This Week in Matrix 2020-06-05
2020-06-05 — This Week in Matrix — Ben Parsons🔗Firstly... 🏃♀️
Make an entry in your calendar, don't just write it on your hand: Open Tech Will Save Us is back for a third edition!
Next Wednesday, 10th June 2020!
🔗Matrix Live 🎙
🔗Dept of Spec 📜
anoa reported:
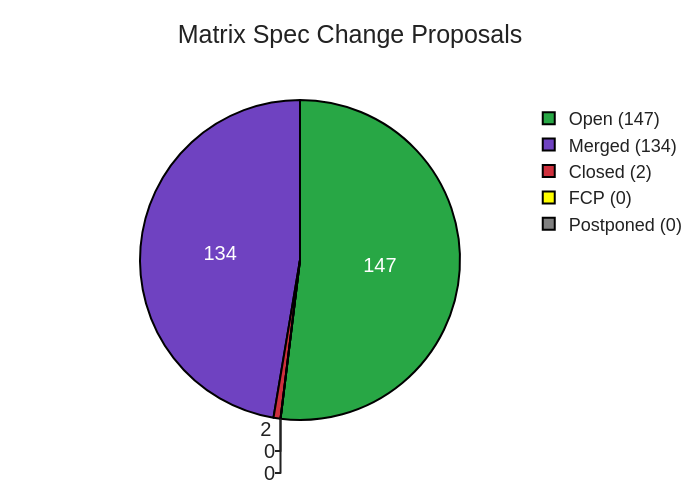
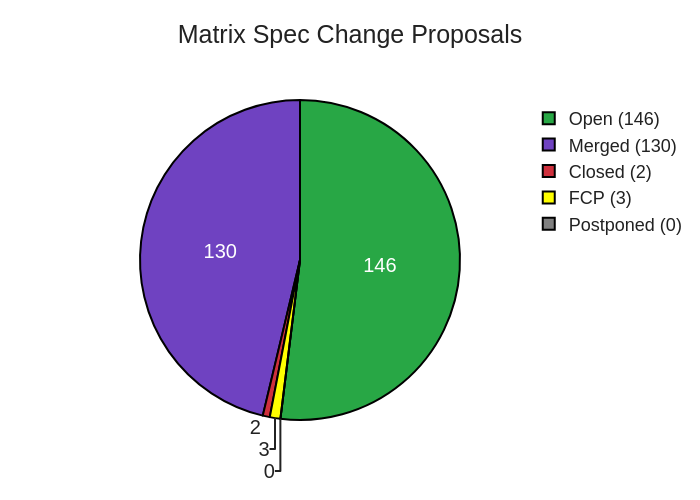
Here's your weekly spec update! The heart of Matrix is the specification - and this is modified by Matrix Spec Change (MSC) proposals. Learn more about how the process works at https://matrix.org/docs/spec/proposals.
🔗MSC Status
Merged MSCs:
MSCs in Final Comment Period:
New MSCs:
MSC2611: Remove m.login.token User-Interactive Authentication type from the specification
MSC2610: Remove m.login.oauth2 User-Interactive Authentication type from the specification
MSC2604: Accept device information for the login fallback endpoint
🔗Spec Core Team
In terms of Spec Core Team MSC focus for this week, we've still got MSC2366 (verification flows) on our plate, but we're removing MSC2399 (UISI messaging) as it just needs one more final tick. We're adding MSC2403 (knocking) in its place.
🔗Dept of Servers 🏢
🔗Mascarene
Nico said:
Mascarene is a quite new homeserver implementation project started a few months ago. Now it's time to introduce it.
Mascarene is written in Scala, runs on JVM and relies on Akka actor model. Out of the box it provides features like efficient streaming I/O, clustering and live data distribution. Data are backed in a PostgreSQL database.
The project is in early stage but already provides a few endpoints which make Mascarene able to talk to Riot.
You can test it at https://snapshot.mascarene.org. You should be able to register, login, create a room and talk to yourself.
Current work is focused on client API implementation; federation or e2ee will come later.
Contributions are welcome, join us on #mascarene:beerfactory.org
🔗Conduit
Conduit is a Matrix homeserver written in Rust https://conduit.rs
timo told us:
Welcome back! This week I went through the whole Client-Server API and wrote down everything that is still missing from Conduit. You can find issues for all of them in the milestone for Conduit 1.0. This should make it more easy for contributors to find something to work on and gives a lot more structure to the repo (maybe I also did it, because it's so satisfying to close issues and see the milestone percentage go up 😛).
