This Week in Matrix 2022-07-22
2022-07-22 — This Week in Matrix — ThibLast update: 2022-07-22 18:39
🔗Matrix Live 🎙
An episode with the maintainers of Threematrix, the 100% Rust bridge between Matrix and Threema!
In addition to that, Open Tech Will Save Us will be back on Wednesday 27 at 16:00 UTC! The topic will be "what makes a platform", or more specifically: "are Linux or the web platforms". There are many fascinating topics to discuss, such as "is it possible to create an app for Linux" (it's not as simple as it sounds), "why are some people against theming?", or "why do developers want to use platforms".
And to answer that, who other than the Linux desktop most advanced projects GNOME and KDE, and people working on Matrix, the protocol that wants to become as unmissable as the web itself, and more specifically on a deeper integration of widgets with Matrix clients?
You can join #otwsu:matrix.org to ask your questions on July 27 during the live show, and bookmark either https://stream.matrix.org or the YouTube stream.
🔗Dept of Spec 📜
Andrew Morgan (anoa) says
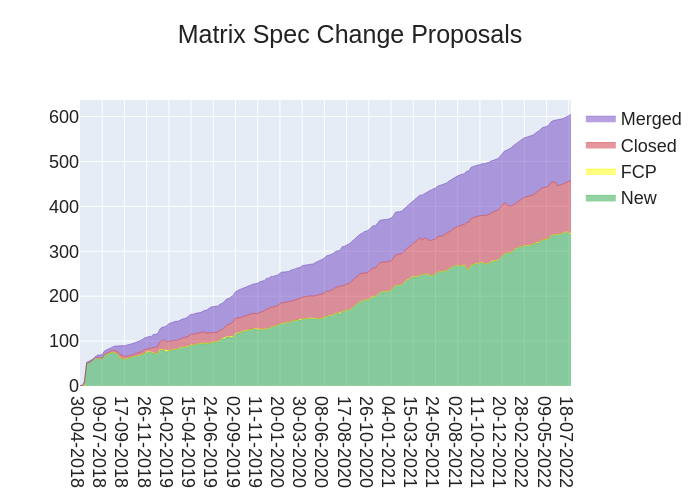
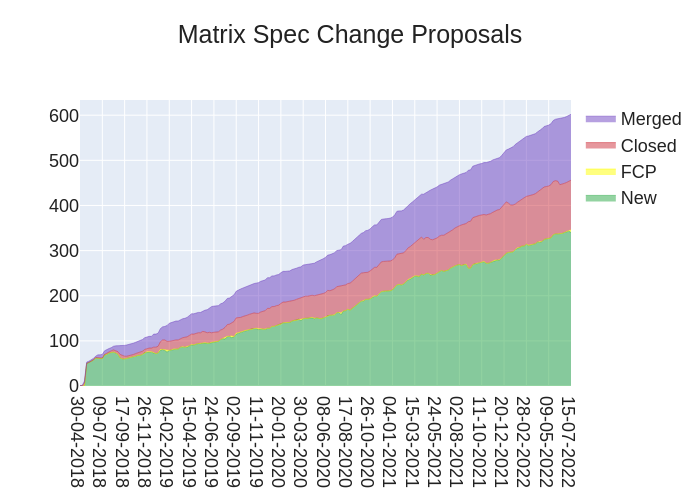
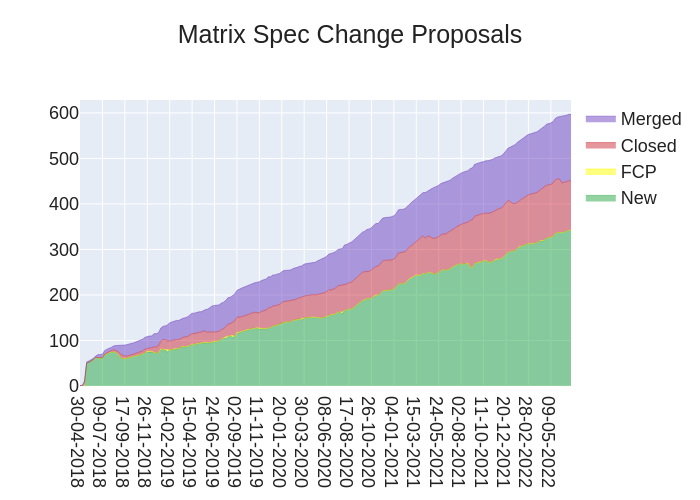
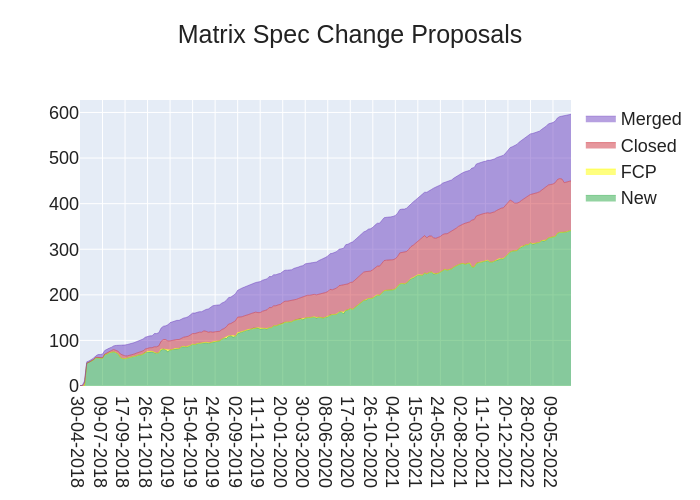
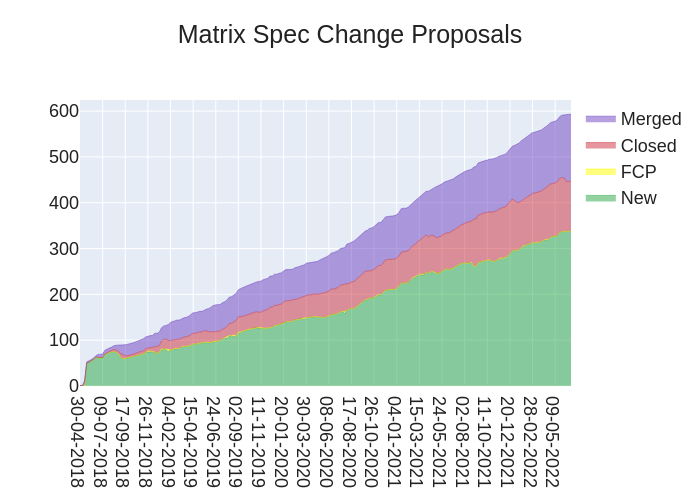
Here's your weekly spec update! The heart of Matrix is the specification - and this is modified by Matrix Spec Change (MSC) proposals. Learn more about how the process works at https://matrix.org/docs/spec/proposals.
🔗MSC Status
MSC status updates from the past week!
New MSCs:
- MSC3852: Expose user agent information on
Device- MSC3851: Allow custom room presets when creating a room
- MSC3849: Observations and Reinforcement
- MSC3848: Introduce errcodes for specific event sending failures
MSCs in Final Comment Period:
- MSC3844: Remove unused policy room sharing mechanism (merge)
