This Week in Matrix 2021-03-19
2021-03-19 — This Week in Matrix — Ben ParsonsLast update: 2021-03-19 19:24
🔗Matrix Live 🎙
🔗Dept of Status of Matrix 🌡️
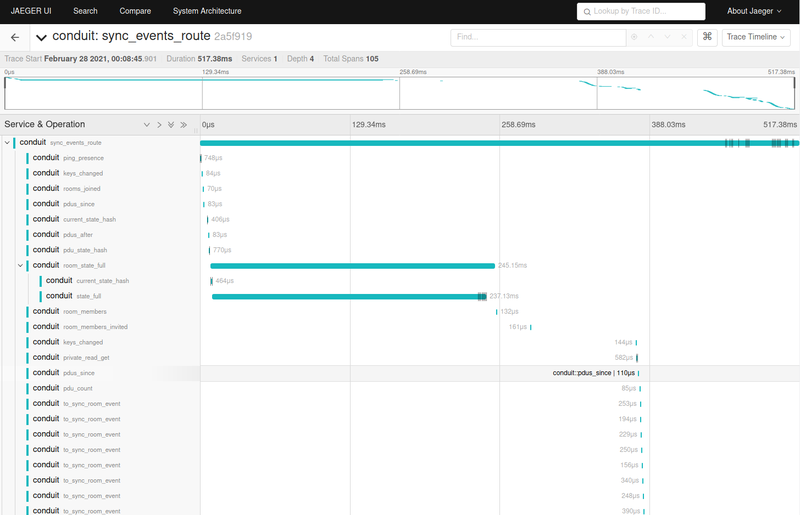
🔗Conduit accepted by Prototype Fund
Conduit is a Matrix homeserver written in Rust https://conduit.rs
timokoesters offered:
Hello everyone! I'm excited to announce that Conduit has been accepted by Prototype Fund and will be funded by the Federal Ministry of Education and Research over the next 6 months: https://prototypefund.de/project/conduit/
The focus lies on federation support and overall improvement and stability, maybe we will even land version 1.0 at the end.
I am surprised how Conduit went from a small hobby project to a very promising Matrix server in just a year. Thank you all for accompanying me on this journey, I really appreciate it.
Now what did we actually do in the last two weeks?
Query signing keys through other servers
Many state resolution updates
Implement /get_missing_events
Implement /state_ids
Many bugfixes
Push notifications on mobile
Fix joining via alias with appservices
Enable zstd for database compression (3.3GB -> 1.6GB on old db!)
Rework state storage to be much more optimized (store a few bytes instead of long strings)
Send proper HOST headers in federation requests (thanks Gabriel!)
Conduit is beginning to run fairly well on the state resolution branch, we will probably merge it after fixing the last few bugs.
This is really excellent news! Congratulations to Timo on this achievement!
🔗Linux Plumbers Conference Matrix / BBB RFQ
David Mehren reported:
The Linux Foundation wants to use BigBlueButton and Matrix for the Linux Plumbers Conference in 2021 and is looking for developers to implement various improvements to BBB and to integrate Matrix as the in-meeting chat.
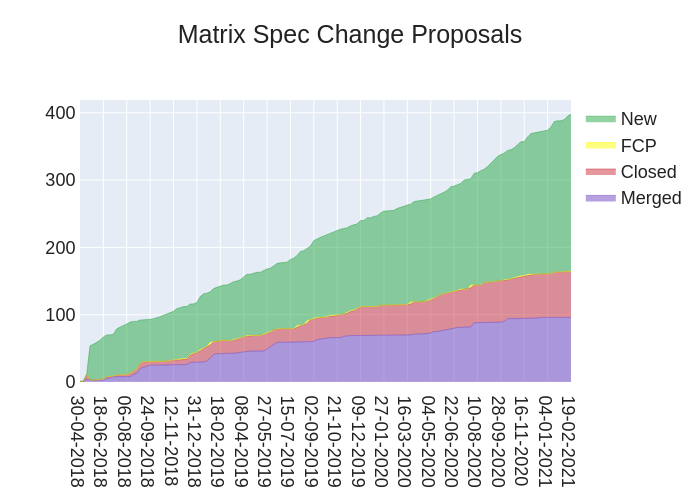
🔗Dept of Spec 📜
🔗Spec
anoa announced:
Here's your weekly spec update! The heart of Matrix is the specification - and this is modified by Matrix Spec Change (MSC) proposals. Learn more about how the process works at https://matrix.org/docs/spec/proposals.