Some of the issues I could already close this week include:
Implement redaction
Implement loading the message someone replied to (/context)
Fix bugs with notifications
Don't send typing events when nothing happened
Bundle typing events into one EDU
Don't send notification counts every /sync
Implement heroes
As you can tell, a lot of work is starting to go into smaller improvements, which is a good thing, because it means most of the core work is already done!
Thanks to my supporters on Liberapay (Take a look, I improved it 🙂).
🔗Synapse
Neil told us:
This week in Synapse land we have been focusing on bug fixes especially SSO and soft logout.
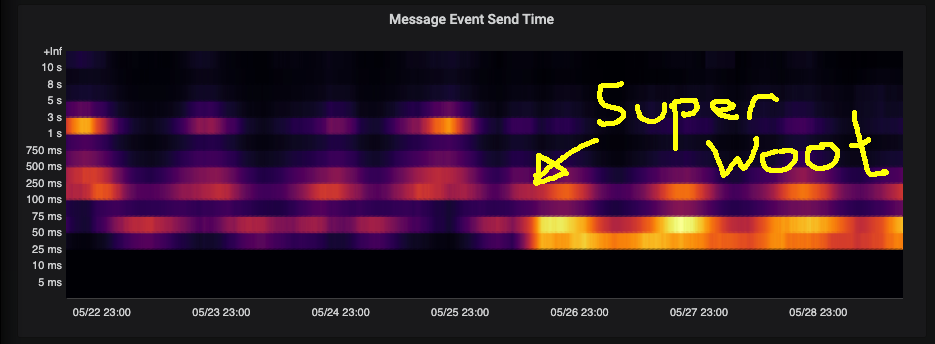
We also spent some time thinking about how to further improve performance for large scale deployments (like matrix.org). In short this will mean sharding contested workers such as the media repo worker, the federation sender and the federation reader. We also want to remove some more functionality from the master process because it is still sitting at about 80% and we’d like some more head room. We'd also like to fix up the state compressor so it can easily be run as a background progress to save on disk space, this will benefit all installations big and small. Finally we want to speed up joins over federation. Exciting times.
Next week, more of the same and we should start on some of the perf items. Also look out for changes to notification defaults.
🔗Dendrite / gomatrixserverlib
Dendrite is a next-generation homeserver written in Go
Neil Alexander offered:
Updates:
Room version 6 support has been added
Server signing keys which have passed their validity period are now re-requested and updated properly, increasing reliability of federation substantially
Federated room joins have been significantly sped up by requesting missing auth events inline when verifying room state, rather than repeating the entire verification for each missing event
Local send-to-device support has been added (federated send-to-device coming soon)
A lot of code clean-up has taken place (with more to come), including cleaning up the internal APIs and the component bases
Decoding of room version 3 event IDs in request URLs has been improved
Inbound federation requests now interrupt backoff intervals on outbound sends
A new internal API exists now for interrupting backoff intervals on the federation sender
The federated
/devicesendpoint now returns in the correct formatPublic rooms are now sorted by their member count
Only our own aliases are stored in the public rooms directory now
gomatrixserverlib is now responsible for marking room versions as supported/stable
Spec-compliant transactions are now sent to the appservice component
File URIs for SQLite databases are now set up using common functions
Handling registration for a user that already exists has been fixed (thanks S7evinK!)
Dendrite can now be configured to use a HTTP proxy server for outbound HTTP (thanks dr-bonez!)
