This Week in Matrix 2018-11-30
2018-11-30 — This Week in Matrix — Ben Parsons🔗Porting to Python 3 - Matrix Live S3E5
Longer than usual episode of Matrix Live this week. Amber talks to Neil about the works she's been doing over the last few months to port Synapse from Python 2 to Python 3. Recommended for anyone who's been following along the progress of Synapse, or who wants a good intro on the benefits of Python 3 over Python 2.
🔗ZeroPhone
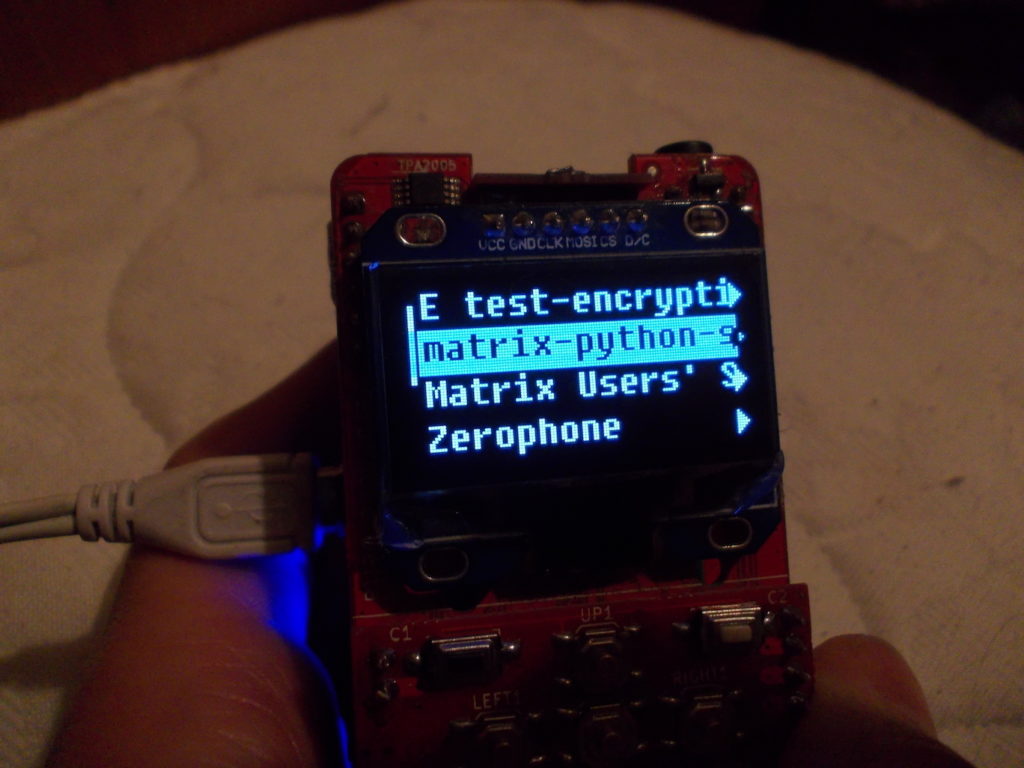
This week we learned about ZeroPhone, a fairly mature project aiming to build a working cellphone on top of a Raspberry Pi Zero.
an open-source smartphone that can be assembled for 50$ in parts. It is Linux-powered, with UI software written in Python. Currently, ZeroPhone is based on Raspberry Pi Zero, SIM800L GSM modem and 1.3" OLED screen and button interface.
&Adam was the first to bring it to our attention:
I stumbled across this blog post which mentions a matrix app in a project to create an open, hackable phone out of a raspberry pi. It's old news at this point I guess, but I don't think I've seen it mentioned here, so I thought it might be a neat thing worth featuring: https://zerophone.github.io/newsletter/ZeroPhone-Weekly-No.-16/
The creator of the Matrix app, derivmug also arrived to tell us about his work:
Hey everyone, I have been suggested to post about the Zerophone project here. I have written a basic matrix client for it. It's basically a simple phone based on a raspberry pi zero, focused on privacy, security and hackability.
The client app is built using the matrix-python-sdk, I'm also hoping to chat to derivmug as part of a future Matrix Live. Take a look at the code here.