- MSC3828: Content Repository CORP Headers (merge)
- MSC3827: Filtering of
/publicRoomsby room type (merge)- MSC2153: Add a default push rule to ignore m.reaction events (close)
Accepted MSCs:
- MSC3786: Add a default push rule to ignore
m.room.server_aclevents- MSC3267: Reference relations
- MSC2832: HS -> AS authorization header
- MSC2676: Message editing
- MSC2285: Private read receipts
Closed MSCs:
Merged MSCs:
- No MSCs were merged to the spec this week.
🔗Spec Updates
Lots of MSCs moving through the pipeline in the last couple weeks! As always, be sure to take a look at those in Final Comment Period above - only a few days left to comment on them before they merge/close!
Otherwise the Spec Core Team is looking to try and get a handle on the current MSC backlog - this means taking a look at all of the open MSCs, triaging them and organising them into a loose priority queue. This is likely to take quite a while to do and may not ever be complete - but should give us and everyone else an idea of what's expected to land in upcoming Matrix spec versions.
🔗Random MSC of the Week
The random MSC of the week is... MSC3217: Soft kicks!
The idea this MSC proposes is to add a possible
m.softkickfield to room membership events of type "leave", which if present will inform clients that the user has only been kicked temporarily, and they are welcome to rejoin.This helps with the IRC bridging use case laid out in the MSC.
ChristianP says
🔗Offline Matrix Spec for Dash and Zeal
I use Zeal – an offline documentation browser using the same docsets as Dash for MacOS. It allows me to browse MDN, ExpressJS docs, NodeJS docs and other languages and formats while not relying on the Internet when traveling. They have "208 awesome docsets", and I guess you know which one I'm missing – or used to miss, until I packaged it myself.