Sytest compliance:
Client-server APIs: 36%
Server-server APIs: 35%
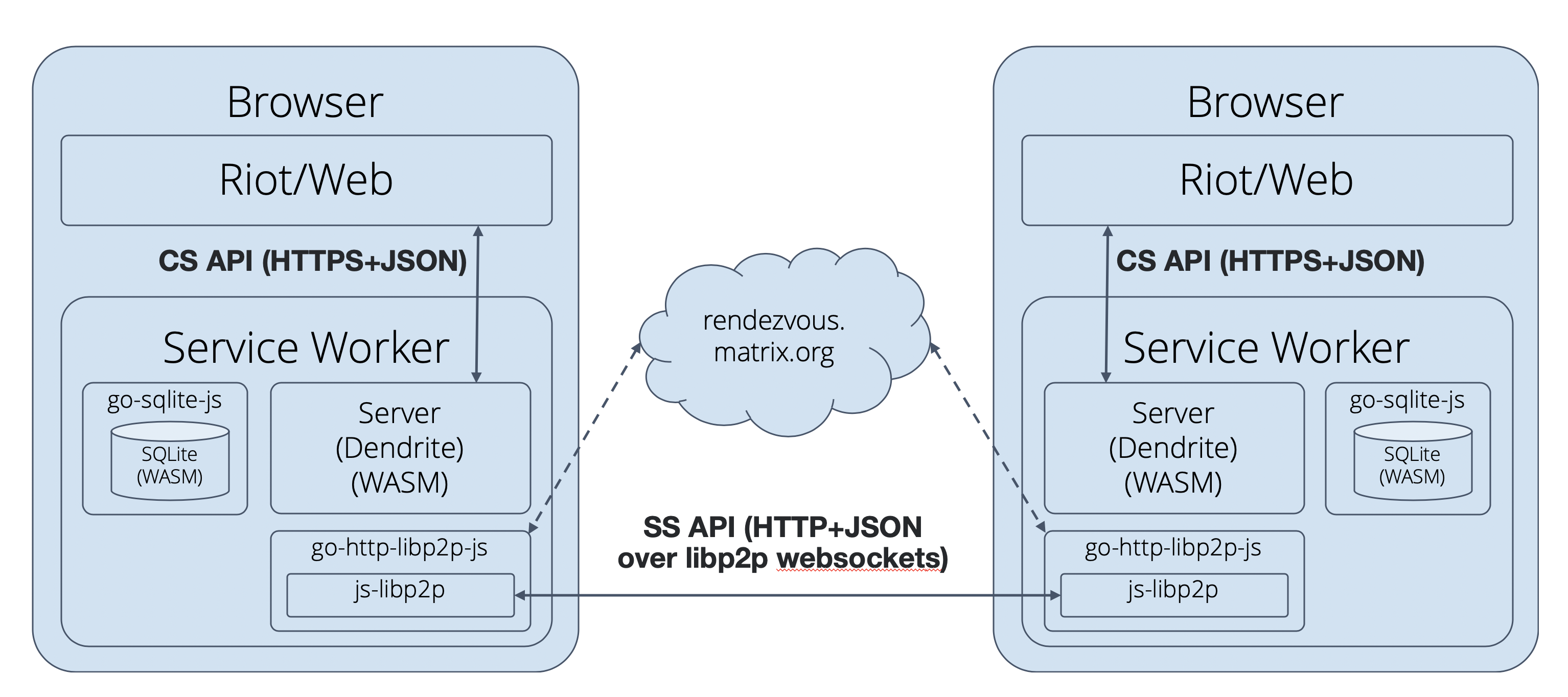
In other news, Kegan wrote a post on how p2p.riot.im works, including Dendrite's journey to SQLite and WebAssembly!
Additionally! You may have already read about v0.1.1 of the P2P Matrix demo - this is a big update, with local storage, room alias handling, federation improvements and more!
🔗Dept of Bridges 🌉
🔗Matrix Appservice Minecraft bridge now in beta
Dylan reported:
My Matrix Appservice Minecraft bridge is now in beta
Here is our Matrix room #minecraft:dhdf.dev

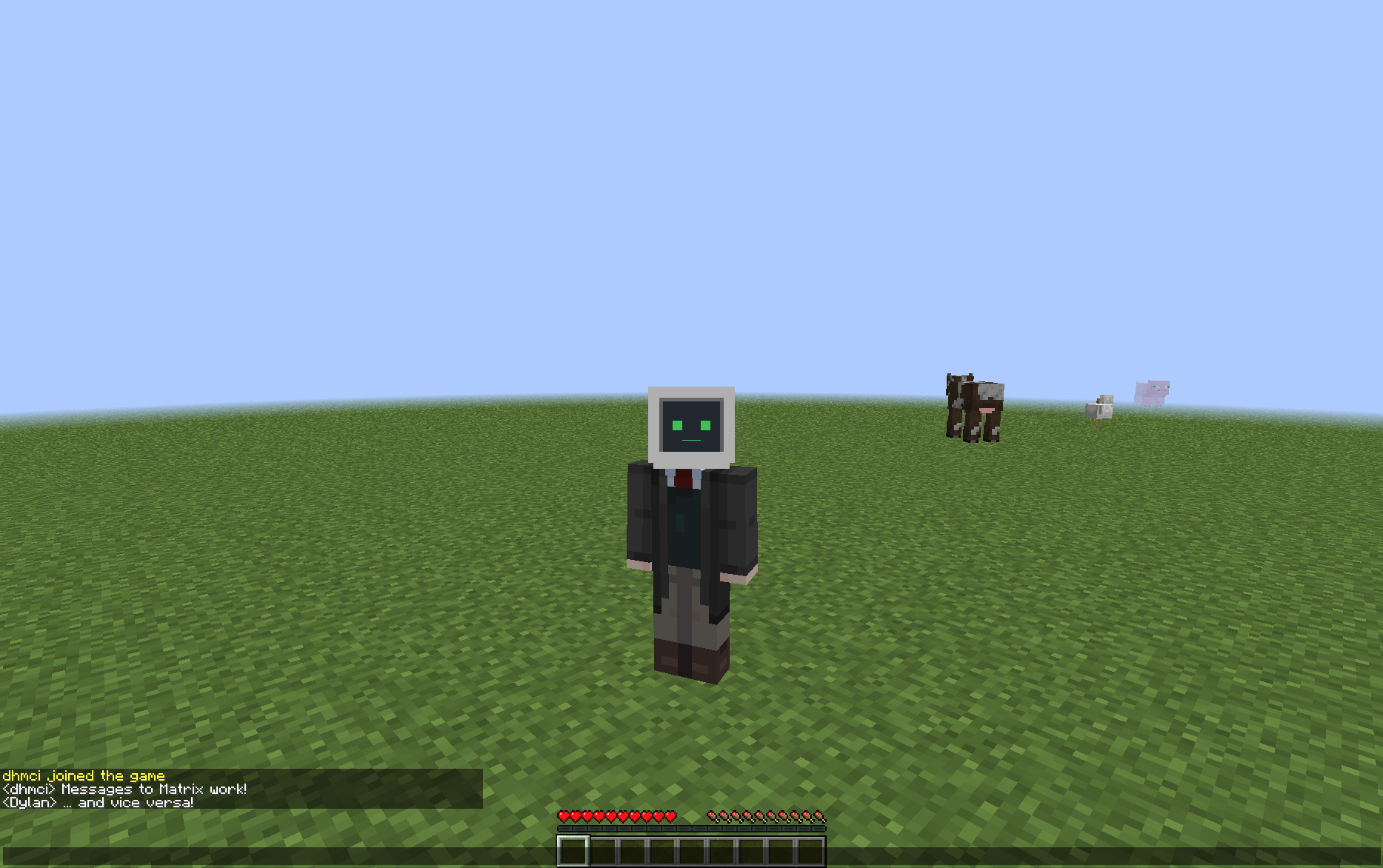
More screenshots: https://github.com/dhghf/matrix-appservice-minecraft#screenshots
🔗Tuple
Alexander Eisele reported:
Tuple is a very early simple matrix <--> mqtt bridge for IOT and other embedded devices.
It's my very first golang project, but it works(TM).
Discussion/Testing: #tuple:eiselecloud.de
This is exciting! I would love to see more IoT-related projects!
🔗mautrix-hangouts
Tulir reported:
mautrix-hangouts can also do backfilling now, both when creating portal and missed messages when connecting
🔗mautrix-facebook
Tulir told us:
mautrix-facebook got support for backfilling history when creating portals and backfilling missed messages when connecting. There's also an option to periodically reconnect to potentially fix the bug where Facebook decides that you don't get messages anymore, but doesn't actually disconnect you.
🔗mautrix-whatsapp
Tulir said:
I had apparently forgotten to implement bridge information in the whatsapp bridge when I implemented it in my other bridges, but that mistake is now corrected. I also fixed a bug with encryption where it would generate too many one-time keys and cause messages to be undecryptable. Finally, mautrix-whatsapp had its first release this week since it's working reasonably well now.
🔗Dept of Clients 📱
🔗Radical Native
stoic reported:
Eager to test the keytar feature (pickle key stored in OS secret storage) with Riot Web? Support landed in radical-native v0.1beta13, which uses Rust keytar bindings under the hood. Testing requires the latest and greatest of Riot Web, so riot.im/develop might be the place to see it in action
Keytar support is a very very new feature, uhoreg, who has been working on it in the shadows and wasn't expecting to see it land yet, commented:
😲
🔗Pattle: version 0.17.0
Pattle is a client written for Flutter using Dart
Wilko offered:
A new version has been made available and will become available on Google Play and TestFlight!
⚠️ If you're not logged out, it's recommend that you logout and additionally clear your data after installing the new version! ⚠️
🔗Changes
Added the ability to reply to messages!
You can now accept (and reject) invites!
You can now join and search channels!