Just to prove it's running on real hardware!
🔗Spec / Foundation
- Work continues on MSC1730 - Mechanism for redirecting to an alternative server during login https://github.com/matrix-org/matrix-doc/pull/1730
- Foundation: Working with the Foundation lawyers on the CIC37 to register the Foundation as a Community Interest Company proper
🔗The Federation (the-federation.info)
Jason Robinson is passionate about Federated technology, and has been working on his site at https://the-federation.info/ for some time. He recently added Matrix to the list of protocols he scrapes and lists:
Matrix (or more specifically, Synapse) servers are now visible on the The Federation info website at https://the-federation.info/matrix%7Csynapse. The website collects lists of servers for various federation protocols (like Matrix, ActivityPub, Diaspora, etc). If a server outputs usage information, it also shows some historical information for servers and projects. Currently the information available from Synapse on the site is just version, availability of registrations and (obviously) domain name. If you want to register your server, check https://the-federation.info/info for more details. Tips also welcome on how to register other Matrix server projects and how to get more data out of servers.
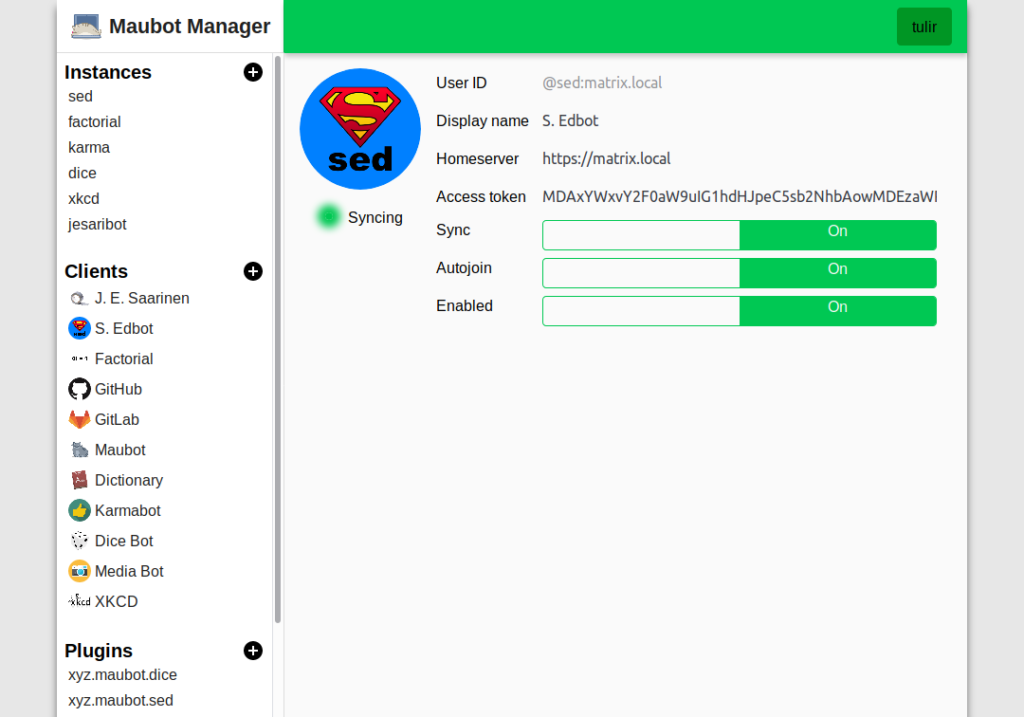
🔗maubot
tulir has continued work on maubot:
- I made a rss plugin for maubot and added a fancy log viewer in the maubot management UI.
- mautrix-telegram 0.4.0 was released, though it has no changes since the release candidate. I also copied mautrix-telegram's HTML parser into mautrix-python. Hopefully it's now generic enough so that when mautrix-telegram switches to mautrix-python, it can drop most of the built-in HTML parser.