Introducing: The Matrix Spec for Dash and Zeal
If you use Dash or Zeal, give it a try. Let me know, if you find pages that are not working. I hope that Matrix will be included in their list of user-contributed docsets.
Note, this is not an official release distribution of the Matrix Spec. Enjoy at your own risk of this breaking or not getting updated.
🔗Dept of Servers 🏢
🔗Construct Server
Jason Volk says
Construct server has been refurbished to support the Ubuntu 22.04+ platform. I am happy to report that Construct performs faster and more reliably than ever before. It's been a long time since the last update due to COVID-related health problems, but development has picked up again. I'd like to thank @manu_kamath:matrix.org and @uis246 for their contributions, and of course Yan Minari for keeping things together over the past year. Additional work implementing the latest MSC's will continue in the coming weeks so I encourage everyone to show support in #construct:zemos.net and contribute if possible.
Several enhancements have taken place this release, so I'd just like to highlight one here: The media database has been eliminated and has been integrated into the main events database. Construct did always store media in rooms by splitting files into blocks, but it offloaded the content block to separate storage leaving just a hash of the content in the matrix event. Construct now stores blocks directly in event content via hardware-accelerated base64 encoding. The result performs better because there's only one database query instead of two, and the room can be shared between servers in a Construct Cluster.
Construct is a performant and robust Matrix Server and Natural Language Processor. Please be mindful of any laws in your country which require registering your instance for commercial use.
🔗Synapse (website)
Synapse is a Matrix homeserver implementation developed by the matrix.org core team
Brendan Abolivier announces
This week we've released Synapse 1.63! This release includes a few features such as better rate limiting for invites, as well as experimental support for MSC3827 which allows filtering public room search results by room type. The latter will, once stabilised, allow for better discoverability of public spaces since it will allow clients to specifically look for them. Read all about this new release on the matrix.org blog: https://matrix.org/blog/2022/07/20/synapse-1-63-released
We've also spent some time clarifying documentation and prompts about the usage statistics Synapse automatically reports if configured with
report_statsset totrue. The new documentation page lists exactly what is reported and how this reporting works. This clarification work included removing the use of "anonymised" when referring to this feature to make it clearer that, even though Synapse does not report identifiable information about users and rooms, it does report the homeserver's name (i.e. the value of theserver_nameconfiguration setting).
🔗Homeserver Deployment 📥️
🔗Helm Chart (website)
Matrix Kubernetes applications packaged into helm charts
Ananace says
Since people seemed to like seeing updates on my Helm Charts; matrix-synapse got bumped to 1.63.0 and then 1.63.1, as well as receiving some expanded handling of workers - all worker instances now come with both startup- and liveness probes attached by default.
🔗Dept of Bridges 🌉
🔗Threematrix (website)
A bridge to the Threema messenger
Moritz Stückler says
Say hello to a new bridge in Matrix universe (or rather fediverse): Threematrix. As you might've guessed from the name: It's a bridge between the Threema messenger and Matrix. Threema is a very popular messenger in europe, especially in German speaking countries (it's a swiss company). We've just released our very first alpha version – it's a very simple bot bridge for now, but we have quite a lot of improvements on our todo list. Currently, it only works with the (paid) Threema Gateway API product, but we're trying to talk to Threema to come up with a more affordable hobbyist pricing model for bridge use. Feel free to follow our releases in the GitHub repo, follow our Mastodon account and join our Matrix room to stay up to date or ask any questions.
P.S.: We're two freelance developers and we're being funded by the German Prototype Fund program. If you're an OSS developer in Germany, check them out!
🔗matrix-hookshot (website)
A multi purpose multi platform bridge, formerly known as matrix-github
Andrew F says
Hookshot 1.8.1
Hello all -- since our last TWIM announcement, Hookshot has been updated from 1.7.2 to 1.8.1. Aside from usability fixes and documentation improvements, there have been some notable changes to generic webhook support:
- XML webhook payloads are now decoded instead of being treated as blobs of text. This means they render more nicely as room messages, and more importantly, it allows them to work with custom JavaScript transformations. (#410)
GETrequests for generic webhooks are no longer supported by default. For details, refer to the documentation. (#397)As usual, visit #hookshot:half-shot.uk to follow the development in real-time.
🔗Dept of Clients 📱
🔗Quadrix (website)
A Minimal, simple, multi-platform chat client for the Matrix protocol.
JFA says
Quadrix v1.2.2 is now available for Linux (https://snapcraft.io/quadrix, https://flathub.org/apps/details/chat.quadrix.Quadrix) and Android (https://play.google.com/store/apps/details?id=chat.quadrix.android). Other platforms will soon follow.