Chat input has been redesigned!
Chat details has been somewhat redesigned
The group icon in the chat's details is now blurred and can be shown unblurred by scrolling to the top
Replies are now a maximum of 3 lines long
The current version is now shown in settings
Wait a bit after typing before checking the homeserver when logging in
Chat name change events are now shown
Chat icon change events are now shown
Errors are now reported to Sentry again!
You won't enter the app with empty chats if the initial load failed
Show date above chat creation event
Fix time sometimes being dark and not readable on image messages
Fix sender's name going outside of bubble
Sender is now in bold for chat description change event
More messages are now loaded if initially not enough are displayed
Show ripple effect on chat app bar when tapping
And more!
🔗Get Pattle
Android
🔗Get involved
Follow development: #app:pattle.im
Issues or suggestions: Post them here!
Donate: If you want to support Pattle, you can donate!
🔗RiotX v0.21.0
benoit announced:
RiotX v0.21.0 has been released on May 28th. It adds support to identity server configuration and e-mail/phone binding and unbinding. It's also now possible to switch between languages inside the app and to display the list of attachments (media and file) of a room. A new setting has been also added to hide redacted (deleted) events in the timeline. As Riot-Android SAS v2 is also included in this release. Also
formatted_bodyform.noticeandm.emoteare now taken into account.This week we were still working on implementing VoIP (audio and video call). Support for integration manager, widgets and sending stickers has been merged to develop. Many new features are coming soon, stay tuned!
🔗Riot-Android classic
benoit offered:
Riot-Android: Version 0.9.12 has been released on May 20th. I forgot to mention it the TWIM of last week. It contains a fix for favorite rooms vanishing and also the SAS v2 implementation (new key agreement method).
🔗Mirage
miruka said:
Mirage 0.5.1 has been released today:
Persistent, cross-client, push rules-aware unread message counters
Read receipts are now sent to mark rooms as read
Basic room settings can now be edited and saved
More control over window alerts, e.g. only enabling them for messages mentioning you
Lots of bugfixes
🔗Riot-iOS
Manu said:
This week, we finalised our work around the iOS13 SDK. The coming public TestFlight (0.12.2) is the result of this work. It comes with a lot of changes including a full rewrite of the push handling codebase, trying to find solutions to make matrix e2ee compatible with iOS Notification Service Extension. Most of these changes are unfortunately invisible for end users. Please report any issues. Note this is safe to switch between this TF and 0.11.5.
In parallel, we started to implement the cross-signing bootstrap and the recovery management. The UX of this is going to be refined on Riot-Web and RiotX-Android. Riot-iOS will implement the refined UX directly.
🔗Riot Web
A glossy Matrix collaboration client for the web. https://riot.im
Ryan told us:
We had several Riot Web releases this week, first with 1.6.3:
Security fix for auth handling in SSO deployments, thanks Quentin Gliech for responsible disclosure
Added more shortcuts to jump to read marker and upload a file
Fixed notification tray icon stability for desktop on Windows
Added an IRC style layout (currently available in labs only)
Added font scaling settings (currently available in labs only)
Fixed several bugs in the cross-signing bootstrap process
Converted older banner-style UI for updates etc. to newer toasts
This was quickly followed by 1.6.4 to fix a few regressions with dismissing toasts, compact timeline layout, key backup, and tooltips on scroll.
🔗Dept of SDKs and Frameworks 🧰
🔗Matrix Dart SDK: version 0.32.0
Wilko announced:
- Databases are now deleted as a migration strategy
This will be in effect until 1.0 (or a bit before). If needed, make a backup between every minor version bump.
All members necessary to render the timeline are now loaded from the store
Room.myMembershiphas been removed, useRoom.me.membershipAdd
Rooms.enterandRoom.jointo join roomsAdd
Room.leavemethodAdd
PublicRoomsAdd useful getters to
MemberlikeisInvitedorhasJoinedRemove
AliasesChangeEventErrors in the separate isolate are now added to the
updatesstream where possible, or thrown in the calling isolateFix profile API not working on servers where authorization is required
Add
MyUser.hasSyncedFix
countnot being nullable inMemberTimeline.loadMore fixes and small changes!
Get it on pub!
🔗Ruma
Ruma is a Rust project to create a comprehensive set of APIs for Matrix. Previously there was a Ruma homeserver project.
jplatte offered:
This week,
Devin, our GSoC student, started blogging on ruma.io
We released ruma-identifiers 0.16.2 and ruma-federation-api 0.0.2
We started updating ruma-events and ruma-client-api with the changes from version r0.6.1 of the client-server specification
We started moving all of our libraries into one monorepo!