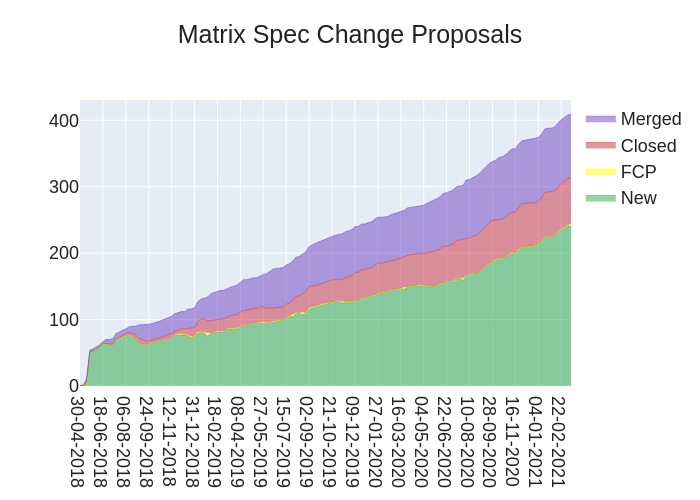
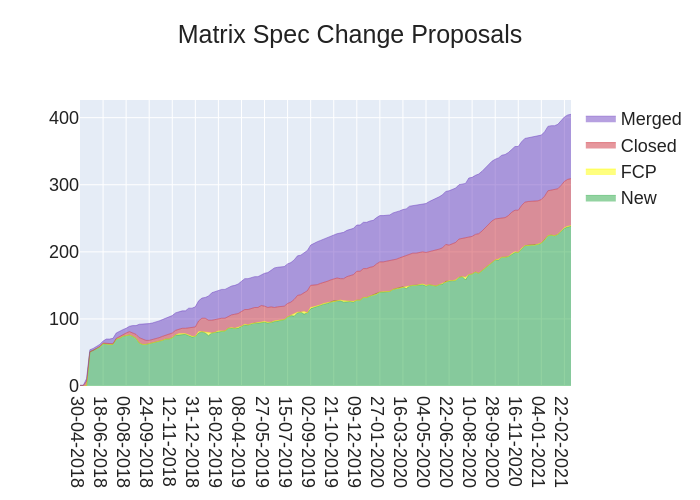
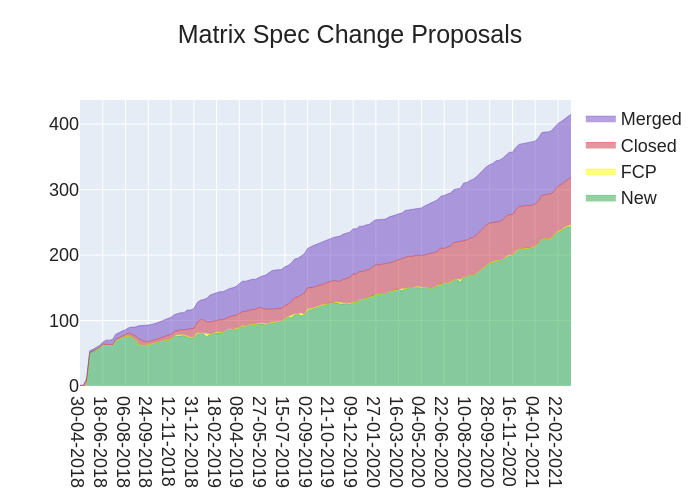
🔗MSC Status
Closed MSCs:
Merged MSCs:
MSCs in Final Comment Period:
New MSCs:
🔗Spec Core Team
We're still working to unfreeze the spec, but in the meantime have been working on MSC2516 (voice messages) and MSC1772 (spaces) plus the merged and in FCP MSCs you see above. ⬆️
🔗Dept of Servers 🏢
🔗matrix-media-repo
matrix-media-repo is a highly customizable multi-domain media repository for Matrix
TravisR reported:
v1.2.5 is out now with several bug fixes and other improvements. The most notable things being:
Optional support for Sentry (error reporting). This is the same error reporting structure that Synapse uses, so it should fit right in 🙂
Several oEmbed URL previews have been fixed, making them useful again. Rejoice once again with a preview of Tweets, Giphys, and other rich content.
