Synapse 1.11.0 released
2020-02-24 — General — Matthew HodgsonHi all,
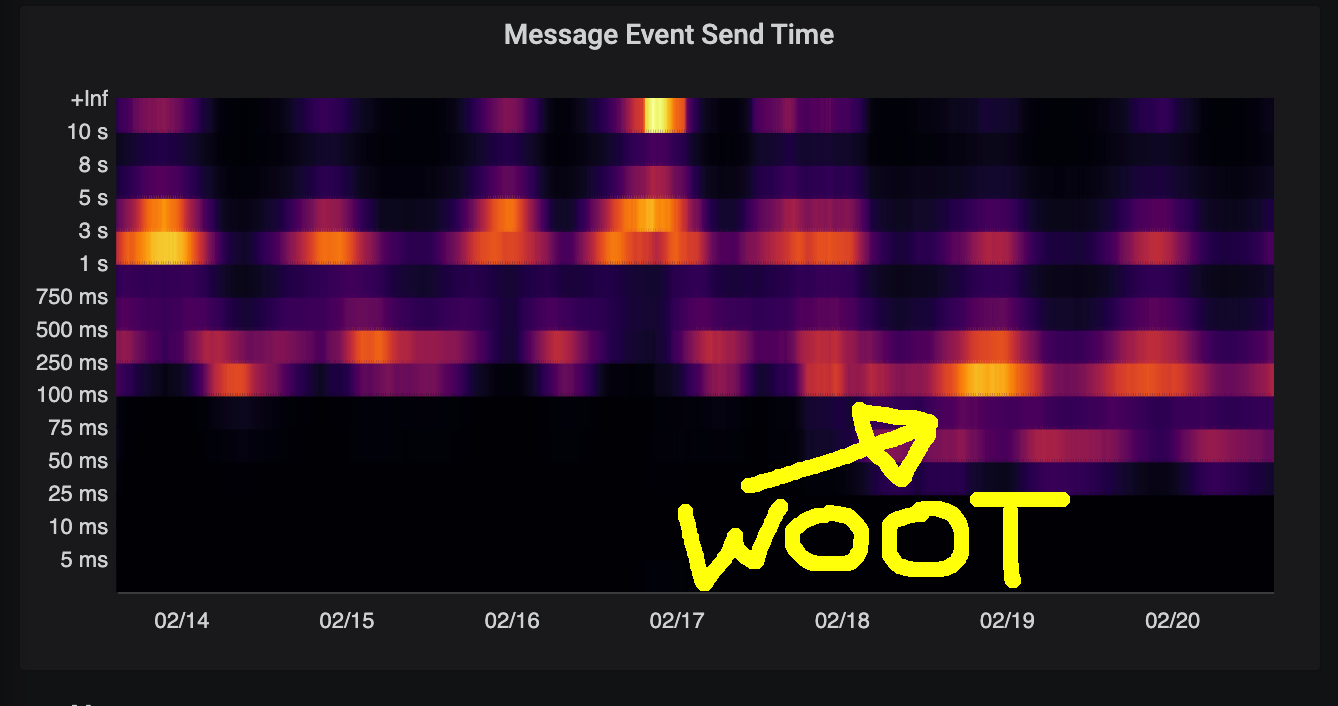
Synapse 1.11 landed on Friday (sorry for running late on blogging the release notes!)
The main change is to introduce an experimental API MSC2432 for managing aliases for rooms on your local server. In Synapse 1.10 we removed support for m.room.aliases events, which were a way to try to track which aliases a room had on the room itself (but were vulnerable to abuse). In this release we've re-added the ability to query which aliases a given server has for the room, giving visibility for managing aliases, without having them spray all over the room state itself. Riot/Web 1.5.10 supports the new API, giving a way to manage aliases on your local server while we finish off the remaining work to improve alias safety & maintenance.
We've also changed the default power levels for new rooms so that room upgrades and ACLs require you to be an Admin (PL100), and invites in public rooms now require you to be a moderator (PL50).