As part of this, we introduced a kind of meta-library so you no longer have to keep the versions of the individual libraries in sync manually
We're hoping that this makes experiments across multiple libraries and the overall contribution process easier 🙂
🔗Dept of Interesting Projects 🛰
🔗Safe Support Chat
Brendan said:
Safe Support Chat, previously known as OCRCC Chatbox, now has a website with guides on how to set it up for organisations: https://www.safesupport.chat/
For context, Safe Support Chat is an embeddable chatbox built on Matrix with cool features such as end-to-end encryption support to enable individuals to seek support with organisations that provide it. It was initially built for the OCRCC (Ontario Coalition of Rape Crisis Centres) in order to allow survivors of sexual violence to communicate and seek help safely with OCRCC facilitators.
Kim Allen of Primal Glow Communications, one of the parties involved in Safe Support Chat's development, also recorded a podcast with Nomadic Labs about this project: https://podcast.nomadiclabs.ca/episodes/the-adventure-of-building-an-open-source-chatbox
🔗Dept of Ops 🛠
🔗matrix-docker-ansible-deploy
This Ansible playbook is meant to easily let you run your own Matrix homeserver.
Slavi reported:
Thanks to benkuly's efforts, matrix-docker-ansible-deploy now supports bridging to SMS (with one telephone number only) via matrix-sms-bridge.
To learn more, see our Setting up Matrix SMS bridging docs page.
🔗CLI Federation Tester
Kai reported:
A new version of the terminal-based federation tester has been released. The current version 1.11 should now cover the entire server discovery process including scenarios with a .well-known configuration without a port, but with a DNS SRV entry.
The script relies on bash, curl, jq and openssl. It has been tested on linux but should also work on *bsd and macos.
The script can be downloaded here:
#cli_federation-tester_de:matrix.chat-secure.de
(The message about the latest version will always be pinned)
🔗FLAP
Louis Chmn announced:
Hi, I've build FLAP to help other self-host multiple free software. FLAP can currently help you to easily setup Synapse, Riot, Nextcloud, SOGo and Jitsi all with SSO and low maintenance needs. Feel free to give it a try !
Sources are here: https://gitlab.com/flap-box/flap
If you need help setting things up, Matrix room is here: #flap-software:matrix.org
For French companies, I am also offering managed paid hosting: https://www.flap.cloud
🔗Dept of Bots 🤖
🔗sparky's Matrix Bot
sparky told us:
Announcing Matrix Bot (name is a work in progress)
The first "official" release of matrix bot has been made and you can find the latest release source at https://github.com/sparky8251/matrix-bot/tree/v1.0.0
It's flagship features are currently
an imperial <--> metric unit converter for common conversational units
a configurable search and link for issues/pulls that responds to any message containing something in the format of
jf#123orjf #1234a configurable general purpose URL linker that responds to messages containing things such as
docs@hwaorlink @troubleshooting(both sides of the @ are configurable)There are plans to enable group pings, get a help command that can be limited to function only in a specific room, and more in the works so be sure to check back soon!
🔗matrix-reminder-bot
anoa reported:
matrix-reminder-bot bot to remind you about things. Supports reminding an individual in a room or the whole room itself. Also supports setting alarms, which will continue to sound periodically until silenced.
Built with nio-template and the excellent matrix-nio library.
🔗Dept of Ping 🏓
Here we reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server. Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | fairydust.space | 354 |
| 2 | aragon.sh | 419 |
| 3 | envs.net | 426 |
| 4 | maunium.net | 456.5 |
| 5 | maclemon.at | 559 |
| 6 | matrix.vgorcum.com | 667.5 |
| 7 | threatmodel.io | 695 |
| 8 | gottliebtfreitag.de | 734 |
| 9 | neko.dev | 818 |
| 10 | nzbr.de | 892 |
🔗Final Thoughts 💭
There are bounties to be had! AU$500 to support Emoji Reactions in Fractal, for reference this is tracked on the GNOME gitlab.
We didn't hear from Spectral too recently, but there are signs of code being written.
This week I've been chatting with conference organisers making really interesting virtual event plans, and I'm bursting to share some of the Matrix integration plans, hopefully more details coming soon.
elmussol said:
For those who Hubzilla or Zap or ActivityPub or Friendica or Diaspora, there is now a Hubzilla forum for all things Matrix: https://elsmussols.net/channel/matrix
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!