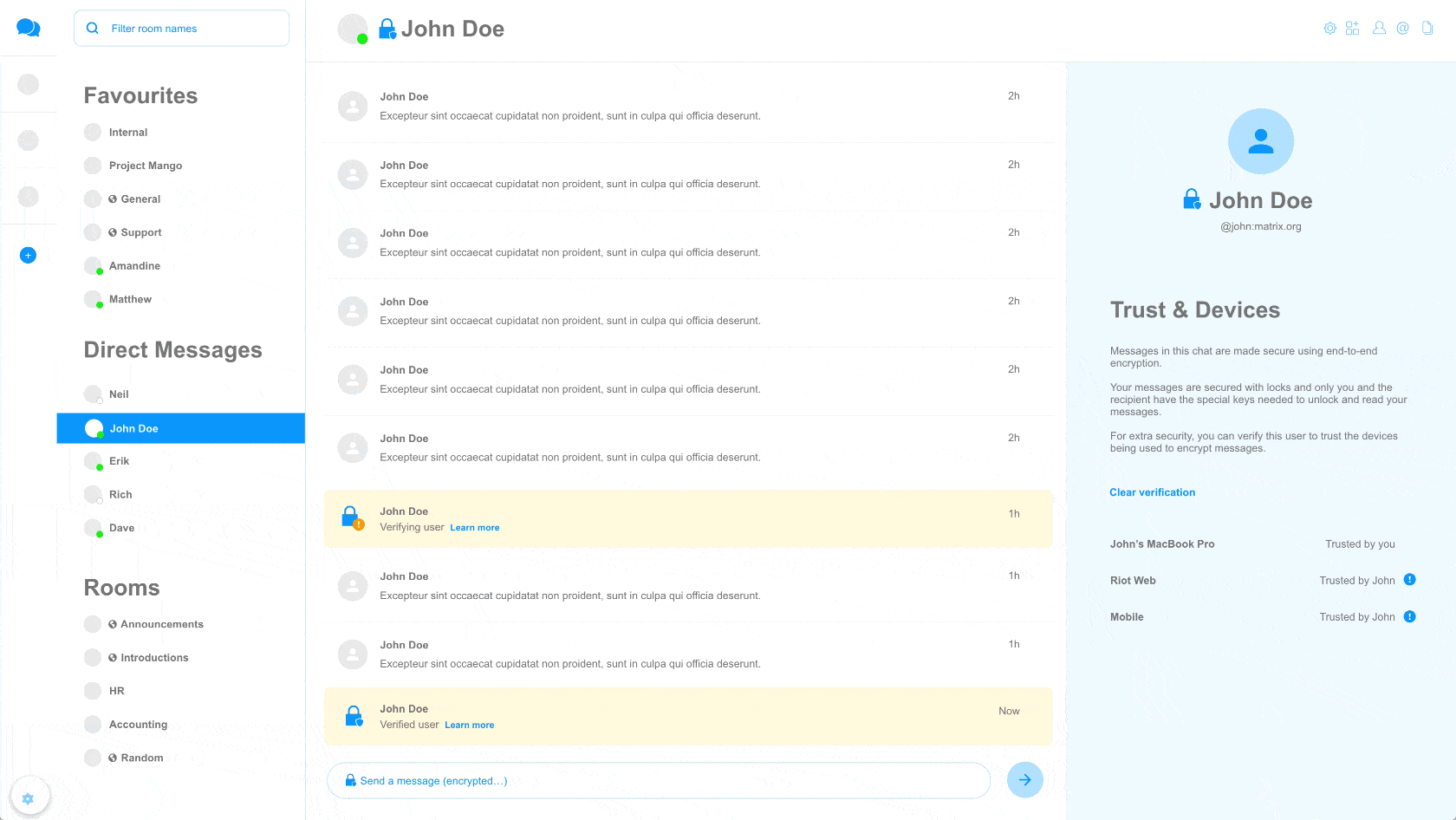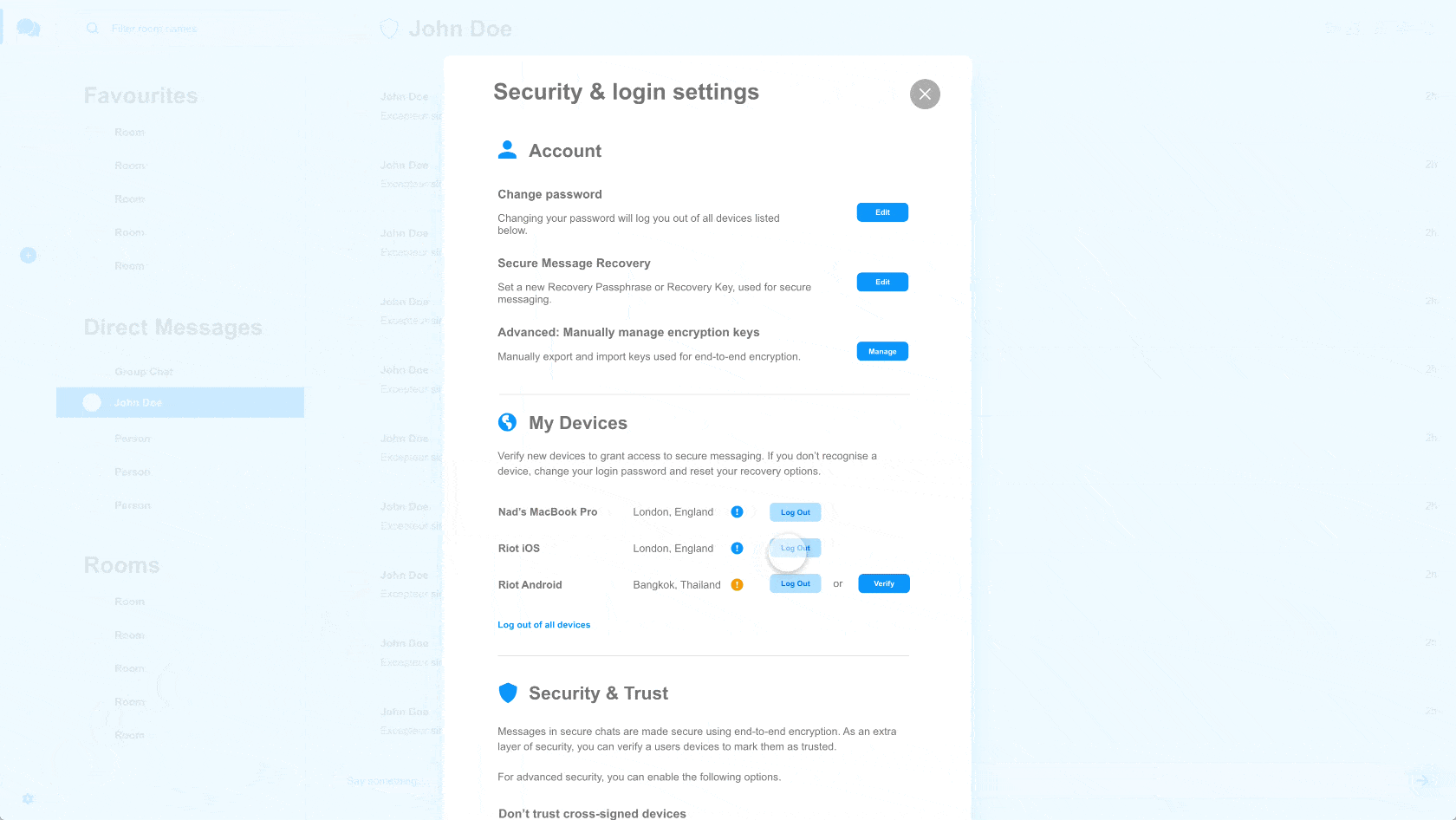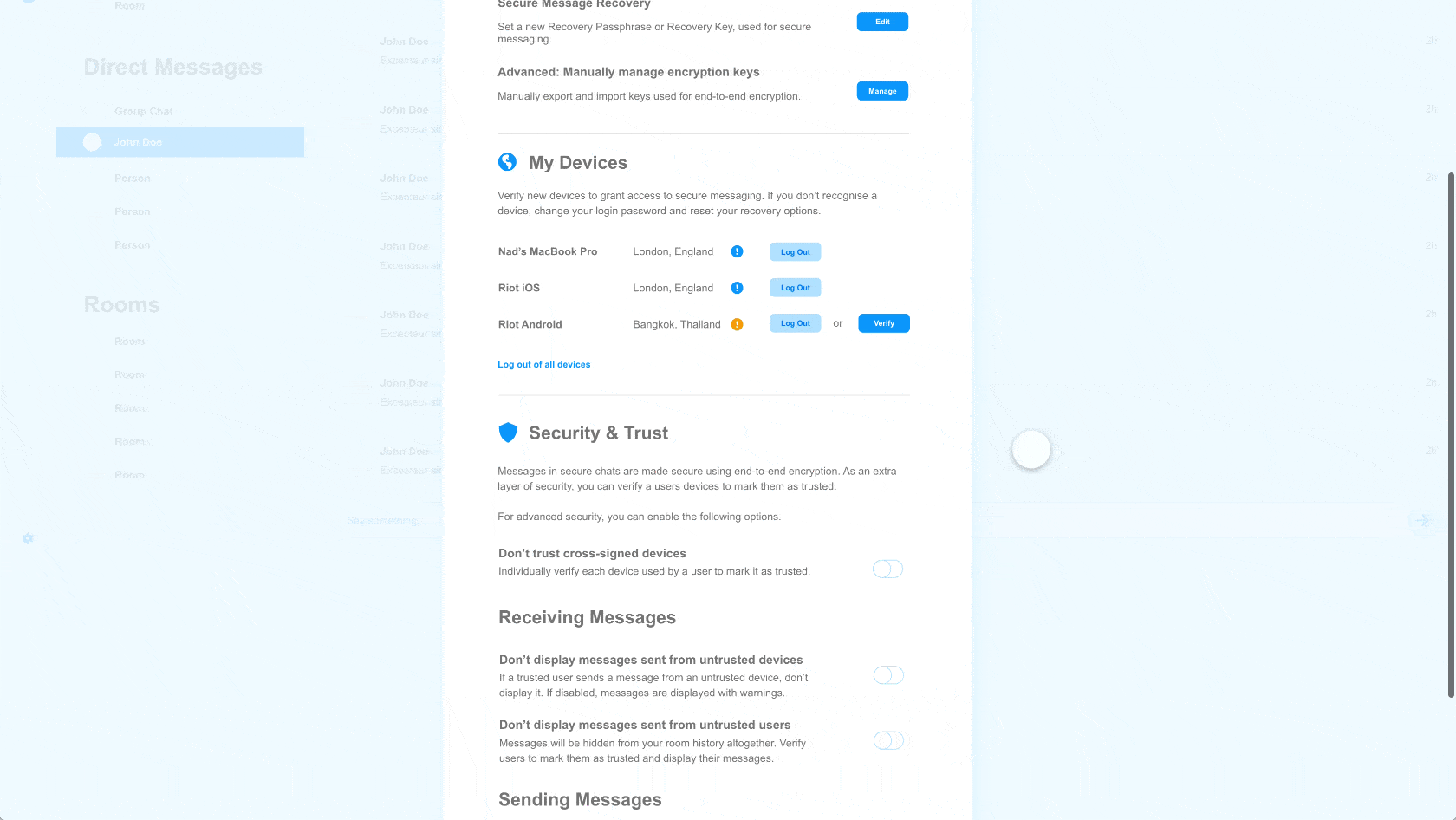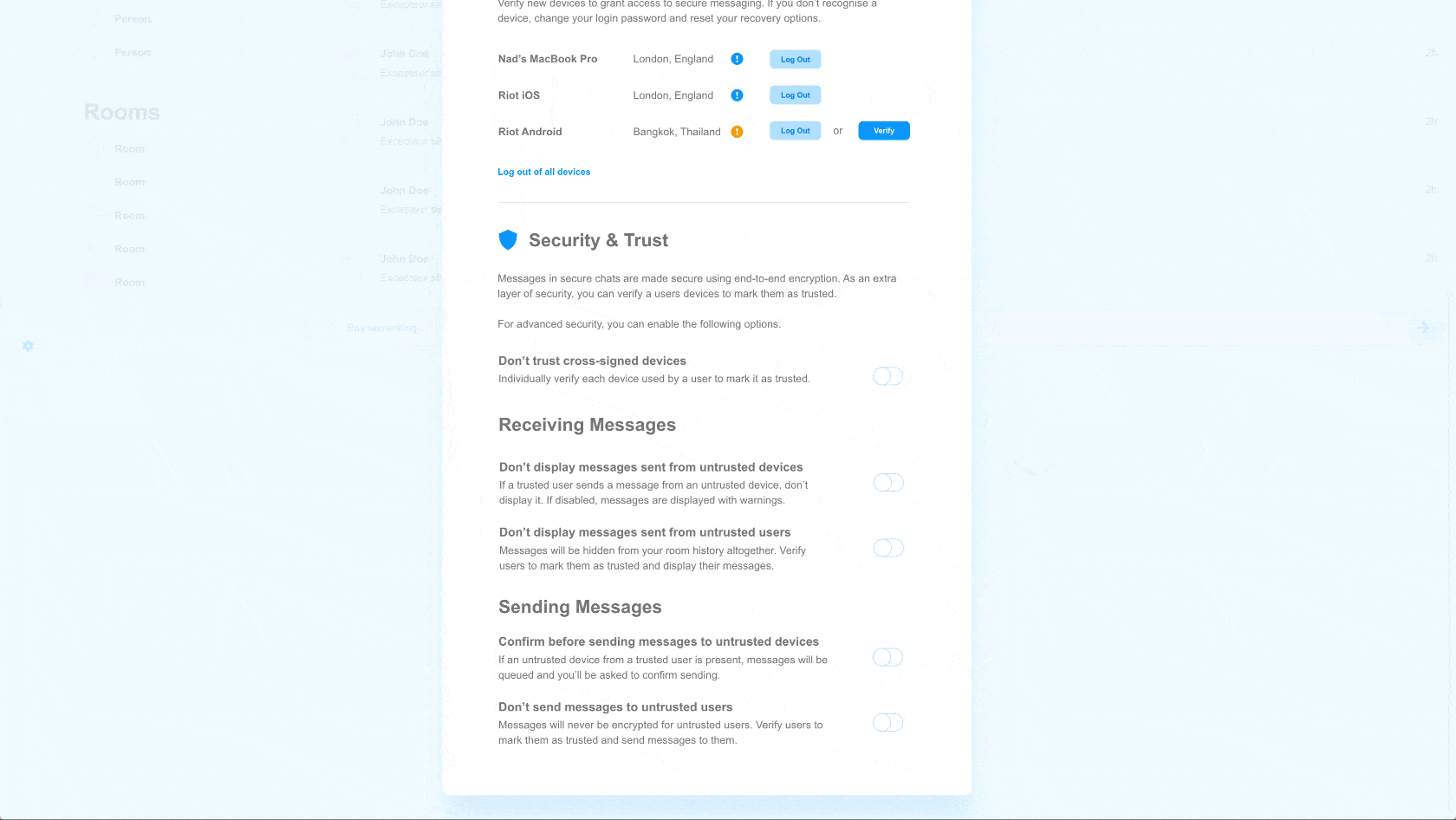
This Week in Matrix 2018-11-16
2018-11-16 — This Week in Matrix — Ben Parsons🔗Matrix Live S3E04
This week we continue Matrix Live Season 3 by talking to community member axx, Axel Simon from La Quadrature du Net, a French advocacy group that promotes digital rights and freedoms of citizens. We talk about the work La Quadrature du Net do, with a focus on the importance of decentralisation and how Matrix helps support this.