New in this release:
- Spanish translation!!!
- Fix for the Jitsi Meet link displayed to non-Quadrix users (thanks to @alpabrz:matrix.org)
Please leave feedback/comments at #quadrix:matrix.org or in the issues at https://github.com/alariej/quadrix (stars welcome :-)
🔗Nheko (website)
Desktop client for Matrix using Qt and C++17.
Nico reports
I got a fantastic release for you to day and it won't fit inside a normal sized update so without further ado, here are the highlights:
- Notification counts 💯 (LorenDB, d42)
- You can now see notification counts in more spaces, like your task bar or in the community sidebar.
- For better work-life balance you can hide the notification counts on a per space basis.
- For notification counts in the task bar your desktop environment needs to support the Unity protocol.
- Notifications are also preserved across restarts now.
- Moderation 👮♀️
- You can now change the permissions and aliases of a room.
- Permissions are shown in the Memberlist
- A new
/redactcommand to redact an event or all messages by a user.- You can now provide a reason when inviting, knocking, kicking and banning users.
- Faster startup ⚡
- On at least some systems startup should now be instant even with thousands of rooms.
- Encryption improvements 🛡️
- Support for the most recent changes to Matrix E2EE including fallback keys, no longer relying on the sender_key.
- Compatibility and stability improvements when dealing with different base64 encodings and when verifying users and devices.
- Fetch the whole online key backup at the click of a button.
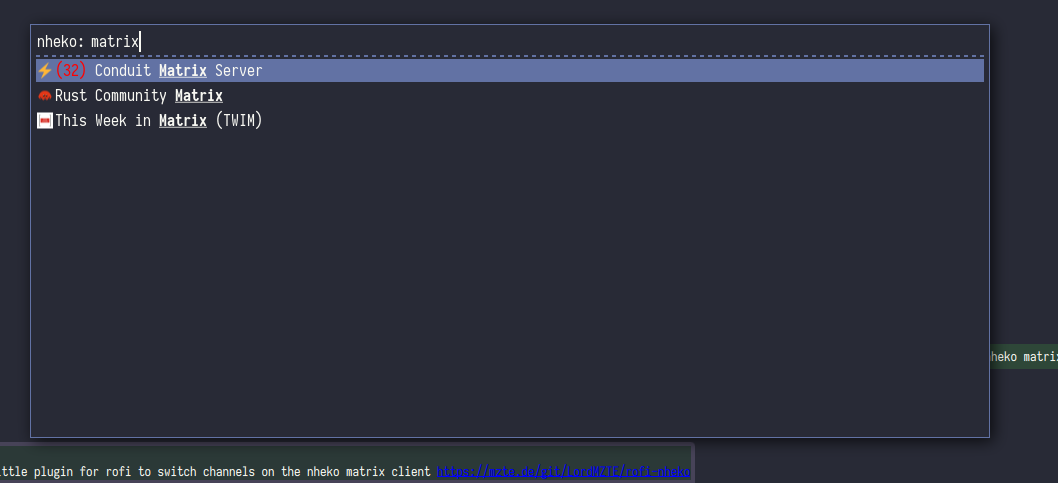
- Integration with external apps 🗺️ (LorenDB)
- Nheko now has a D-Bus API, which you can enable in the settings menu.
- This allows applications like KRunner or Rofi to list and switch between rooms.
If you are reading this a bit early, the release builds might still be cooking, but they should be available in the next few hours. There about 40 more features and at least 30 bugfixes waiting for you, so checkout the release here: https://github.com/Nheko-Reborn/nheko/releases/tag/v0.10.0 . I'd like to thank as always everyone who contributed to this release, it has been a pleasure to work with you folks and I hope I will see a few of you in the next release as well.
As you might be able to tell, moderation features were a big topic this release. But they are clearly not done yet and I expect more of those to land in the future now that Nheko is fairly mature. There are also a few other cool features planned, so while this release is exciting, there will always be more! Same bad client, same bad... wait, this is not my outro!
Please give this release a whirl and tell us how you like it in #nheko:nheko.im!