Fixed a bug where after uploading media to a datastore the media repo would then download it again before returning it. This made remote media downloads inefficient (it'd download from the remote server, upload to S3, then download from S3, then return it to the user), sorry.
Sometimes a wobbly database could cause some issues with future requests. While I recommend a not-wobbly database, the media repo should be more resilient to this sort of problem now.
As always, if you have bugs or encounter problems with setup then please pop by #media-repo:t2bot.io
🔗Synapse
callahad told us:
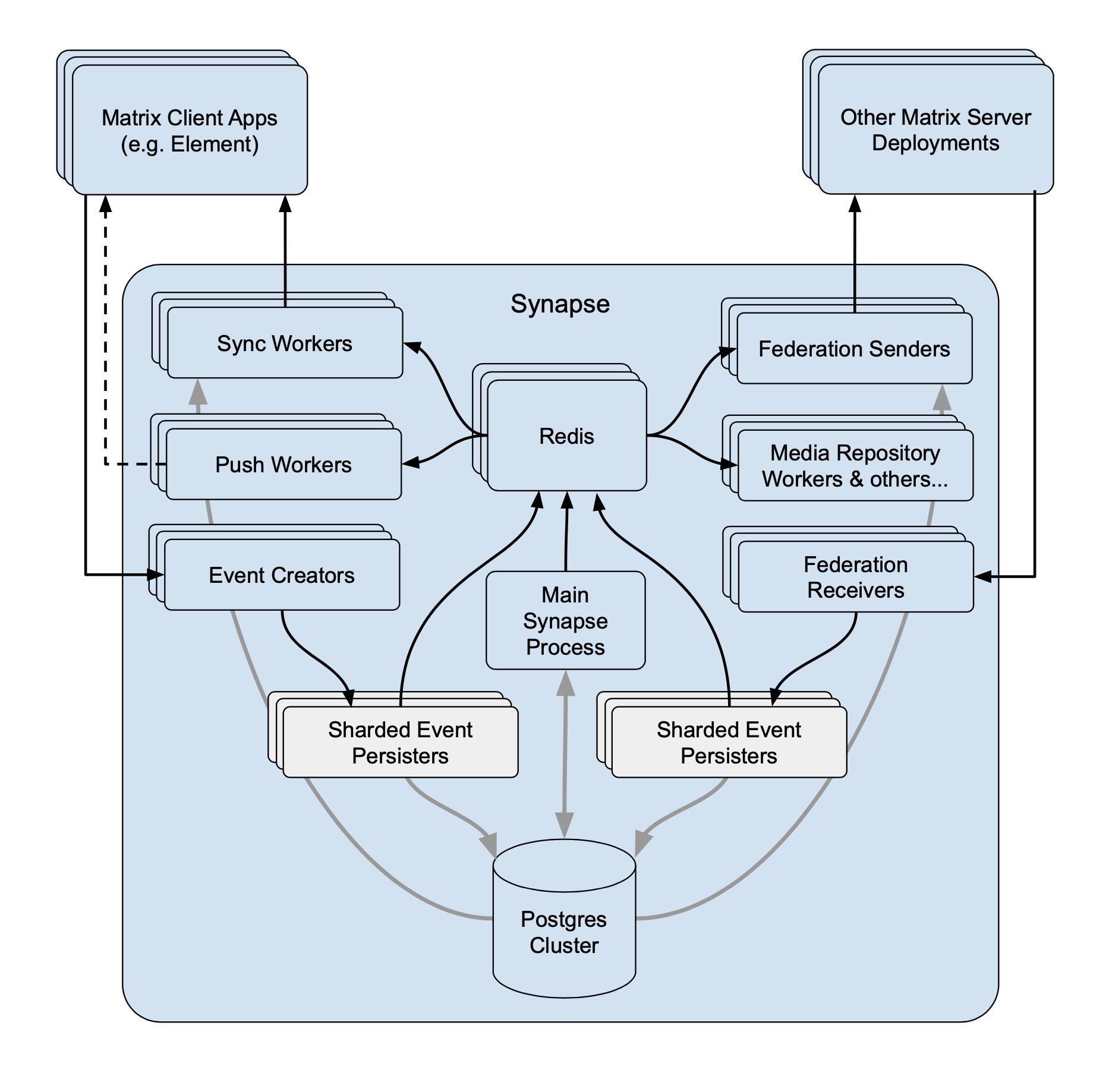
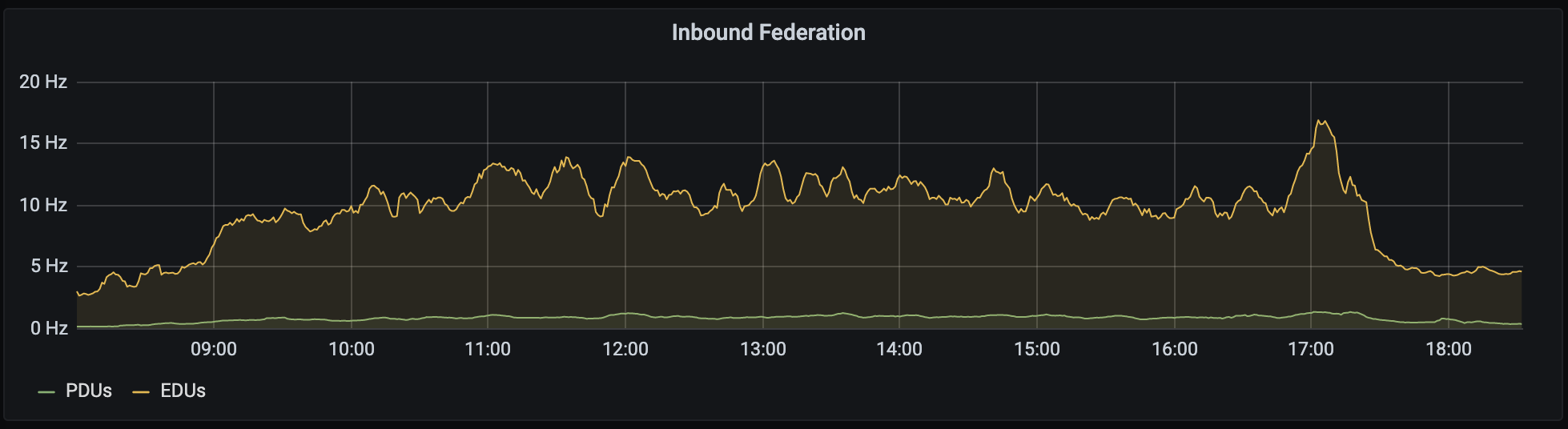
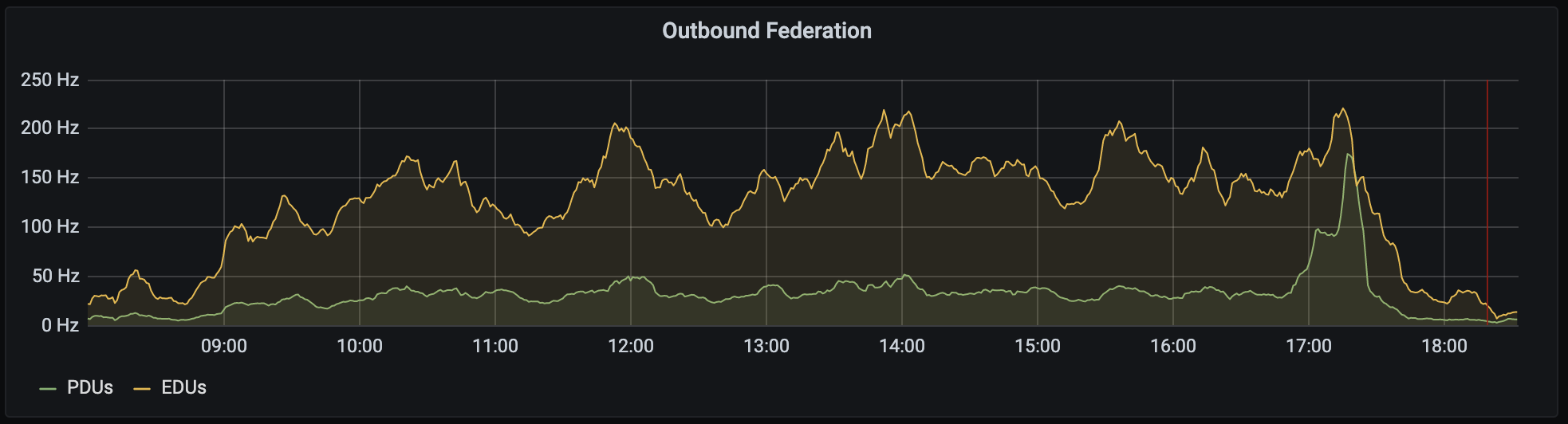
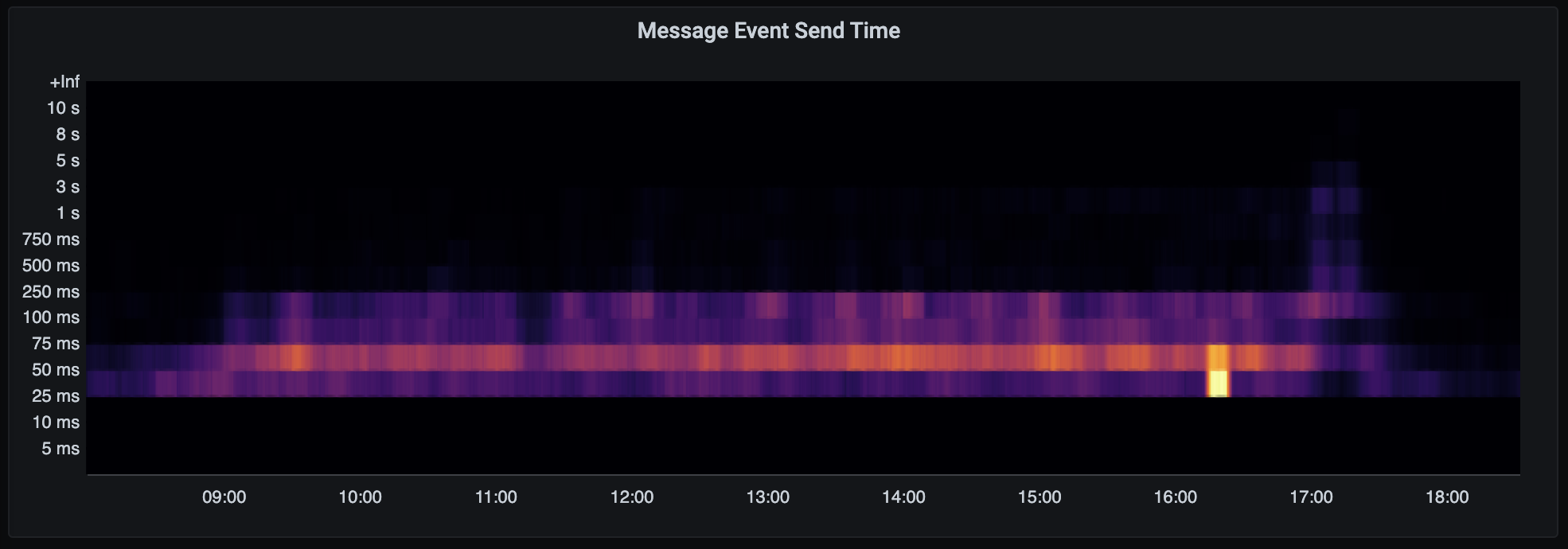
As I mentioned last week, we've been focusing on nailing down some inefficiencies in federation performance. Well, Synapse 1.30.0rc1 is out, and I'm very excited to share one result of that work:
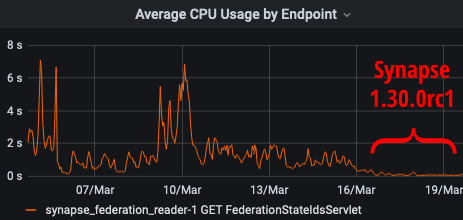
If you look closely, you'll note an order of magnitude improvement in our handling of the
/_matrix/federation/v1/state_ids/{roomId}endpoint. On matrix.org, we've seen that endpoint go from averaging a few seconds of CPU time to well under 100ms. Database usage is similarly reduced.This improvement by @clokep builds on the chain cover index that @erikjohnston implemented in Synapse 1.26.0 to speed up the calculation of auth chain differences during state resolution.