🔗matrix-appservice-discord
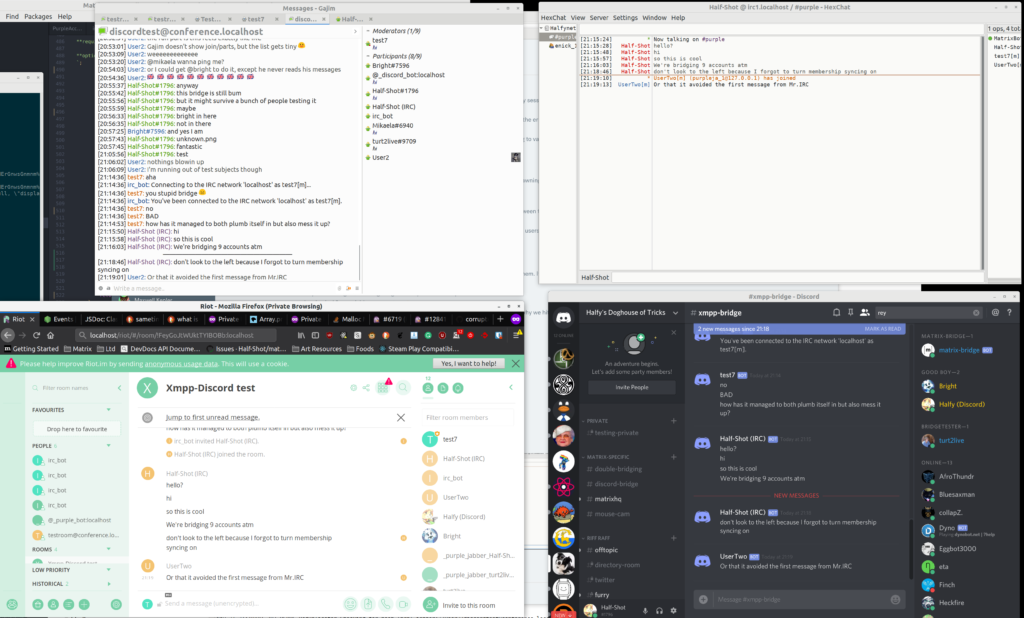
Bridge-of-the-week this week is matrix-appservice-discord. Anyone in the dev room (#discord:half-shot.uk) will be very aware of this as Half-Shot and Sorunome have spent the day testing @room notifications.
matrix-appservice-discord received a lot of work these past days. Not only the usual small bugfixes, but also some rather big changes: The parsers for both Discord->Matrix sending and Matrix->Discord sending were re-written completely to properly handle things (and thus, at the same time, crunch a bunch of edge-case bugs!). In addition, the long-awaited highlighting issues with @ everyone and @ here (on discord) and @ room (on matrix) were addressed. Some of these things are still in PR stage, but expected to be merged soon!
Half-Shot also provided a great screenshot of everything working well:
is just showing off having IRC+Matrix+Discord+XMPP plugged together. XMPP being the one purple is bridging
🔗matrix-docker-ansible-deploy
Slavi reports that:
matrix-docker-ansible-deploy now supports configuring the matrix-synapse-ldap3 LDAP auth password provider. Thanks to @tvo6 for contributing this!
🔗Riot iOS
- User Agreement (GDPR) in now part of the registration flow
- Reskin has started
- New fixes for unexpected “Empty room”
- We have PR templates
🔗Riot Android
- Realm store for e2e keys has landed
- Riot reboot: support timelines merge in DB to avoid to trash data as less as possible when navigating through permalinks
- New settings to choose ringtone for incoming call
- We have PR templates also
🔗SimpleMatrix
MTRNord, is working on the design for SimpleMatrix:
As I currently have less time for actual coding I am planning out the SimpleMatrix Design. You can find the Images of the Design (and a PDF file) at https://gitlab.com/Nordgedanken/simplematrixredesignimages Feel free to also join #SimpleMatrix:matrix.ffslfl.net to give feedback.
🔗Synapse
- This week our focus has been to work through some final bugs blocking 0.34.0 which will be our first official python 3 release. Expect a RC rsn. For a sneak peak see this week's Matrix Live video at the top!
🔗Auf Wiedersehen…
That's it for this week. If you have anything to share with us, and you'd like to be included on the blog, please come talk in #twim:matrix.org!
In one month from now, many Matrix-acolytes, including myself, will be at 35c3. If you'll be there, come chat to us in #matrix-35c3:matrix.org!