🔗Element Web/Desktop (website)
Secure and independent communication, connected via Matrix. Come talk with us in #element-web:matrix.org!
kittykat says
- We’ve made more improvements to the new search
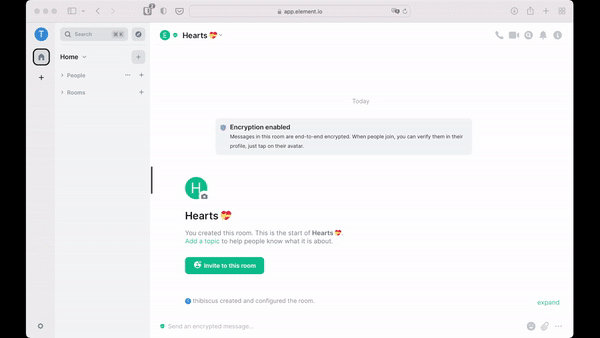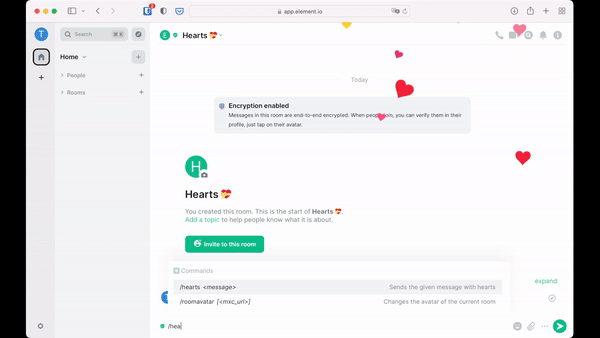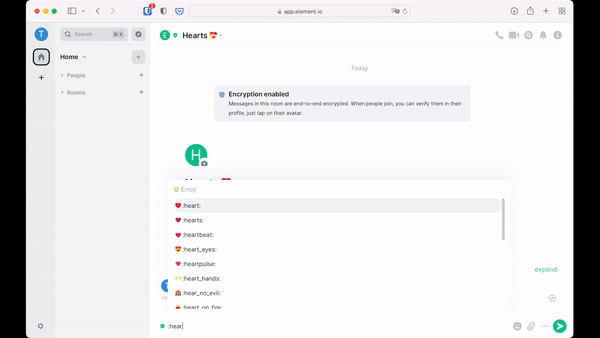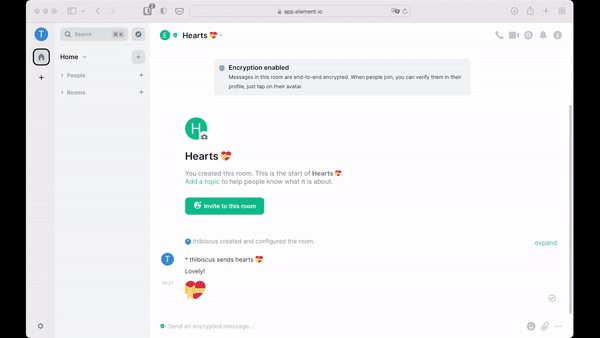
- Added a new emoji effect for 💝 which you can also send with a
/heartscommand in the composer- CicadaCinema and luixxiul have submitted more layout polishes to the app
- Frequently used emojis will appear at the top of the autocomplete suggestions in the composer
- Meanwhile, work continues on message favouriting and live location sharing
- Lazy Loading tests have now been migrated to Cypress. We are coming closer to finishing porting.
- Code style guide is now in final commenting period
- This week’s release (1.11.1) has been delayed until next Tuesday while we fix some last minute issues
🔗Element iOS (website)
Secure and independent communication for iOS, connected via Matrix. Come talk with us in #element-ios:matrix.org!
Ștefan announces
- Version 1.8.23 (with in-app notifications!) is now available on the AppStore
- The new first time user experience is getting very close to release
- Good progress is continuing to be made on the new home screen layout
- We can now silence unwanted push notifications, dare I say, finally!
- We have started experimenting with adopting Sync V3 in ElementX
- And, as always, we have fixed various bugs including edited messages not showing the right text
🔗Element Android (website)
Secure and independent communication for Android, connected via Matrix. Come talk with us in #element-android:matrix.org!
benoit announces
- Release 1.4.28 has been dropped, to give us time to fix the regression and performance issue added when key share history was worked on. The next RC 1.4.30 will be done next week as usual.
- We have started to work on using the new Realm Kotlin SDK (we are using the legacy Java SDK at the moment): it should improve the stability of the app (and so the crash free session) and improve devX. Nearly all the possible blocking points have been handled. This will force us to use suspend methods, which will be useful for ElementX.
- Latest tweaks on FTUE have been merged on develop. We will iterate on a few things, but we are close to releasing the feature! New wordings for FTUE are waiting for translations on Weblate. Thanks to all the contributors!
