrix-bot-sdk has had a v0.6.0-beta.3 release with beta support for crypto! It even includes documentation!
The crypto is considered beta quality at the moment: good enough to use for somewhat unimportant bots, but not fully recommended for production just yet. With that being said, I'm interested in bugs you run into - please use the issue tracker if you run into crypto not working.
Tutorials for the crypto setup are at https://turt2live.github.io/matrix-bot-sdk/tutorial-encryption.html
Note for appservice support to work then you'll need a Synapse with these PRs enabled (may require manual merge too):
- https://github.com/matrix-org/synapse/pull/11538
- https://github.com/matrix-org/synapse/pull/11617
- https://github.com/matrix-org/synapse/pull/11215
For non-linux platforms, the rust-sdk will try to build itself which means you might need a working Rust stack. The Rust SDK repo itself has more information:
- https://github.com/matrix-org/matrix-rust-sdk/blob/travis/node-bindings/crates/matrix-sdk-crypto-nodejs/README.md
- https://github.com/matrix-org/matrix-rust-sdk/blob/travis/node-bindings/README.md
Bots and appservices don't automatically support encryption, but adding encryption should be easy. The Rust SDK dependency is required in either case, sorry.
🔗Complement (website)
Matrix compliance test suite
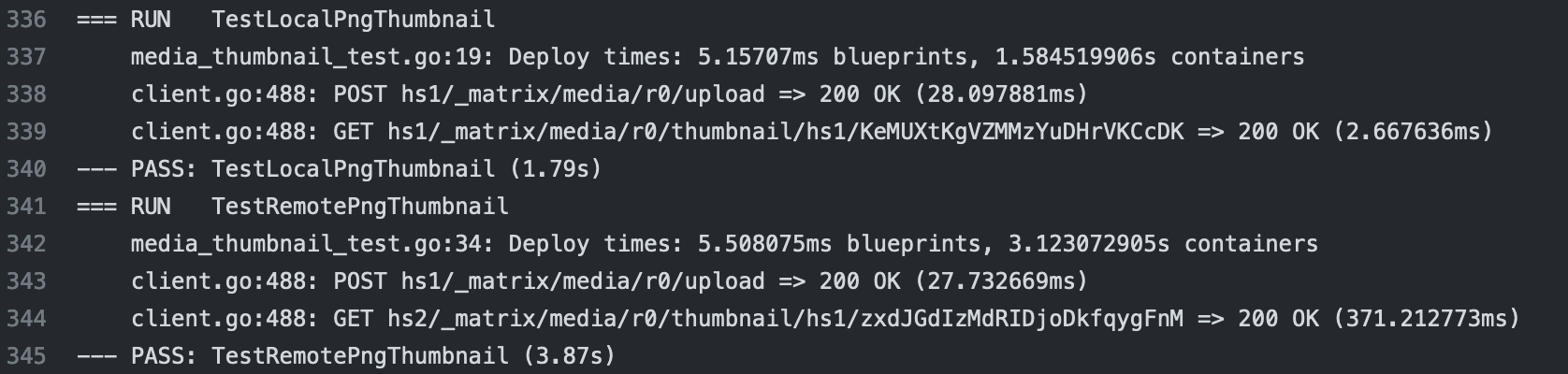
Kegan reports
Complement has seem some updates this week in the test output that is produced onto the CLI. Details on how to add this to your CI process are contained in the README. Here's the difference when viewed using Github Actions:
Before:
After:
🔗Polyjuice (website)
Elixir libraries related to the Matrix communications protocol.
uhoreg reports
Polyjuice Newt, the newest addition to the Polyjuice project, is an Elixir binding for vodozemac, the new Olm/Megolm implementation in Rust. At the time of writing, Polyjuice Newt supports encryption and decryption using Olm and Megolm, but by the time you read this next year, it may also support the SAS verification functions and pickling/unpickling.