🔗mxisd v1.2.0 released
Max has been giving updates on the road to mxisd v1.2.0, which was released this week:
A new stable version of mxisd is out: v1.2.0. It comes with:
- The ultimate identity store that lets you run any command on the system to fetch info, making it the most generic yet. The sky is now your limit!
- The ability to send email notifications about room invites when done using a Matrix ID regardless if their users is already provisioned on synapse, using emails found in an Identity store. Targeted at onboarding/migration to Matrix for any org/corp.
🔗Spec
TWIM: five(!) new MSCs so far this week, including a long-awaited MSC for displaying math(s) in messages: https://github.com/matrix-org/matrix-doc/pull/1722
🔗matrix-appservice-purple
Half-Shot has been working on important work for his final undergrad year. Just kidding! He's been working on bridges as you'd expect:
I've been working on matrix-appservice-purple, and the community immediately rallied around and helped me get it into shape. We've got automated builds for both the bridge and the libpurple binding modules. In features land, group chats are now working at a basic level and I will be working on supporting profiles next.
#purple-bridge:half-shot.uk is now a room where you can tell me why your favorite protocol doesn't work with the bridge. (It's also used for updates.)
🔗Informo
vabd:
A couple of SCS (Specs Changes Submissions) have been merged into the Informo specs, notably SCS #2 which introduces a complete technical description of the network's nodes and their expected behaviour, and SCS #4 which changes the duration of the call for public review period, shrinking it from 14 days to 7 days, in order to speed specs work up while letting a decent amount of time for people to give a look at new SCSs and voice their concerns.
🔗Synapse 0.33.9rc1
Synapse has a new release candidate - 0.33.9rc1 - If you'd like to help us test it, you can get it here.
🔗Koma
This week in Koma, I have been working on a correct implementation of the user registration process. Currently waiting for a small issue with synapse to get fixed
For kotlin programmer who might be interested https://github.com/koma-im/koma/pull/6
🔗f-droid.org has set up a new matrix (synapse) server
f-droid.org has set up a new matrix (synapse) server for internal conversation and to chat in #fdroid:matrix.org , which will obviously also get a :f-droid.org alias.
For now the server is private, only allowing core team members to get an account in order to keep the performance manageable.
🔗mautrix-telegram v0.4.0
tulir released an RC for mautrix-telegram:
mautrix-telegram 0.4.0 release candidate was released. It's mostly a lot of bugfixes.
…and TravisR hosted it on t2bot.io:
as of a few minutes ago, the t2bot.io Telegram bridge is updated to 0.4.0rc2
🔗Push-to-Talk for Jitsi calls in Riot
anoa:
An implementation for Push-to-Talk for Jitsi calls in Riot has now been completed and is in the review phase. This was a result of multiple weeks of work, with code changes across many different repositories. Will hopefully make a difference with background noise or many participants. Look forward to seeing it land in /develop sometime shortly! Works with both Scalar and Dimension setups.
🔗gomuks progress
gomuks development is slowly continuing. It now uses mautrix-go and I also added proper reply rendering.
🔗More Things
Last week we mentioned that Julian Sparber has been working on Fractal UI. He has since published a blog post about the work, and also notes that Purism are beginning to sponsor Fractal development: https://blogs.gnome.org/jsparber/2018/11/10/purism-fractal-sponsorship/
Half-Shot: "The events API update for Slack was released on riot.im/develop a little while ago, which let you do more than webhooks could let you do. The UI scalar/integration manager bits were left on /develop for testing but got rolled out to /app this week."
If you have feedback about the matrix.org website (which you may be on right now!), we have a new room to collect and organise it: #matrix.org-website:matrix.org. Thank you to Aaron Raimist for much-needed chasing (of me) on this work…
This week I attended TADSummit in Lisbon to tell them about the excellent progress Matrix has been making this year. You can see more details of the conference (plus video) here: http://blog.tadsummit.com/2018/11/16/tadsummit-2018-web3/
🔗That's all I got!
If you need more, come back here next week, for all the latest from This Week in Matrix! Also, join us in #twim:matrix.org to tell us what you've been doing.