- We have set up a nightly build using Firebase app distribution. We keep it internal for the moment, we will see in the future if we want to open it to the community.
🔗Open Super dApp (Android)
Brendan A. Miller reports
New project!
open-super-dapp-androidis a fully open source, open standard, decentralized "super app" including a secure, encrypted Matrix compatible messenger based off of the Element Messenger, and an Ethereum crypto wallet and web3 browser based off of Alpha Wallet. Our mission is to foster, and provide access to, a decentralized and secure digital commons for all. Github repo: https://github.com/2gatherproject/open-super-dapp-androidOSD is a downstream project of Element, aiming to provide the functionalities of a "super app" like WeChat, just as an open, distributed and not-for-profit app instead of a proprietary, closed and for-profit one.
This software is pre-alpha, actively seeking contributors, donors and maintainers/leaders. Get in on the ground floor and help build something amazing!
Currently, Open Super dApp builds and runs with full functionality of the Element messenger and Alpha Wallet in the same Android app, with all existing tests passing. Efforts to further integrate their functionalities are just beginning.
Next steps include:
- Demonstrate easy to use person to person Ethereum payment functionality between Matrix users.
- Provide a powerful and easy to use messaging and payment javascript API for use by web3 applications accessed through the Open Super dApp. Produce sample web dApps using this API.
- Centralize cryptographic secrets between the wallet and the messenger.
- Build a parallel iOS version for iPhones using Element iOS and Alpha Wallet iOS.
🔗Dept of SDKs and Frameworks 🧰
tusooa says
We released 0.2.0 of libkazv. Change log is as follows:
- Support streaming uploads. https://gitlab.com/kazv/libkazv/-/merge_requests/1
- Fix ctx.dispatch() returning promises resolving to empty EffectStatus. https://gitlab.com/kazv/libkazv/-/commit/c7796a6ab8325773bf47fe83254a377204d6abcf
- Prevent leaking full file path when uploading to matrix server by using only basename for the request.
- Deal with timeline gaps properly. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/1
- Record state events in timeline. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/2
- Add support for streaming download. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/3
- Add support for Boost.Serialization. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/4
- Support encrypted attachments. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/5
- Allow custom random generator with crypto. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/6
- Support auto-discovery. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/12
- Support profile API. https://lily.kazv.moe/kazv/libkazv/-/merge_requests/13
- Support kick/ban API. https://lily-is.land/kazv/libkazv/-/merge_requests/15
- Support room heroes. https://lily-is.land/kazv/libkazv/-/merge_requests/16
- Add coverage report. https://lily-is.land/kazv/libkazv/-/merge_requests/17
🔗Deprecated
makeDefaultEncryptedSdk()is now deprecated. UsemakeDefaultSdkWithCryptoRandom()instead.
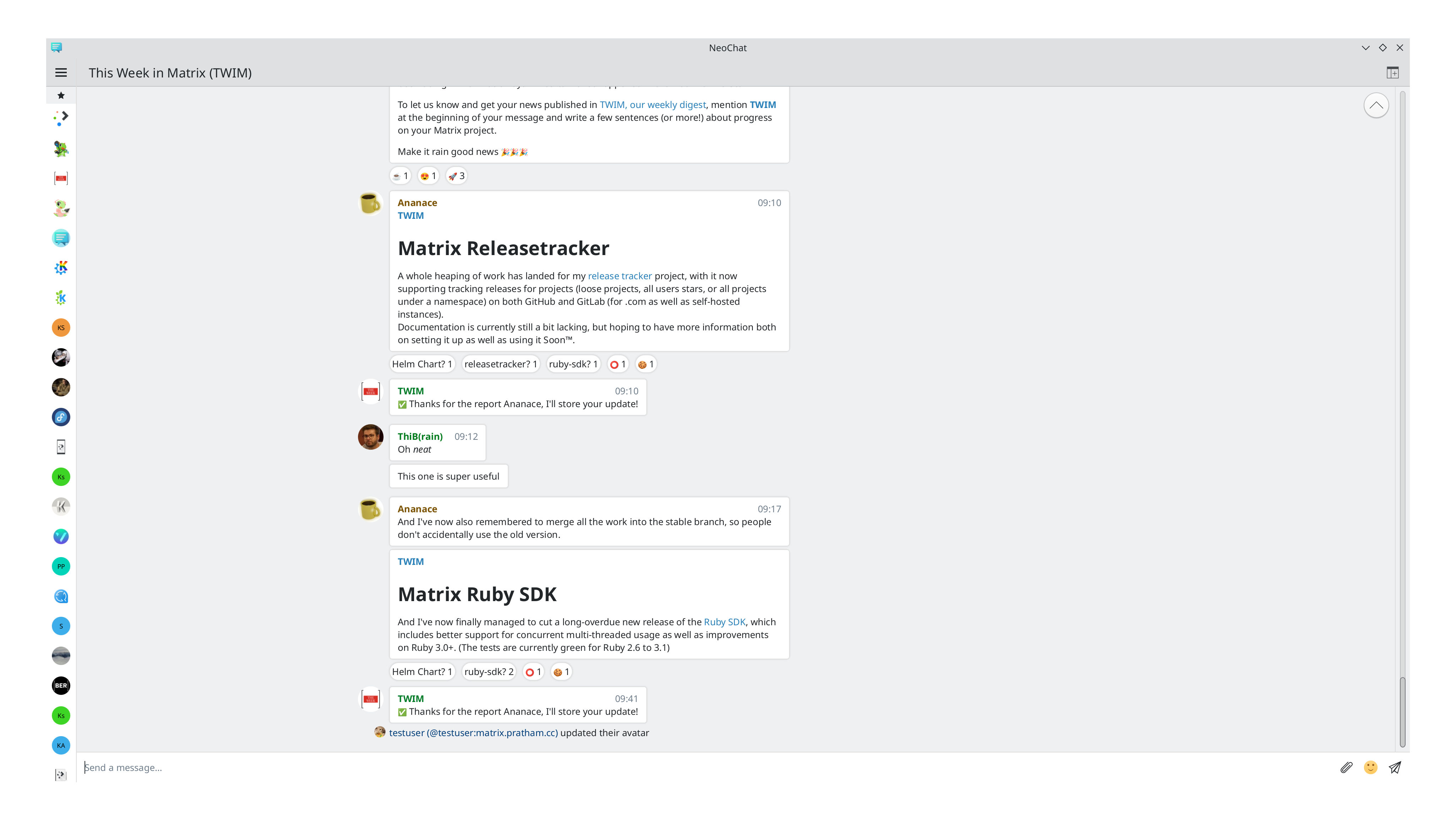
🔗matrix-rust-sdk (website)
Matrix Client-Server SDK for Rust
ben says
