This Week in Matrix 2020-01-10
2020-01-10 — This Week in Matrix — Ben Parsons🔗Matrix Live 🎙
🔗Dept of Spec 📜
anoa informed us:
We've had a slight lull from people crawling out from winter holiday hibernation caves, but there's likely more to come as everyone gets back into the swing of things.
Merged MSCs
No MSCs were merged this week.
MSCs in Final Comment Period
No MSCs are currently in FCP.
New MSCs
The Spec Core Team is continuing to work on implementation of existing MSCs.
🔗Dept of Servers 🏢
🔗Synapse 1.8.0 is out now
Get the latest news here!
Synapse 1.8.0 has arrived, it contains a whole host of bug fixes and tweaks, most notably fixing some long standing problems with search.
More generally we are spending a lot of time improving the e2ee experience ahead of switching on e2ee by default, so watch this space.
🔗Deploying Synapse
Several packaging projects have been updated to deploy the new version:
- matrix-docker-ansible-deploy from Slavi
- avhost/docker-matrix and mvgorcum/docker-matrix from Mathijs
- Kubernetes from Ananace
- multi-arch synapse docker image from Black Hat
- also from the Debian repos thanks to @andrewsh:matrix.org
🔗matrix-media-repo v1.0.0 - repeat, v1.0.0!!
TravisR offered:
matrix-media-repo v1.0.0 has been released! If it is suitable for your environment, please give it a go.
🔗Dendrite federation work!
Neil Alexander announced:
Federation fixes have been pushed to
gomatrixserverliband Dendrite'smasterbranches, that include the following tweaks:
- Using the
v2endpoints for/send_joinand/send_leave- Fixing the resolution of room aliases to room IDs in the Dendrite federation API
- A rewrite of the auth chain functions which should be a bit smoother
- A couple of other minor tweaks to some of the types
In addition, I've spent the last few days working on Dendrite's storage backends, adding somewhat-hacky support for SQLite and investigating ORM modelling for some of the simpler components, as a part of getting Dendrite to run as a "true monolith" for the P2P work.
🔗cortex (synapse worker in Rust) supports e2ee rooms
Black Hat offered:
cortex's federation sender finally supports e2ee rooms! I'm testing its performance on an Intel Atom z8350 and it looks great.
🔗Dept of Bridges 🌉
🔗Matrix App for Zapier
@coppero1237 appeared to us, then announced:
The MVP is now available: https://zapier.com/developer/public-invite/77712/033209ffe96c0c0cdd618c8071355c01/
Use the Zapier App to integrate your Matrix room with any of Zapier's 1500+ apps, including:
- Github
- Trello
- Pagerduty
- Google calendar
- Jira
- Salesforce
Currently the MVP supports sending messages to a room. Reading messages from a room is future work.
If you're interested providing feedback, requesting a feature, future development, or just understanding how it works, please join the matrix room, #zapier:matrix.org
Source code: https://github.com/tyleradams/Zapier-Matrix
🔗matrix-zammad bridge
Half-Shot offered:
matrix-zammad now supports reacting to tickets to close them, provided you've set up your puppeted token in the config. It's useful if you get a lot of spam tickets :p
🔗mx-puppet-bridge
sorunome reported:
Lots of changes in mx-puppet-bridge!
- Allow sending status messages into bridged rooms
- add a bridgeChannel function for protocol implementations
- add config options to set displayname and avatar url of the AS bot
- leave the bridge bot of a bridged room, whenever possible
- auto-leave a puppeted ghost after an hour inactivity (to prevent DMs having three users in them)
- automatically dedupe media when uploading
- matrix group to remote protocol group mapping
🔗mx-puppet-discord
Along with mx-puppet-bridge, things got implemented in mx-puppet-discord!
- allow bridging of single channels in a guild
- display an error if sending a message to discord fails
- add
joinentireguildcommand- handle webhooks properly
- map discord guilds to matrix groups
If you enjoy this software, please consider to donate, thank you! 🦊
And another mx-puppet-discord update!
- [User Tokens] Proper User-Agent spoofing - friends management now seems mostly safe! Leaving the warning thing in just-in-case, though
🔗Dept of Clients 📱
🔗📽️ Matrix Presents!
I'm adding this to the client section because it behaves like a client, but it's not what we'd normally think of...
Half-Shot reported:
Work has resumed on matrix-presents, newly rewritten in Vue.js! The project was first demoed back in Oggcamp 2018 where I gave a meta presentation on the virtues Matrix for other mediums. This time around, it's being brought back with:
- A user interface for managing, joining and creating slideshows.
- Control over how slides are advanced (pinned to the presenters view, or unlocked)
- Finer control over how slides are laid out, using a fragments system to build slides out of submessages.