Synapse 1.30 will be released early next week.
We also shipped Sygnal 0.9.0 today, which has a few minor bug fixes as well an initial prototype of Web Push support, per the Hydrogen update in last week's TWiM.
🔗Dept of Bridges 🌉
🔗matrix-puppeteer-line
Fair offered:
matrix-puppeteer-line: A bridge for LINE messenger based on running LINE's Chrome extension in Puppeteer.
Updates:
New name! (Previously named matrix-appservice-line)
New home: https://src.miscworks.net/fair/matrix-puppeteer-line
Group chat support
Syncing of own messages sent from another client (must enable
bridge.invite_own_puppet_to_pm)TODOs:
User/chat avatars
Emoji/sticker support (barring copyright issues??)
LINE->Matrix read receipts
Not requiring the Puppeteer-controlled browser to be visible in order to run (Puppeteer requires it when loading extensions, but will look for a workaround)
Double-puppeting with login support
Bugfixes, inevitably 🙂
Discussion: #matrix-puppeteer-line:miscworks.net
🔗Dept of Clients 📱
🔗Nio, Mio, wow-io!
Nio is a client written with SwiftUI
helge5 announced:
I ported the native https://nio.chat iPhone client to macOS Big Sur, and call that "Mio". Nio and Mio share the same SwiftUI code base, with the Mio changes being merged into the Nio upstream repository. Like Nio, Mio is still in very early stages but looks quite nice already.
A preliminary build can be downloaded over here: https://zeezide.de/download/Mio.app-0.2.0-2.zip, and I posted a screenshot in the Nio channel: https://matrix-client.matrix.org/_matrix/media/r0/download/matrix.org/RpPiQFJytjXboshcUnqnGwrd.
Some time ago we featured Nio running on an M1 Mac via Catalyst, this is being compiled natively for Mac.
🔗Nheko
Nheko is a desktop client using Qt, Boost.Asio and C++17. It supports E2EE and intends to be full featured and nice to look at
Nico (@deepbluev7:neko.dev) offered:
Thanks to LorenDB, notifications now omit the reply fallback and show that that message is a reply instead. They also should not break on encrypted rooms anymore (they show that the message was encrypted for now, but they will be decrypted in the future, if that is enabled in the settings). Emotes should now also show up in them properly and if someone sends an unencrypted image, this should show up with a preview in the notification as well.
Jedi18 ported the room switcher, which can be accessed with Ctrl+K to Qml, which fixes a lot of readability issues and should improve how the rooms get filtered.
Jedi18 also fixed a few issues with playing video on Windows. Salahmak made sending media easier by allowing you to send the image by just pressing enter.
Nheko now also stores images outside of the database, which should decrease database size in the future and make it easier to clean out that part of the cache. We also now use native menus where possible and fixed a few crypto and sync issues as well as formatting of mentions sent by Nheko. Nheko should now not randomely fail to /sync anymore, if your network connection dropped out in between. Also the flatpak should now be able to use your webcam in more cases, but this means we also use less sandboxing now. If you don't like that, you can disable access to all devices, but that sadly also includes the webcam.
🔗Quaternion
kitsune reported:
Yet another beta-approximation of Quaternion at version 0.0.95 arrived, with the main change being fonts finally unified throughout the application. Translators are still very much welcome (French is almost there to be marked as "sufficiently complete", e.g.). Expect 0.0.95 release in the nearest weeks.
🔗Hydrogen
A minimal Matrix chat client, focused on performance, offline functionality, and broad browser support. https://github.com/vector-im/hydrogen-web/
Bruno told us:
Released 0.1.39 with:
- Fix for always retrying decryption after fetching key backups
And work on progress:
Work is progressing on push notifications, along with the Sygnal webpush implementation. An initial version should land early next week.
A community member stepped forward and volunteered on adding SSO support 🎉
Another community member fixed the room header disappearing on iOS when showing the keyboard, this should land soon 🎉
Fixed updates sometimes taking seconds or even minutes to apply
🔗Element Clients
Updates from the teams:
Delight
- Social Login
- MSC 2858 (multiple sso providers) has been pushed to spec
- Spaces
- Web is trailblazing private spaces, while Android is catching up on support for public spaces
- We’ve almost finished the first implementation of the Space Summary API in Synapse, so will start testing public space user flows next week!