This week has seen an merges of many minor, partially longer-pending PRs into the mainline code base: among them a fix for a longer pending CI problem with Apply builds, an update to latest ruma and many minor fixes and style improvements. We've also gotten the Crypto-bindings for the JS in web using WASM a lot further, the only thing remaining for a release are some last minute PRs and fixes in the release infrastructure. But the most changes to the code base this week have been coming from the appservice department, who've submitted, reviewed and merged a whopping seven PRs this week, fixing various problems and adding a bunch of appservice specific features.
Beyond purely code changes this week has seen a lot of project starts, too: For ones, with the help of the rust team, the iOS Team has started integrating the Sliding-Sync/Sync V3 into the upcoming Element-X-Series; the team has put up the first PR to add integration tests against an actual synapse server (some issues pending); a workshop set out the first ideas for the new upcoming timeline API; and a very interesting draft PR was brought in from community member docweirdo proposing a new API on top of the existing SDK to have futures wait for actual completion - no more sending a message and observing sync for the appropriate response yourself.
👉️ Wanna hack on matrix rust? Go check out our
help wantedtagged issues and join our matrix channel at #matrix-rust-sdk:matrix.org.
🔗Dept of Ops 🛠
🔗Synatainer (website)
Synapse Maintenance Container – Docker container with tools for synapse & postgres database maintenance
saces reports
Synatainer v0.4.1-RC1
Synapse Maintenance Container – Docker container with tools for synapse & postgres database maintenance
A lot of things added and changed, and I'm sure I missed something, so I will go with a release candidate this time
New in v0.4.1-RC1
- enable PGPASSFILE support for better database password handling
- add tools to detect and maybe fix synapse issue 12507 and 13026 (No state group for unknown or outlier event)
- internal: added an extension for mautrix-go to serve synapse admin api requests
- lots of iternal changes
stuiis a typical golang binary, it's also available as stand alone version from the release pageTools for
No state group for unknown or outlier event[docker run -it --rm registry.gitlab.com/mb-saces/synatainer:0.4.1-RC1] stui 12507 --help [docker run -it --rm registry.gitlab.com/mb-saces/synatainer:0.4.1-RC1] stui 13026 --helpThe tools scan the database for the issues and tells you which rooms are affected. Adding the
--fixoption, itdestroys your databasedeletes the bogus extremeties. Use at your own risc. And make a backup.The doc have still a lot of space for improvements…
Start the container without command and let do its magic :)
What it does by default:
- daily:
- purge all rooms without local members
- run the state autocompressor (500/100)
- weekly:
- delete old remote media (>90 days)
- delete old message history from public joinable rooms (>180 days)
- monthly:
- vacuum the database
Source: https://gitlab.com/mb-saces/synatainer
Room: #synatainer:c-base.org
🔗matrix-docker-ansible-deploy (website)
Matrix server setup using Ansible and Docker
Slavi reports
Thanks to Stuart Mumford (@Cadair) for starting (PR #373 and PR #622) and to Julian-Samuel Gebühr (@moan0s) for finishing up (in PR #1894), matrix-docker-ansible-deploy can now help you set up maubot - a plugin-based Matrix bot system.