Get the new release from github or any of the sources mentioned at https://github.com/matrix-org/synapse/blob/master/INSTALL.md.
🔗Synapse 1.11.0 (2020-02-21)
🔗Improved Documentation
- Small grammatical fixes to the ACME v1 deprecation notice. (#6944)
🔗Synapse 1.11.0rc1 (2020-02-19)
🔗Features
- Admin API to add or modify threepids of user accounts. (#6769)
- Limit the number of events that can be requested by the backfill federation API to 100. (#6864)
- Add ability to run some group APIs on workers. (#6866)
- Reject device display names over 100 characters in length to prevent abuse. (#6882)
- Add ability to route federation user device queries to workers. (#6873)
- The result of a user directory search can now be filtered via the spam checker. (#6888)
- Implement new
GET /_matrix/client/unstable/org.matrix.msc2432/rooms/{roomId}/aliasesendpoint as per MSC2432. (#6939, #6948, #6949) - Stop sending
m.room.aliasesevents when adding / removing aliases. Checkalt_aliasesin the latestm.room.canonical_aliasevent when deleting an alias. (#6904) - Change the default power levels of invites, tombstones and server ACLs for new rooms. (#6834)
🔗Bugfixes
- Fixed third party event rules function
on_create_room's return value being ignored. (#6781) - Allow URL-encoded User IDs on
/_synapse/admin/v2/users/<user_id>[/admin]endpoints. Thanks to @NHAS for reporting. (#6825) - Fix Synapse refusing to start if
federation_certificate_verification_whitelistoption is blank. (#6849) - Fix errors from logging in the purge jobs related to the message retention policies support. (#6945)
- Return a 404 instead of 200 for querying information of a non-existent user through the admin API. (#6901)
🔗Updates to the Docker image
- The deprecated "generate-config-on-the-fly" mode is no longer supported. (#6918)
🔗Improved Documentation
- Add details of PR merge strategy to contributing docs. (#6846)
- Spell out that the last event sent to a room won't be deleted by a purge. (#6891)
- Update Synapse's documentation to warn about the deprecation of ACME v1. (#6905, #6907, #6909)
- Add documentation for the spam checker. (#6906)
- Fix worker docs to point
/publicised_groupsAPI correctly. (#6938) - Clean up and update docs on setting up federation. (#6940)
- Add a warning about indentation to generated configuration files. (#6920)
- Databases created using the compose file in contrib/docker will now always have correct encoding and locale settings. Contributed by Fridtjof Mund. (#6921)
- Update pip install directions in readme to avoid error when using zsh. (#6855)
🔗Deprecations and Removals
- Remove
m.lazy_load_membersfromunstable_featuressince lazy loading is in the stable Client-Server API version r0.5.0. (#6877)
🔗Internal Changes
- Add type hints to
SyncHandler. (#6821) - Refactoring work in preparation for changing the event redaction algorithm. (#6823, #6827, #6854, #6856, #6857, #6858)
- Fix stacktraces when using
ObservableDeferredand async/await. (#6836) - Port much of
synapse.handlers.federationto async/await. (#6837, #6840) - Populate
rooms.room_versiondatabase column at startup, rather than in a background update. (#6847) - Reduce amount we log at
INFOlevel. (#6833, #6862) - Remove unused
get_room_stats_statemethod. (#6869) - Add typing to
synapse.federation.senderand port to async/await. (#6871) - Refactor
_EventInternalMetadataobject to improve type safety. (#6872) - Add an additional entry to the SyTest blacklist for worker mode. (#6883)
- Fix the use of sed in the linting scripts when using BSD sed. (#6887)
- Add type hints to the spam checker module. (#6915)
- Convert the directory handler tests to use HomeserverTestCase. (#6919)
- Increase DB/CPU perf of
_is_server_still_joinedcheck. (#6936) - Tiny optimisation for incoming HTTP request dispatch. (#6950)