VoIP
- Another connectivity fix on web
- Fixed jitsi sometimes getting usernames instead of display names on web
Web
Element Web 1.7.23 is now available, including:
- Refreshed UI for file uploads and sent messages
- Improved VoIP call connection reliability
- Added Edge to the set of supported browsers
- Added send message button to the composer
...along with many smaller fixes.
iOS
- The 1.2.6 release in on the App Store since Monday
- Trust shields have been removed from rooms list for performance
- The crypto module has received several performance improvements
- Several memory leaks have been fixed
🔗Dept of SDKs and Frameworks 🧰
🔗Polyjuice Client 🧙
uhoreg said:
Polyjuice Client 0.4.0 has been released. This release features support for more endpoints, mostly contributed by two new contributors, multi prise and Arjan Sherpenisse. This release also has some backward-incompatible changes. See the changelog for more information.
🔗libQuotient
kitsune told us:
Aligned with the Quaternion beta, stability-focused libQuotient 0.6.6 has been released - packagers already using libQuotient 0.6.x branch are strongly encouraged to update to this version.
🔗Dept of Ops 🛠
🔗matrix-docker-ansible-deploy
This Ansible playbook is meant to easily let you run your own Matrix homeserver.
Slavi offered:
Thanks to Zir0h, matrix-docker-ansible-deploy can now install and configure the Go-NEB bot.
See our Setting up Go-NEB documentation to get started.
🔗Final Thoughts 💭
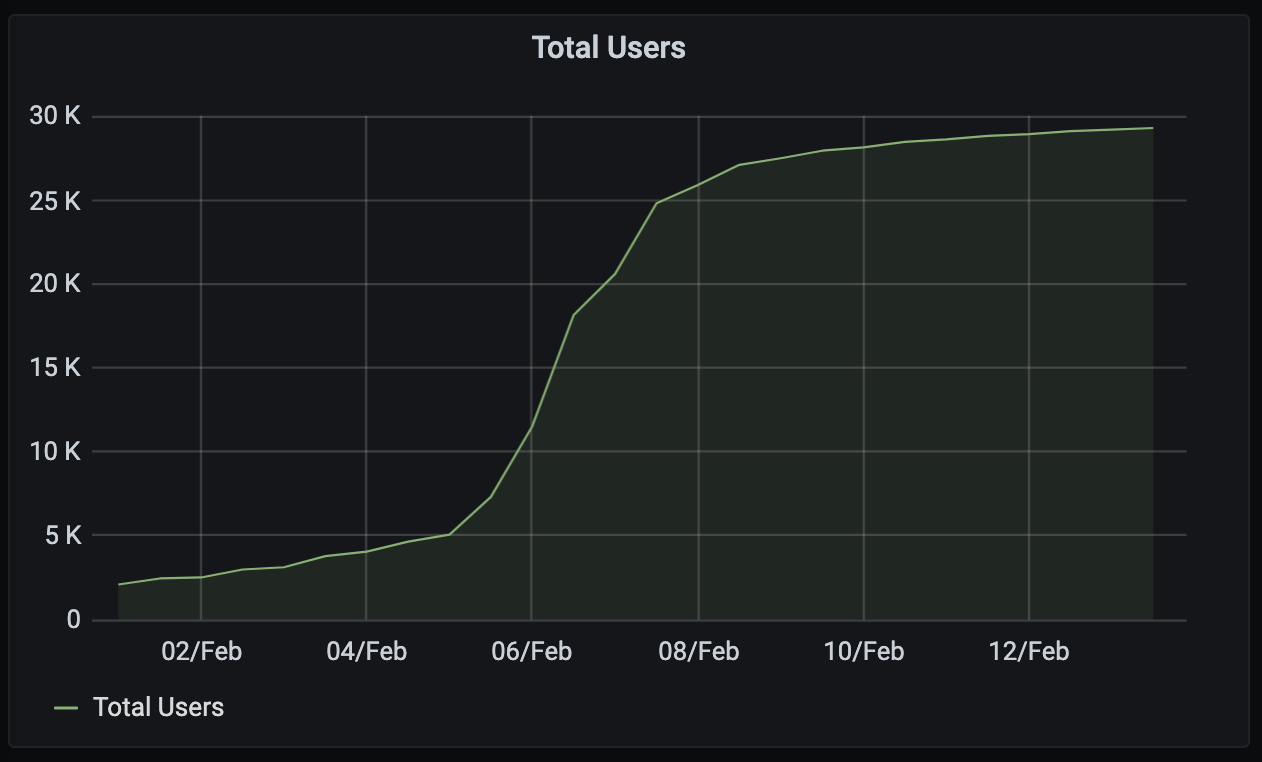
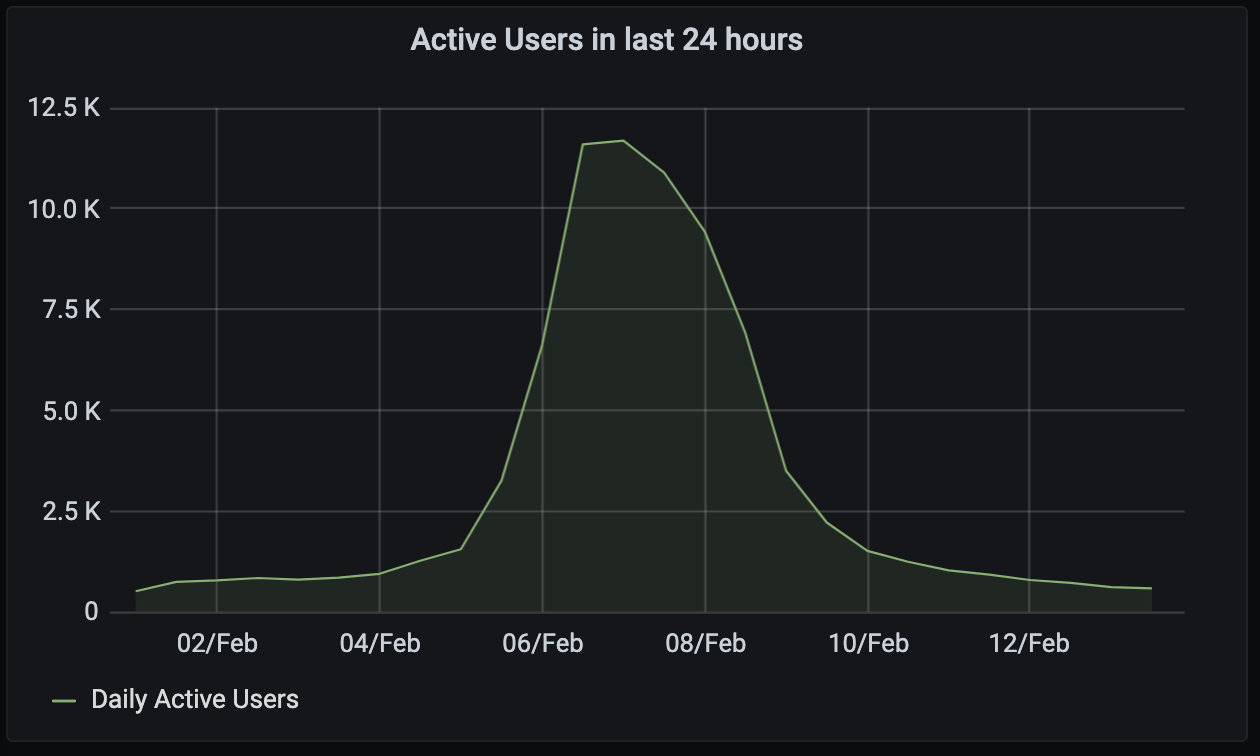
Did you get involved with FOSDEM this year? If you hung out on Matrix that weekend and had a great time, then maybe you bought a t-shirt? Oleg did, and he shared this photo!

🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server.
🔗#ping:maunium.net
Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | envs.net | 356 |
| 2 | maunium.net | 386 |
| 3 | neko.dev | 469.5 |
| 4 | matrix.sp-codes.de | 654 |
| 5 | maescool.be | 666.5 |
| 6 | thomcat.rocks | 669 |
| 7 | fosil.eu | 674 |
| 8 | helsinki-systems.de | 702 |
| 9 | halogen.city | 727 |
| 10 | backhaus.nrw | 898 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!