This is currently in heavy development and will debut at Fosdem 2020!
A regularly updated version of the app is hosted at https://presents.half-shot.uk/.
(And for those of you expecting a form of table tennis, there is an easter egg in progress 😃)
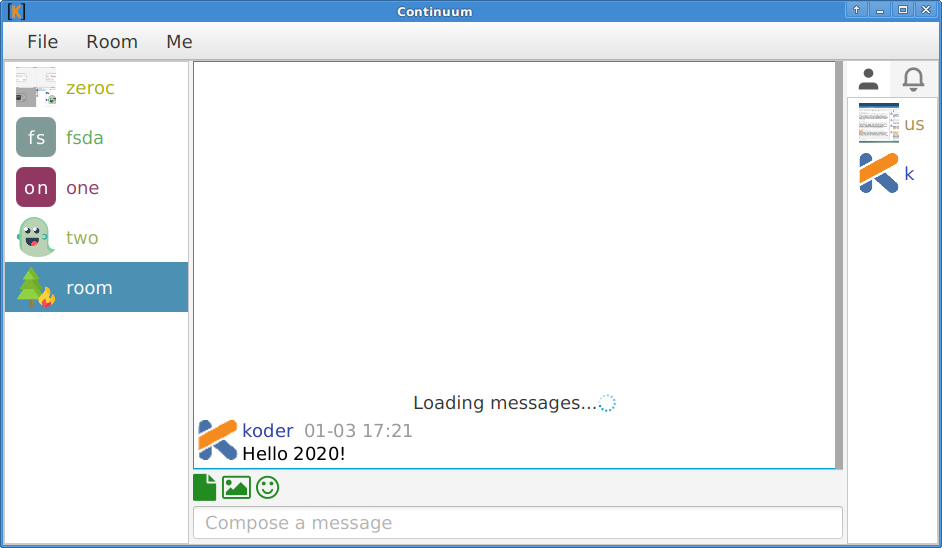
🔗Continuum, desktop client in Kotlin
yuforia offered:
Continuum, a desktop client in Kotlin:
- Update README to include information on building from source
- Fix: database not updated after leaving a room
- Move user's access token and list of joined rooms from database to more lightweight key-value storage
🔗RiotX v0.12.0
benoit reported:
RiotX v0.12.0 has been released with some performance improvement, especially on initial sync and on timeline loading time. The release also contains bugfixes and a cleanup in the application settings. A new "developer mode" has been added to show advanced features only to power users. We are now working on the room profile screen, and we are making progress on the cross-signing implementation. Besides that, we are working to make RiotX available on the F-Droid store.
I must say RiotX is getting a lot more stable and reliable recently!
🔗Riot iOS
Manu told us:
We are still working on the implementation of cross-signing and verification by DM.
🔗Dept of Ops 🛠
🔗K8s
In addition to mentioning Synapse 1.8.0 support, Ananace said:
Synapse 1.8.0 Kubernetes-optimized images are pushed, I've also updated the example manifests as part of some work on making it easier to deploy - expect a MVP of a Helm Chart some time Soon™
Also, to add a bit of context/information to this;
Helm is the de-facto standard package manager for Kubernetes clusters, where a Chart is a package for an application that can be installed and configured. The Helm Chart I'm working on won't be a one-click install to begin with, for the Minimum Viable Product it will require manually generating and storing the Synapse signing key - though I have thoughts on how to later delegate that to a small one-time job that Helm can run if necessary
🔗Opsdroid 0.17
Cadair offered:
Opsdroid 0.17 was released in December, it comes with many changes but the main matrix improvements are support for extra event types like Replies, Edits, Reactions, Room Name changes, Room Topic changes, Alias changes, Room avatar changes, Power levels, and support for generic matrix state events. All these events are supported for both sending and implementing skills based on receiving them.
🔗Dept of Ping 🏓
Let's reveal, rank, and applaud the homeservers with the lowest ping, as measured by pingbot, a maubot that you can host on your own server. Join #ping:maunium.net to experience the fun live, and to find out how to add YOUR server to the game.
| Rank | Hostname | Median MS |
|---|---|---|
| 1 | getflexedon.me | 180.5 |
| 2 | maclemon.at | 278 |
| 3 | im.leptonics.com | 299 |
| 4 | maunium.net | 327 |
| 5 | lkas.cc | 339.5 |
| 6 | services.pyrahex.com | 351 |
| 7 | tx0.co | 361 |
| 8 | matrix.vgorcum.com | 381 |
| 9 | nerdsin.space | 406 |
| 10 | neko.dev | 442.5 |
🔗That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!