🔗Dept of Ops 🛠
🔗NixOS Deployment (website)
Matrix packaging for NixOS
piegames announces
I don't think we've previously had any Nix/NixOS/nixpkgs related entries in TWIM, so I'll start ^^
The current unstable channel has extended its Matrix ecosystem support to also include Heisenbridge and Conduit packages and modules. This makes it super easy to deploy any of those services: For example, my configuration for Heisenbridge is 21 lines long, and Conduit is only 11 lines. You can browse the available configuration options online:
services.matrix-conduit,services.heisenbridge(note that some of them are freeform and simply forward to the upstream configuration).For those that are not into NixOS, a module is the code that turns the declarative configuration files into your running system setup. As an example, if you enable
services.heisenbridgethe following things are done for you:
- Create a new
heisenbridgeuser and group for the service- Create and manage the registration file for the homeserver (i.e. automatically regenerate it after the configuration changed)
- Create a systemd service that runs the
heisenbridgecommand with the requested bridge configuration. The unit also sets a few systemd security hardening options.For support, join our Matrix space at #community:nixos.org and its Matrix-Nix channel: #matrix-nix:transformierende-gesellschaft.org
🔗matrix-docker-ansible-deploy (website)
Matrix server setup using Ansible and Docker
Slavi says
Thanks to Aine of etke.cc, matrix-docker-ansible-deploy can now help you set up Honoroit - a helpdesk bot.
See our Setting up Honoroit documentation to get started.
Slavi says
Thanks to Aine of etke.cc, matrix-docker-ansible-deploy now supports Cinny - a new simple, elegant and secure Matrix client.
To try it out, see our Setting up Cinny documentation page.
Slavi announces
At matrix-docker-ansible-deploy, we believe that 2022 will be the year of the non-Synapse Matrix server!
Jip J. Dekker did the initial work of adding Dendrite support to the playbook back in January 2021. Lots of work (and time) later, Dendrite support is finally ready for testing.
The playbook was previously quite Synapse-centric, but can now accommodate multiple homeserver implementations, with Synapse still remaining the default.
To learn more, see our changelog entry about Dendrite.
Slavi announces
Thanks to Matthew Cengia and Shreyas Ajjarapu, matrix-docker-ansible-deploy can now bridge to Twitter using the mautrix-twitter bridge.
Note: the playbook already supports another Twitter bridge - mx-puppet-twitter.
To get started with this bridge, see Setting up Mautrix Twitter bridging in our documentation.
This brings the total number of bridges supported by the playbook up to 22. See all supported bridges here.
🔗matrix-commit (website)
A Github Action for sending messages to a Matrix Room.
krazykirby99999 says
🔗Version 1.2.2 Released!
A Github Action for sending messages to a Matrix Room. Changes should apply automatically if you are using tag
v1.🔗New Features:
- Link to repository added
- Link to commit added
🔗Before:
🔗After:
🔗Dept of Guides 🧭
Austin Huang says
A new Matrix guide has come into town: https://joinmatrix.org
In the hopes to expand Matrix's reach to the non-technical population, this guide is intended to give quick directions on how to use Matrix, as well as clear comparison between Matrix and other dominant platforms.
The pages are available on GitHub. Open to contributions!
🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server.
🔗#ping:maunium.net
Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | envs.net | 599.5 |
| 2 | thomcat.rocks | 768 |
| 3 | matrix.spooks.cyou | 862 |
| 4 | matrix.nicfab.it | 955 |
| 5 | aria-net.org | 1300 |
| 6 | aletheia.moe | 1611.5 |
| 7 | trygve.me | 1617 |
| 8 | mtx.koyax.org | 1703.5 |
| 9 | rollyourown.xyz | 1808 |
| 10 | microelectro.de | 1996 |
🔗#ping-no-synapse:maunium.net
Join #ping-no-synapse:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | matrix.spooks.cyou | 366 |
| 2 | dendrite.matrix.org | 440 |
| 3 | sspaeth.de | 466 |
| 4 | rustybever.be | 546.5 |
| 5 | grin.hu | 966 |
| 6 | matrix.awesomesheep48.me | 1294 |
| 7 | dendrite.neilalexander.dev | 1537 |
| 8 | dendrite.beckmeyer.us | 1744 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!