See our Setting up maubot documentation to get started.
🔗Dept of Bots 🤖
🔗Auto-reply maubot plugin
Brendan Abolivier says
Because I don't like having to change my display name to tell coworkers when I'm away, I've written a maubot plugin for an auto-responder bot.
It allows me to signal when I'm away, at which point anyone who sends a message in an existing DM will be sent an automated reply so they know that I'm away, when I'll be back, and how to reach out to me in case of emergencies (it does this once per DM until I come back). When I'm back, I just need to tell the bot and it will automatically turn off the auto-responder and give me a summary of the DMs in which I've missed messages while I was away.
The source code and package for this plugin are available right here: https://github.com/babolivier/maubot-autoreply 🙂
🔗MSC Bot
minecraftchest1 says
I just created a simple bot that generates a MSC url from the specified MSC id. The source code for the project can be found at https://mau.dev/minecraftchest1/mscbot/. And example instance can be found at @maubottest1:synapse1.arsrobotics.org Demo and use the bot in #msc-bot:synapse1.arsrobotics.org
Cat reminds us
This feature is already in the MSC bot used in #matrix-spec or atleast in one of those bots.
🔗Matrix Release Tracker (website)
A release tracker that posts updates into Matrix rooms
Ananace announces
My release tracking bot received a bunch more work since the last update. It now supports tracking repos, groups, and user stars on GitHub, GitLab (both .com and self-hosted), as well as Gitea (though Gitea requires a token for reading stars). And also tracking "releases" - a.k.a. tags - on bare Git repos, at least as long as they don't require SSH key authorization. Things are getting ever closer to a 1.0 release, with only really some missing bang commands and error reporting being the remaining pieces.
🔗Dept of Events and Talks 🗣️
🔗HOPE conference
cel reports
HOPE conference (today/tomorrow/Sunday) is using Matrix https://hope.net/
🔗End of Matrix Summit 2022 CfP
ChristianP announces
The Matrix Summit 2022 is a community event taking place Thu, 25th to Sun, 28th Aug at c-base in Berlin. Today's the last day to propose presentations and workshop. The exact deadline is 22:22 (Europe/Berlin).
Will you be in Berlin and have a Matrix project to talk about? Can you organise a workshop about how to use Matrix? How does your community or workplace use Matrix? Submit your proposal now!
🔗Matrix-DevRoom at FrOSCon
ChristianP reports
FrOSCon is a conference that takes place in Siegburg/Bonn, Germany on 21st and 22nd August. Most presentations will be German, but there are some in English as well. It's all about free, open source software.
And, best of all, we'll have an entire DevRoom track for a day – full of Matrix. Furthermore, you can come by the Matrix stand for that famous hallway track. ✨ I know I'll be there. 👋
https://programm.froscon.org/2021/events.html#matrix%20track
🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server.
🔗#ping:maunium.net
Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | envs.net | 309 |
| 2 | babel.sh | 392 |
| 3 | keks.club | 473 |
| 4 | rom4nik.pl | 641 |
| 5 | babel1.eu | 750.5 |
| 6 | alemann.dev | 793 |
| 7 | mindlesstux.com | 892 |
| 8 | kittenface.studio | 989 |
| 9 | roeckx.be | 1063 |
| 10 | supersandro.de | 1110 |
🔗#ping-no-synapse:maunium.net
Join #ping-no-synapse:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | babel.sh | 172.5 |
| 2 | dendrite.matrix.org | 275 |
| 3 | joeth.uk | 294 |
| 4 | babel1.eu | 302 |
| 5 | dendrite.babel.sh | 509.5 |
| 6 | rustybever.be | 708 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!